实验案例
1、kubernetes对普通用户授权
RBAC是基于角色的访问控制
创建一个kaka用户来管理namespace=dev的dashboard账户
第一步:在指定namespace创建账户kaka
root@k8s-master01:/apps/k8s-yaml/auth-case# kubectl create namespace dev namespace/dev created root@k8s-master01:/apps/k8s-yaml/auth-case# kubectl create serviceaccount kaka -n dev serviceaccount/kaka created
root@k8s-master01:/apps/k8s-yaml/auth-case# kubectl api-resources NAME SHORTNAMES APIVERSION NAMESPACED KIND bindings v1 true Binding componentstatuses cs v1 false ComponentStatus configmaps cm v1 true ConfigMap endpoints ep v1 true Endpoints events ev v1 true Event limitranges limits v1 true LimitRange namespaces ns v1 false Namespace nodes no v1 false Node persistentvolumeclaims pvc v1 true PersistentVolumeClaim persistentvolumes pv v1 false PersistentVolume pods po v1 true Pod podtemplates v1 true PodTemplate replicationcontrollers rc v1 true ReplicationController resourcequotas quota v1 true ResourceQuota secrets v1 true Secret serviceaccounts sa v1 true ServiceAccount services svc v1 true Service mutatingwebhookconfigurations admissionregistration.k8s.io/v1 false MutatingWebhookConfiguration validatingwebhookconfigurations admissionregistration.k8s.io/v1 false ValidatingWebhookConfiguration customresourcedefinitions crd,crds apiextensions.k8s.io/v1 false CustomResourceDefinition apiservices apiregistration.k8s.io/v1 false APIService controllerrevisions apps/v1 true ControllerRevision daemonsets ds apps/v1 true DaemonSet deployments deploy apps/v1 true Deployment replicasets rs apps/v1 true ReplicaSet statefulsets sts apps/v1 true StatefulSet tokenreviews authentication.k8s.io/v1 false TokenReview localsubjectaccessreviews authorization.k8s.io/v1 true LocalSubjectAccessReview selfsubjectaccessreviews authorization.k8s.io/v1 false SelfSubjectAccessReview selfsubjectrulesreviews authorization.k8s.io/v1 false SelfSubjectRulesReview subjectaccessreviews authorization.k8s.io/v1 false SubjectAccessReview horizontalpodautoscalers hpa autoscaling/v1 true HorizontalPodAutoscaler cronjobs cj batch/v1 true CronJob jobs batch/v1 true Job certificatesigningrequests csr certificates.k8s.io/v1 false CertificateSigningRequest leases coordination.k8s.io/v1 true Lease endpointslices discovery.k8s.io/v1 true EndpointSlice events ev events.k8s.io/v1 true Event ingresses ing extensions/v1beta1 true Ingress flowschemas flowcontrol.apiserver.k8s.io/v1beta1 false FlowSchema prioritylevelconfigurations flowcontrol.apiserver.k8s.io/v1beta1 false PriorityLevelConfiguration nodes metrics.k8s.io/v1beta1 false NodeMetrics pods metrics.k8s.io/v1beta1 true PodMetrics ingressclasses networking.k8s.io/v1 false IngressClass ingresses ing networking.k8s.io/v1 true Ingress networkpolicies netpol networking.k8s.io/v1 true NetworkPolicy runtimeclasses node.k8s.io/v1 false RuntimeClass poddisruptionbudgets pdb policy/v1 true PodDisruptionBudget podsecuritypolicies psp policy/v1beta1 false PodSecurityPolicy clusterrolebindings rbac.authorization.k8s.io/v1 false ClusterRoleBinding clusterroles rbac.authorization.k8s.io/v1 false ClusterRole rolebindings rbac.authorization.k8s.io/v1 true RoleBinding roles rbac.authorization.k8s.io/v1 true Role priorityclasses pc scheduling.k8s.io/v1 false PriorityClass csidrivers storage.k8s.io/v1 false CSIDriver csinodes storage.k8s.io/v1 false CSINode csistoragecapacities storage.k8s.io/v1beta1 true CSIStorageCapacity storageclasses sc storage.k8s.io/v1 false StorageClass volumeattachments storage.k8s.io/v1 false VolumeAttachment
kaka-role.yaml
cat >> kaka-role.yaml << EOF kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: namespace: dev name: kaka-role rules: - apiGroups: ["*"] #资源的版本信息,"*"表示所有版本 resources: ["pods","pods/exec"] #资源信息,pods表示pod资源,pods/exec表示可以进入pod执行命令 verbs: ["*"] #做什么操作,"*"表示所有操作 ##RO-Role #verbs: ["get", "watch", "list"] - apiGroups: ["extensions", "apps/v1"] resources: ["deployments"] verbs: ["get", "list", "watch", "create", "update", "patch", "delete"] ##RO-Role #verbs: ["get", "watch", "list"] EOF root@k8s-master01:/apps/k8s-yaml/auth-case# kubectl apply -f kaka-role.yaml role.rbac.authorization.k8s.io/kaka-role created
cat >> kaka-role-bind.yaml << EOF kind: RoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: role-bind-kaka namespace: dev subjects: - kind: ServiceAccount name: kaka namespace: dev roleRef: kind: Role name: kaka-role apiGroup: rbac.authorization.k8s.io EOF root@k8s-master01:/apps/k8s-yaml/auth-case# kubectl apply -f kaka-role-bind.yaml rolebinding.rbac.authorization.k8s.io/role-bind-kaka created
root@k8s-master01:/apps/k8s-yaml/auth-case# kubectl get secrets -n dev | grep kaka kaka-token-mpbwh kubernetes.io/service-account-token 3 17m #root@k8s-master01:/apps/k8s-yaml/auth-case# kubectl get secret kaka-token-mpbwh -o jsonpath={.data.token} -n dev |base64 -d root@k8s-master01:/apps/k8s-yaml/auth-case# kubectl describe secrets kaka-token-mpbwh -n dev Name: kaka-token-mpbwh Namespace: dev Labels: <none> Annotations: kubernetes.io/service-account.name: kaka kubernetes.io/service-account.uid: 632d6a30-aa82-4145-9504-f0343f6a71f4 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1350 bytes namespace: 3 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6InYyWDRVcktKczh1WVJBWUlXcWFZQVdWV1l4a2FwMXRGRURrMGV2RUxmaUUifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZXYiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlY3JldC5uYW1lIjoia2FrYS10b2tlbi1tcGJ3aCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrYWthIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNjMyZDZhMzAtYWE4Mi00MTQ1LTk1MDQtZjAzNDNmNmE3MWY0Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmRldjprYWthIn0.AL3k4uILRID6eF3Fp2UVrYT7CpaGxX97kJVJeggZdOyqnawTRpg5fmvGkdjm7TmtoKqhzAFYY5cjKe9YD_m8MxXW1YT7-4sFGuuAjLGzHEKcR3kctzUttOSu0SExHEFGAlsciOvq_TfruAoV4k1vG_5TbN9_BJ6bJTppQ8lI4zjToXM3asmGh_OM-wrV97p-YGSBnWnNQqZ6Mz3Vsw4gTwz7Y1z3q9v5FSByWRnSyoZJZaqI9TaBc3jAJg0DHJ4VFPvO8kdWv9_2eqwQ-VGGcdxCK3VDbtIIs98fj_G_G3Vw6zu4EcNV5BLXYX3Lb8rtiJnvml_GkUmoI_5DF7QOCg
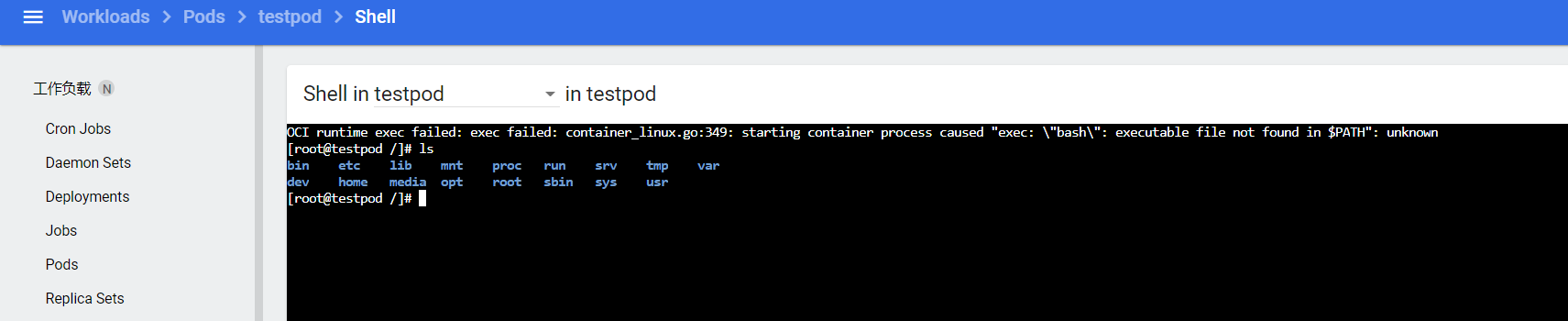
原因是kaka用户无获取pods/exec的权限
基于kube-config文件登录
第六步到第八步在kubernetes的kubeasz部署机上操作,本实验为172.168.33.201
第九步及其之后是在k8s-master01上操作,本实验为172.168.33.207
第六步:创建csr文件
root@harbor:/apps/certs# pwd /apps/certs root@harbor:/apps/certs# cat >> kaka-csr.json << EOF { "CN": "China", "hosts": [], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "BeiJing", "L": "BeiJing", "O": "k8s", "OU": "System" } ] } EOF
#安装cfssl命令 root@harbor:/etc/kubeasz# apt install golang-cfssl -y #生成证书 root@harbor:/etc/kubeasz# cfssl gencert -ca=/etc/kubeasz/clusters/k8s-ywx/ssl/ca.pem -ca-key=//etc/kubeasz/clusters/k8s-ywx/ssl/ca-key.pem -config=/etc/kubeasz/clusters/k8s-ywx/ssl/ca-config.json -profile=kubernetes kaka-csr.json | cfssljson -bare kaka root@harbor:/apps/certs# ls kaka-csr.json kaka-key.pem kaka.csr kaka.pem
root@harbor:/apps/certs# scp -r ./* 172.168.33.207:/etc/kubernetes/ssl/ kaka-csr.json 100% 218 230.1KB/s 00:00 kaka-key.pem 100% 1679 2.8MB/s 00:00 kaka.csr 100% 993 1.2MB/s 00:00 kaka.pem 100% 1383 2.3MB/s 00:00
root@k8s-master01:/etc/kubernetes/ssl# kubectl config set-cluster k8s-ywx --certificate-authority=/etc/kubernetes/ssl/ca.pem --embed-certs=true --server=https://172.168.33.50:6443 --kubeconfig=kaka.kubeconfig #--embed-certs=true 为嵌入证书信息
root@k8s-master01:/etc/kubernetes/ssl# kubectl config set-credentials kaka --client-certificate=/etc/kubernetes/ssl/kaka.pem --client-key=/etc/kubernetes/ssl/kaka-key.pem --embed-certs=true --kubeconfig=kaka.kubeconfig
https://kubernetes.io/zh/docs/concepts/configuration/organize-cluster-access-kubeconfig/
root@k8s-master01:/etc/kubernetes/ssl# kubectl config set-context k8s-ywx --cluster=k8s-ywx --user=kaka --namespace=dev --kubeconfig=kaka.kubeconfig
root@k8s-master01:/etc/kubernetes/ssl# kubectl config use-context k8s-ywx --kubeconfig=kaka.kubeconfig
root@k8s-master01:/etc/kubernetes/ssl# vim kaka.kubeconfig name: k8s-ywx contexts: - context: cluster: k8s-ywx namespace: dev user: kaka name: k8s-ywx current-context: k8s-ywx kind: Config preferences: {} users: - name: kaka user: client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUQwRENDQXJpZ0F3SUJBZ0lVQ09naVNmSkMvb1BITkFWY2liTFpValBoYkVzd0RRWUpLb1pJaHZjTkFRRUwKQlFBd1lURUxNQWtHQTFVRUJoTUNRMDR4RVRBUEJnTlZCQWdUQ0VoaGJtZGFhRzkxTVFzd0NRWURWUVFIRXdKWQpVekVNTUFvR0ExVUVDaE1EYXpoek1ROHdEUVlEVlFRTEV3WlRlWE4wWlcweEV6QVJCZ05WQkFNVENtdDFZbVZ5CmJtVjBaWE13SUJjTk1qRXhNVEF4TVRVd09EQXdXaGdQTWpBM01URXdNakF4TlRBNE1EQmFNR0F4Q3pBSkJnTlYKQkFZVEFrTk9NUkF3RGdZRFZRUUlFd2RDWldsS2FXNW5NUkF3RGdZRFZRUUhFd2RDWldsS2FXNW5NUXd3Q2dZRApWUVFLRXdOck9ITXhEekFOQmdOVkJBc1RCbE41YzNSbGJURU9NQXdHQTFVRUF4TUZRMmhwYm1Fd2dnRWlNQTBHCkNTcUdTSWIzRFFFQkFRVUFBNElCRHdBd2dnRUtBb0lCQVFETVZMQVJZMHJmREVuWWJ0N05ONUNrR3VxVWhBSGgKRnhkRHBLVWRsS3dQeXdNZWZFcEN6UVgyb05YSmpvMXJBa09DNHdaYVgzZnJaRjVnTENUNTVyaWVZc0N1MVlzVwoySVFOeGdqRHU3YWw2NE44MElZdUpZU09XOFk5ZFQwY0h3OFdjRWgzNW5ZWDg5dU9RT00wVkRaSUtRV1g2SFhSCnZjMVhkVm9WMDIvZXZDbzZ1cXZJNFBxUXJDbjdSYkhDRVZUWDBLQXdIVUJidzlkMDFwZ01tSllmU1ExU1BGTjUKR25pc1BKRktzeXVUY2IyeE5rTVRWSEUvK3RVZTV1elVsb0xpRWNFK2hDcjVBaUI3UEpJcnBsODlOUlhCZXRSNwpBblA0N1UrNDlSOWZDZDRoYStreWhNN1gzaEI3cEk1bjQ0V3ZPOXNwakRuM3NNZFlUMGN4RllDZEFnTUJBQUdqCmZ6QjlNQTRHQTFVZER3RUIvd1FFQXdJRm9EQWRCZ05WSFNVRUZqQVVCZ2dyQmdFRkJRY0RBUVlJS3dZQkJRVUgKQXdJd0RBWURWUjBUQVFIL0JBSXdBREFkQmdOVkhRNEVGZ1FVSlVETVlWRGNkL2RZc3FTR1VZNmRHTFBZSlNndwpId1lEVlIwakJCZ3dGb0FVWE5RTHROY2ljSVRMNjlqbUlVRU9QR0dMWStBd0RRWUpLb1pJaHZjTkFRRUxCUUFECmdnRUJBSXovUGFGcG01UFFqb2VIaXJBaWFvZ0ZFT1NvanN0ZkxPMmtVMlB1WTF5a2ZwNXgxK3VrUG8rWFJjdUcKYnFUN2x4WkNkZ1BDWEV5TENqMHU5NjJ5TUdlOUdaSGp1c0VmSnJRdGg3TXpKNnJ6ak1lMlVWMXUyTnoyYndiKwovRGIvd1BHNHN2WXpMZW9yNjFLaDNwNXdPYWJLR1QxemJTQ1cvTWFja0s1L0ZkQXdqU3IrL2pWSXIyb1RkUkF3CnRCWVBySkN3WURFdjBxaEtrbjlqZ0ZXN3c0NTVZU052L2hrYkdaaDJ2d2IwL1htQ2VoTXRCc1RlU0J1QUkvME0KNzNqZ3pidVp3T203Sk5pTkV6dWd2NFVmLzlSa3VBZHU3dnN5dVZiaHFyMVpsamRXdG5sMThyQityMmI4NDl1Two0RFFIblJhS3Qwejc3eXJYd2tzSHdrUjNjYVk9Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcEFJQkFBS0NBUUVBekZTd0VXTkszd3hKMkc3ZXpUZVFwQnJxbElRQjRSY1hRNlNsSFpTc0Q4c0RIbnhLClFzMEY5cURWeVk2TmF3SkRndU1HV2w5MzYyUmVZQ3drK2VhNG5tTEFydFdMRnRpRURjWUl3N3UycGV1RGZOQ0cKTGlXRWpsdkdQWFU5SEI4UEZuQklkK1oyRi9QYmprRGpORlEyU0NrRmwraDEwYjNOVjNWYUZkTnYzcndxT3Jxcgp5T0Q2a0t3cCswV3h3aEZVMTlDZ01CMUFXOFBYZE5hWURKaVdIMGtOVWp4VGVScDRyRHlSU3JNcmszRzlzVFpECkUxUnhQL3JWSHViczFKYUM0aEhCUG9RcStRSWdlenlTSzZaZlBUVVZ3WHJVZXdKeitPMVB1UFVmWHduZUlXdnAKTW9UTzE5NFFlNlNPWitPRnJ6dmJLWXc1OTdESFdFOUhNUldBblFJREFRQUJBb0lCQVFDaGxHSzdEVXJhd1V2dwpGQlNxTWNOMmtqWm9oVTg3SVZoclRGcXAzclNGdEtOZHl5bXFVNWpnbytVTGcyZi9kQVhSRGhnckJRMitubHNuCk1DRjVZT01qbExJTVQ1K3l6RHI0N1Y1bThoMEliZ3BIZkZwdlNZbmVUV0toblFGYktKQjB6UXZ4ak5SY01xR3YKaDA1a1JpZTZ2bjNHMTdPN3paMEJDVExZeVovUWdJL0p3RUVGLzAzU3d2ZllPSDNtYlZiRG9vajY4bVVBUXJQSQorV1RsTlJGUVB3eTZrd0dTOEUxZXVMUTRMRVY0NC9MRDRJUGJUcmdPUmV0VmpZNFNsa0Q2TUlzQnprVUZYZ3VsCkR1cGNVcXZSbkkrdUFVUjZpcEhFam1yd3drSElySkh6UUJOZ0grNnBUU2VQVVdGL2JSUWN6blFmdVdmMDZaZDIKOVBBS3NTNmRBb0dCQU5xb3VZcjZ0OTA1NkJVZDBSclVCS0xvK2V2MkhGaHloaGJYQ3hHWDE2RXFKZm44bm5sTwpDNml3UWF5WlpiNTdGemJXZGdxSEhPaTJOWmpHUk1jMURmTkdOenI5aG9LRzhEMGhxMW1uTktXRzdMK2h1U0tCCjh2VEMzeU1ENVJLV0swdGplWDl4aFlZTDJNbWtQZ3NlTS8yZDVMcWMyMnZBYUczRnlLQlZScTFIQW9HQkFPODUKa0ZUSTJBZkJ6aXVhQUl6cTRjN0FWYm15aDhlZDlpNU1raFVEU3o4RVZ2RklNUnFkNHdLMXdJQmM2UUQ0SHJmMAp1M2hmM1k0T1REMWNpVXJRUUltUGQ1c2ZWSktvaWlVaG9KaVMxK003MkdMMFlGMnEvNHBIeUhWTG1WNzJPK0JLCmppMjB0ZTBKTWR6M2FqazFSYUJwUVJ4NmR5a3FCWkYyWGlHbGg0VDdBb0dBYnVTRS9PUDhYWGpocDl2d1VZL1gKTGh2RHJCU3IrWHRUWDcvOXdCVm02VGhyL0NWTzVheGNJMWdJWnBXQlVTSXgrc0MzS3MydExxUkIrRklOVFk0dApuZ1F0UElDWk9CZGhQVStYRENmTmZtazRKbFBKaGFPcjZNL3Z4RjFVVHFIVUlTNjR6cFp2SmpWWjQ2R2xTWlF1CnY5L1V3WU9Oa0U4TFp5aVlnQi9mY1Q4Q2dZQmdHbWY1SjVaaHgySGo4a0kyV2tYTW9VZlBDZ0d5RjZ0R2ZreFIKVkxsdDMzaHVCZXAwSHVtTHRTaFlhUHJTQU51V1d5TFZBTzRvbTJYVllNOW0xcktXa0tRa0ZUb01rTml1Z2d2YQpQMk9yVGVkb0dYUjlMS3pzQ0ZwbmhLOWdqdHNQQitTR1NBcXQ1dnU1SVV2ekg0dVJIYmVpa1RBOXdUdnJhL24wCjJtTE84UUtCZ1FESnU2S290SjdLWmpHbmx4Q1FYdVBMZlRQN0FNbko0NDQyR0JJVTVETHhhUkt2dkV5dTErQWkKUFRSMmJSQUN1MDVqRlNZT2JvTVdqSFBxYUFMUUo5N1JvTmtXNmJ4c1o0eGlVdEt6WXhNQ2dqQW42OXZldFNSdQpaRUgydy96Q25YNFdIeFFxNWhvY2QrUXpWcmQrREJXM0NVZnZNWkJwcFloMFRBQUF2em9sVVE9PQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo= token: eyJhbGciOiJSUzI1NiIsImtpZCI6InYyWDRVcktKczh1WVJBWUlXcWFZQVdWV1l4a2FwMXRGRURrMGV2RUxmaUUifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZXYiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlY3JldC5uYW1lIjoia2FrYS10b2tlbi1tcGJ3aCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrYWthIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNjMyZDZhMzAtYWE4Mi00MTQ1LTk1MDQtZjAzNDNmNmE3MWY0Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmRldjprYWthIn0.AL3k4uILRID6eF3Fp2UVrYT7CpaGxX97kJVJeggZdOyqnawTRpg5fmvGkdjm7TmtoKqhzAFYY5cjKe9YD_m8MxXW1YT7-4sFGuuAjLGzHEKcR3kctzUttOSu0SExHEFGAlsciOvq_TfruAoV4k1vG_5TbN9_BJ6bJTppQ8lI4zjToXM3asmGh_OM-wrV97p-YGSBnWnNQqZ6Mz3Vsw4gTwz7Y1z3q9v5FSByWRnSyoZJZaqI9TaBc3jAJg0DHJ4VFPvO8kdWv9_2eqwQ-VGGcdxCK3VDbtIIs98fj_G_G3Vw6zu4EcNV5BLXYX3Lb8rtiJnvml_GkUmoI_5DF7QOCg