/etc/passwd文件解析
(1):用户名。
(2):密码(已经加密)
(3):UID(用户标识),操作系统自己用的
(4):GID组标识。
(5):用户全名或本地帐号
(6):开始目录
(7):登录使用的Shell,就是对登录命令进行解析的工具。
例如:user:password:501:501:user:/home/usr:/bin/bash
/etc/shadow文件解析
如果查看/etc/shadow下存放的普通帐号信息如下:
(1):帐号名称
(2):密码:这里是加密过的,但高手也可以解密的。
(3):上次修改密码的日期
(4):密码不可被变更的天数
(5):密码需要被重新变更的天数(99999表示不需要变更)
(6):密码变更前提前几天警告
(7):帐号失效日期
(8):帐号取消日期
(9):保留条目,目前没用
口令字加密方式
密码由三个部分组成$id$salt$encrypted
/*
* basic crypt functionality
* char *crypt(const char *key, const char *salt);
* key is a user's typed password
* salt is a two-character string chosen from the set [a-zA-Z0-9./]
* On success, a pointer to the encrypted password is returned. On
* error, NULL is returned.
*
* glibc extends crypt()
* salt can be encoded as $id$salt$ (with the last $ optional)
* where salt is up to 16 characters following the $id$
* id | method
* 1 | MD5
* 2a | Blowfish (not always present)
* 5 | SHA-256 (since glibc 2.7)
* 6 | SHA-512 (since glibc 2.7)
* result is then $id$salt$encrypted
*
* since glibc 2.7, the salt can be extended to be
* $id$rounds=yyy$salt$ where 1000 <= yyy <= 999999999
* with the result $id$rounds=yyy$salt$encrypted
* no plan to use this form yet
*/
root:$6$6VH6qXTt$t2BfE3VNOfOC1I7QIGj5rtXcSnwGmTsfGRlxfvs7DP3KmZwZ2ZNU7SmOqDYZx4IK4sSwPyhZ4wrJYFFc8obsw1:0:65015:root:/root:/usr/local/sbin/shell.exe
表示的是使用SHA-512算法加密,salt为6VH6qXTt。
crypt()函数传入password明文和salt值,返回值为password密文。注意,传入的第二个参数为$id$salt$。
验证口令字
当用户登录时,使用getpwnam()获取用户登录相关信息。
struct passwd {
char * pw_name; /* Username. */
char * pw_passwd; /* Password. */
__uid_t -pw_uid; /* User ID. */
__gid_t -pw_gid; /* Group ID. */
char * pw_gecos; /* Real name. */
char * pw_dir; /* Home directory. -*/
char * pw_shell; /* Shell program. */
};
struct passwd* pw;
pw = getpwnam(userName);
result = crypt(password, pw->pw_passwd);
if( strcmp( result, pw->pw_passwd ) == 0 )
pass_verify();
SSH远程登录
root@XXXXX:/# ssh hz@10.244.1.82
The authenticity of host '10.244.1.82 (10.244.1.82)' can't be established.
ECDSA key fingerprint is SHA256:GODQ6c4iwi/zfdSnY/7PnuvAvfFaycP3/olZASQW1Rk.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.244.1.82' (ECDSA) to the list of known hosts.
hz@10.244.1.82's password:
登录过程:
(1)客户端发起连接请求
(2)服务器收到请求并发送公钥
(3)客户端使用服务器公钥加密密码并送给服务器
(4)服务器使用私钥解密,获得客户端密码,验证用户名和密码。
安全风险:SSH协议的公钥没有证书中心(CA)公证。中间人攻击。
中间人攻击过程:
(1)客户端发起连接请求
(2)黑客截获登录请求,冒充服务器,将伪造的公钥发给客户端
(3)登录请求,然后冒充服务器,将伪造的公钥发给客户端
(4)黑客获得密码并使用它登录服务器。
/vob/hz/.ssh/known_hosts存放的是服务器的公钥。下面的提示表示,公钥过期,解决方法是删掉重新连接
hz@XXXXX $ ssh hz@172.0.10.58
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the ECDSA key sent by the remote host is
ce:33:7b:da:2c:06:5e:e3:1c:da:1b:99:f1:7d:c4:de.
Please contact your system administrator.
Add correct host key in /vob/hz/.ssh/known_hosts to get rid of this message.
Offending ECDSA key in /vob/hz/.ssh/known_hosts:3
ECDSA host key for 172.0.10.58 has changed and you have requested strict checking.
Host key verification failed.
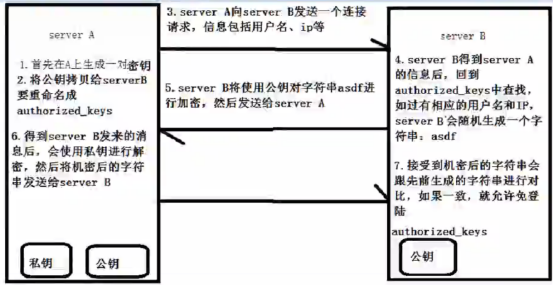
SSH免密登录