题目
链接:https://pan.baidu.com/s/1yt4LNXsk6kdfnaVjT4AsNQ
提取码:py32
ViolentScript.apk
做法一
AndroidKiller搜索flag{定位主函数
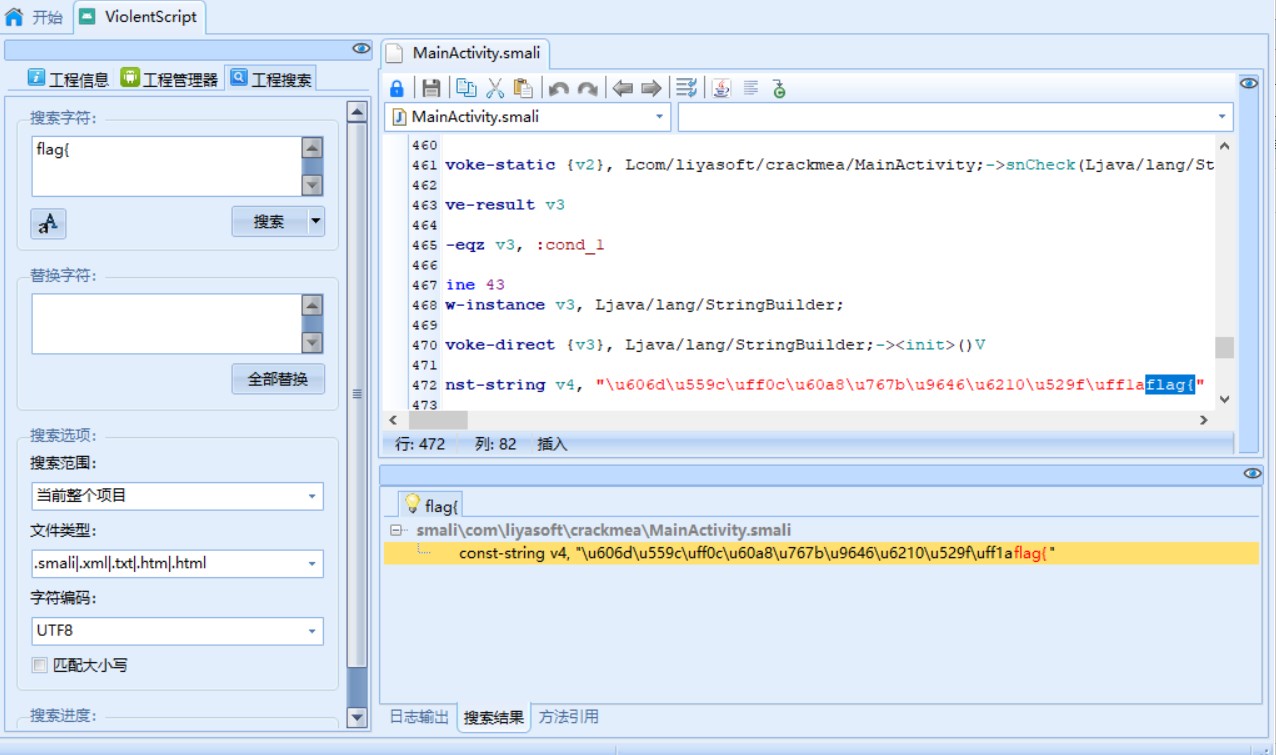
一般题目字符串中没有flag时 从smali->com中找
apk中original存放的是配置信息,res存放资源文件(图片视频之类),smali存放字节码文件,其中Android和Androidx为安卓库文件,com中存放的是用户自定义的包
查看java源码
package com.liyasoft.crackmea;
import android.content.DialogInterface;
import android.content.DialogInterface.OnClickListener;
import android.os.Bundle;
import android.support.v7.app.AlertDialog.Builder;
import android.support.v7.app.AppCompatActivity;
import android.view.View;
import android.view.View.OnClickListener;
import android.widget.Button;
import android.widget.EditText;
import java.security.MessageDigest;
import java.security.NoSuchAlgorithmException;
public class MainActivity
extends AppCompatActivity
implements View.OnClickListener
{
private static int[] mask = { 23, 1, 0, 1, 10, 17, 7, 90, 20 };
private Button mButton;
private EditText mPassword;
private EditText mUsername;
private static boolean checkUsername(String paramString)
{
boolean bool1 = true;
int i = paramString.length();
int j = 0;
if (i == 9)
{
boolean bool2;
for (;;)
{
bool2 = bool1;
if (j >= 9) {
break;
}
if ((paramString.charAt(j) ^ "miaomiao!".charAt(j)) != mask[j])
{
bool2 = false;
break;
}
j++;
}
return bool2;
}
return false;
}
private static String getString(byte[] paramArrayOfByte)
{
StringBuilder localStringBuilder = new StringBuilder();
for (int i = 0; i < paramArrayOfByte.length; i++) {
localStringBuilder.append(paramArrayOfByte[i]);
}
return localStringBuilder.toString();
}
public static String hash(String paramString)
{
try
{
paramString = MessageDigest.getInstance("MD5").digest(paramString.getBytes());
StringBuilder localStringBuilder = new java/lang/StringBuilder;
localStringBuilder.<init>(40);
int i = paramString.length;
for (int j = 0; j < i; j++)
{
int k = paramString[j];
if ((k & 0xFF) >> 4 == 0)
{
localStringBuilder.append("0");
localStringBuilder.append(Integer.toHexString(k & 0xFF));
}
else
{
localStringBuilder.append(Integer.toHexString(k & 0xFF));
}
}
paramString = localStringBuilder.toString();
return paramString;
}
catch (NoSuchAlgorithmException paramString) {}
return null;
}
private void initView()
{
this.mButton = ((Button)findViewById(2131230814));
this.mUsername = ((EditText)findViewById(2131230915));
this.mPassword = ((EditText)findViewById(2131230835));
this.mButton.setOnClickListener(this);
}
private static boolean snCheck(String paramString)
{
if (paramString.length() != 32) {
return false;
}
if ((paramString.toLowerCase().startsWith("27a3c22d01eb")) && (paramString.toLowerCase().endsWith("6ee8866aa5e5e7820"))) {
try
{
boolean bool = hash(paramString).equalsIgnoreCase("271373f323d9f76dc31204ff19823fdf");
return bool;
}
catch (Exception paramString)
{
return false;
}
}
return false;
}
public void onClick(View paramView)
{
if (paramView.getId() == 2131230814)
{
AlertDialog.Builder localBuilder = new AlertDialog.Builder(this);
Object localObject = this.mUsername.getText().toString();
paramView = this.mPassword.getText().toString();
if ((checkUsername((String)localObject)) && (snCheck(paramView)))
{
localObject = new StringBuilder();
((StringBuilder)localObject).append("恭喜,您登陆成功:flag{");
((StringBuilder)localObject).append(paramView);
((StringBuilder)localObject).append("}");
localBuilder.setMessage(((StringBuilder)localObject).toString());
localBuilder.setNegativeButton("确定", new DialogInterface.OnClickListener()
{
public void onClick(DialogInterface paramAnonymousDialogInterface, int paramAnonymousInt)
{
paramAnonymousDialogInterface.dismiss();
}
});
}
else
{
localBuilder.setMessage("用户名或密码不正确 密码就是答案哦!");
localBuilder.setNegativeButton("确定", new DialogInterface.OnClickListener()
{
public void onClick(DialogInterface paramAnonymousDialogInterface, int paramAnonymousInt)
{
paramAnonymousDialogInterface.dismiss();
}
});
}
localBuilder.show();
}
}
protected void onCreate(Bundle paramBundle)
{
super.onCreate(paramBundle);
setContentView(2131427356);
initView();
}
}
根据提示密码就是flag,所以着重看snCheck
if (paramString.length() != 32) {
return false;
}
if ((paramString.toLowerCase().startsWith("27a3c22d01eb")) && (paramString.toLowerCase().endsWith("6ee8866aa5e5e7820"))) {
try
{
boolean bool = hash(paramString).equalsIgnoreCase("271373f323d9f76dc31204ff19823fdf");
return bool;
}
也就是paramString以27a3c22d01eb开头,6ee8866aa5e5e7820结尾,且长度为32位,还有中间3位需要爆破
爆破脚本如下
python:
import hashlib
nums1 = ["27a3c22d01eb"]
nums2 = [0]*3
nums3 = ["6ee8866aa5e5e7820"]
str = "271373f323d9f76dc31204ff19823fdf"
str2 = "0123456789abcdefjhigklmnopqrstuvwxyz"
def computeMD5(message):
m = hashlib.md5()
m.update(message.encode(encoding='utf-8'))
return m.hexdigest()
def check():
for i in str2:
for j in str2:
for k in str2:
nums2[0] = i
nums2[1] = j
nums2[2] = k
nums4 = nums1 + nums2 + nums3
if computeMD5(''.join('%s' %id for id in nums4)) == str:
print( ''.join(nums4) )
return
check()
java:
t.charAt(i)是提取t中第i个位置的字符
public static void main(String[] args) {
String t = "0123456789abcdefghijklmnopqrstuvwxyz";
String flagA = "27a3c22d01eb";
String flagB = "6ee8866aa5e5e7820";
for (int i = 0; i < t.length(); i++) {
char x = t.charAt(i);
for (int j = 0; j < t.length(); j++) {
char y = t.charAt(j);
for (int k = 0; k < t.length(); k++) {
char z = t.charAt(k);
String flag = flagA + x + y + z + flagB;
if ("271373f323d9f76dc31204ff19823fdf".equals(MD5Utils.stringToMD5(flag))){
System.out.println("flag: "+flag);
}
}
}
}
}
做法二
直接把271373f323d9f76dc31204ff19823fdf进行md5解密,得到wgwl$5000!
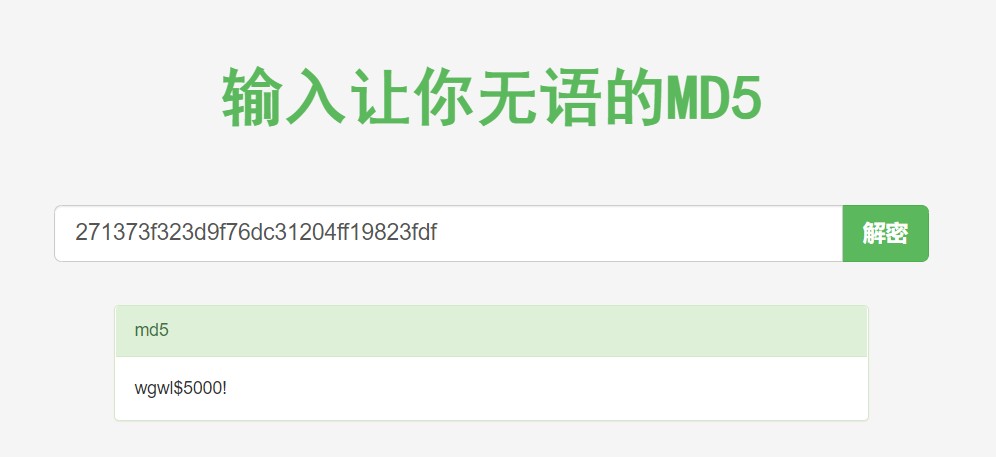
然后再将wgwl$5000! md5加密得到27a3c22d01eb0466ee8866aa5e5e7820
这里强推网站https://www.somd5.com/
可以自动解两层md5
Reverse02
做法一
一个exe,看一下界面
到md5都是可读的,需要的就是后面的部分
查壳

查找字符串
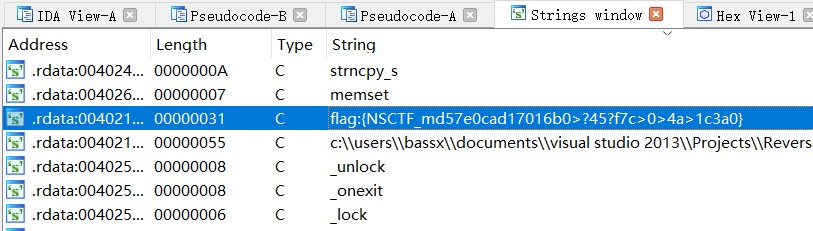
发现两个函数
这里是表明在文本框中输入什么才会弹出flag提示框
int v1; // edx
int v2; // esi
int result; // eax
if ( ((unsigned __int8)a13 ^ 7) == *this
&& ((unsigned __int8)a12 ^ 7) == this[1]
&& ((unsigned __int8)a11 ^ 7) == this[2]
&& ((unsigned __int8)a10 ^ 7) == this[3]
&& ((unsigned __int8)a9 ^ 7) == this[4]
&& ((unsigned __int8)a8 ^ 7) == this[5]
&& ((unsigned __int8)a7 ^ 7) == this[6] )
{
v1 = dword_403380 + 2;
v2 = dword_403018 - 1;
dword_403380 += 2;
--dword_403018;
}
else
{
v1 = dword_403380;
v2 = dword_403018;
}
if ( ((unsigned __int8)a6 ^ 0x33) == this[7]
&& ((unsigned __int8)a5 ^ 0x33) == this[8]
&& ((unsigned __int8)a4 ^ 0x33) == this[9]
&& ((unsigned __int8)a3 ^ 0x33) == this[10]
&& ((unsigned __int8)a2 ^ 0x33) == this[11]
&& ((unsigned __int8)a1 ^ 0x33) == this[12] )
{
--v1;
v2 += 2;
dword_403380 = v1;
dword_403018 = v2;
}
if ( v2 + v1 == 3 )
result = sub_401000();
else
result = MessageBoxA(0, "flag:{NSCTF_md57e0cad17016b0>?45?f7c>0>4a>1c3a0}", "Flag", 0);
dword_403018 = 1;
dword_403380 = 0;
return result;
}
这里是flag加密原理
int sub_401000()
{
char *i; // eax
char Destination; // [esp+0h] [ebp-38h] BYREF
char v3[51]; // [esp+1h] [ebp-37h] BYREF
Destination = 0;
memset(v3, 0, 0x30u);
strncpy_s(&Destination, 0x31u, "flag:{NSCTF_md57e0cad17016b0>?45?f7c>0>4a>1c3a0}", 0x30u);
for ( i = &v3[14]; *i != 125; ++i )
*i ^= 7u;
return MessageBoxA(0, &Destination, "Flag", 0);
实际上按照这个^7就可以了
#include <stdio.h>
main(){
char a[33] = "7e0cad17016b0>?45?f7c>0>4a>1c3a0";
int i;
for (i=0;i<32;i++){
printf("%c",a[i] ^ 7);
}
}
得到0b7dfc60761e798328a0d9793f96d4f7
可以获取输入验证一下
#include <stdio.h>
main(){
char a[] ={0x4A, 0x50, 0x46, 0x6A, 0x58, 0x6A, 0x32, 0x3B, 0x39, 0x47, 0x57, 0x62, 0x4E};
int i;
for (i=12;i>=6;i--){
printf("%c",a[i] ^ 7);
}
for (i=5;i>=0;i--){
printf("%c",a[i] ^ 0x33);
}
}
得到输入为IeP@><5YkYucy

做法二
摁下按钮,flag弹框出现,可以选择用破解,将输入判定nop掉
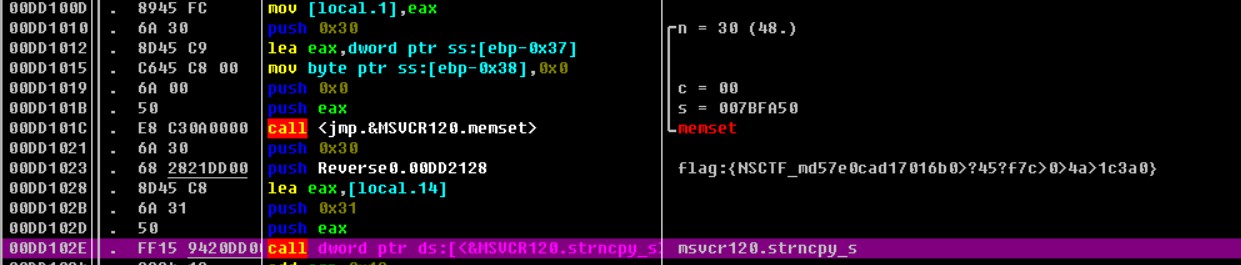
od打开,先查字符串,两个flag{

区分一下
第一个下面先调用了strncpy,后调用了message,所以是输出正确flag的函数
第二个只调用了message,是检验输入的函数
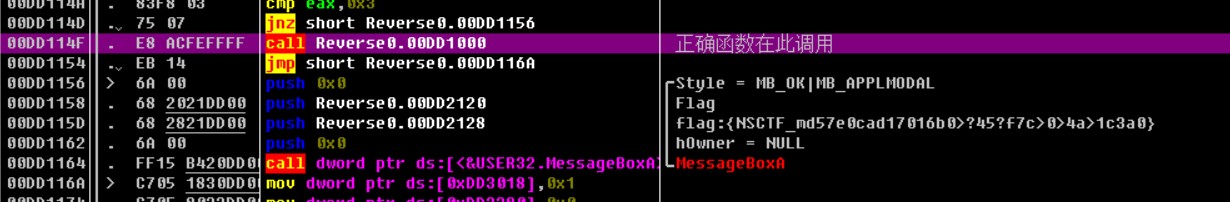
这里只要把调用第一个函数的判断条件nop掉,即可直接输出
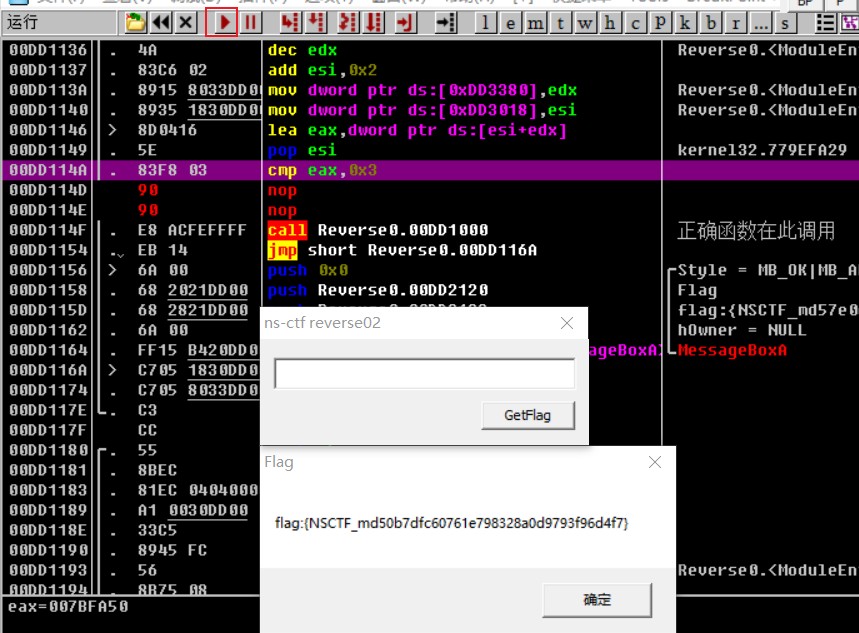
直接运行
re
主函数为

有两个key
key1
dwfsxe *__fastcall key1(dwfsxe *this)
{
int i; // [rsp+14h] [rbp-2Ch]
unsigned __int64 v3; // [rsp+18h] [rbp-28h] BYREF
const char *v4; // [rsp+20h] [rbp-20h]
size_t size; // [rsp+28h] [rbp-18h]
char *v6; // [rsp+30h] [rbp-10h]
unsigned __int64 v7; // [rsp+38h] [rbp-8h]
v7 = __readfsqword(0x28u);
v4 = "OFG{OxS3Lha6MUDk[0PnXofmcUrp`E3w`1@zalL2fZX1gJn4SWHFPGTEP2jHQivOVW7RWDDQW3PTTnf[UTmjSAOiHT6oIkerZ{q?";
size = 192LL;
v6 = (char *)malloc(0xC0uLL);
for ( i = 0; i < size; ++i )
v6[i] = v4[i] ^ 2;
*(_QWORD *)this = ohfewfynewnfew(v6, size, &v3);
return (dwfsxe *)(__readfsqword(0x28u) ^ v7);
key1解出来后base64解密为0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!@#$%^&*()_+
key2
handvfiu *__fastcall key2(handvfiu *this)
{
int i; // [rsp+14h] [rbp-2Ch]
unsigned __int64 v3; // [rsp+18h] [rbp-28h] BYREF
const char *v4; // [rsp+20h] [rbp-20h]
size_t size; // [rsp+28h] [rbp-18h]
char *v6; // [rsp+30h] [rbp-10h]
unsigned __int64 v7; // [rsp+38h] [rbp-8h]
v7 = __readfsqword(0x28u);
v4 = "bEBn`GBkMV{fJyMLTF{yR@sQVjUNIoULJVtsN@UQ[d>>";
size = 44LL;
v6 = (char *)malloc(0x2CuLL);
for ( i = 0; i < size; ++i )
v6[i] = v4[i] ^ 3;
*(_QWORD *)this = ohfewfynewnfew(v6, size, &v3);
return (handvfiu *)(__readfsqword(0x28u) ^ v7);
}
key2解出来是hP&p0!5L#3NXLs@*QR%L&UN!L)0%Q
check函数
__int64 __fastcall check(B *this, dwfsxe *a2, handvfiu *a3)
{
int i; // [rsp+2Ch] [rbp-14h]
if ( strlen(*(const char **)this) != 31 )
wrong(this);
for ( i = 0; i < strlen(*(const char **)this); ++i )
{
if ( *(_BYTE *)(*(_QWORD *)a2 + *(char *)(*(_QWORD *)this + i) - 48LL) != *(_BYTE *)(*(_QWORD *)a3 + i) )
closeto(this);
}
return right(this);
}
check函数表明flag31位且a2[this[i] - 48 ] == a3[i],其中this是我们输入的部分
写出脚本
a2 = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!@#$%^&*()_+"
a3 = "hP&p0!5L^#3NXLs@*QR%L&UN!L)0%Q^"
for i in range(len(a3)): #一共循环31次
for j in range(len(a2)):
if a3[i] == a2[j]:
print(chr(j + 48),end="")
flag为ActI0n5_sp3ak_Louder_than_w0rds