1、UDP scanning with Scapy
Scapy is a tool that can be used to craft and inject custom packets into a network ,in this specific recipe, Scapy will be used to scan for active UDP services ,This can be done by sending empty UDP packet to destionation ports and then identifying the ports that do not respond with an ICMP port-unreachable response .whether a service is running on a give UDP port ,the technique that we will use with Scapy is to identify closed UDP port with ICMP port-unreachable replies ,to send a UDP request to any given port ,so we need to build layer of taht the request , the first layer that we will need to construct is the IP layer
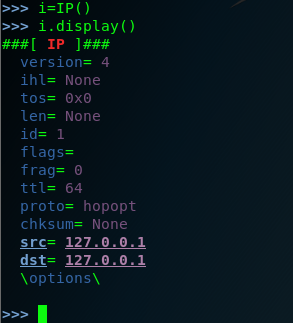
step one : we used the command Scapy to invoking the tool .you don't sent the ip.src ,because the source the ip will automatically updates associated with the default interface . after each setup , you need to check and confirm it by youself . we can you the command (.display) .we should do in lab envrionment , I use the metasploitable2 and , the metasploitable2 system can used as remote service over UDP . so let's see the following option :
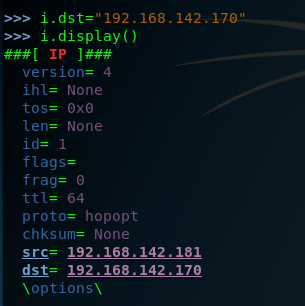
step two : view the metasploitable2 ip address . so the ip.dst=192.168.142.170
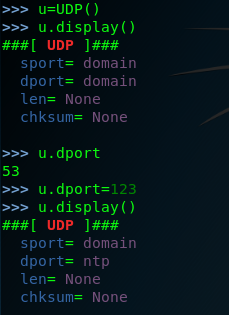
step three :start-up the Scapy and construct the ip layer ,and set the dst ip is 192.168.142.170 . .but hte DNS is a comman service that can often be discovered on network systems , so we can modified by setting the attribute equal to the new port destination value set the dport =123
setp four: we have created both the IP layers ,so here we need to construct the request by the stacking these layers by request=(i/u)
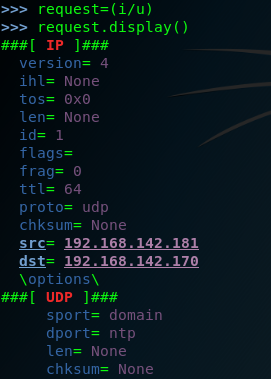
and then send the request to the remote service
finally we can look the response.display ()
>>> response.display()
###[ IP ]###
version= 4
ihl= 5
tos= 0xc0
len= 56
id= 64015
flags=
frag= 0
ttl= 64
proto= icmp
chksum= 0xe144
src= 192.168.142.170
dst= 192.168.142.181
options
###[ ICMP ]###
type= dest-unreach
code= port-unreachable
chksum= 0x9bc7
reserved= 0
length= 0
nexthopmtu= 0
###[ IP in ICMP ]###
version= 4
ihl= 5
tos= 0x0
len= 28
id= 1
flags=
frag= 0
ttl= 64
proto= udp
chksum= 0xdc1f
src= 192.168.142.181
dst= 192.168.142.170
options
###[ UDP in ICMP ]###
sport= domain
dport= ntp
len= 8
chksum= 0x607d
in fact the request can be performed without independently building and stacking each layer ,we can use a single one-line command by calling the function directly and passing them the approprite argument as following . of couse wen scan set the timeout and the verbose .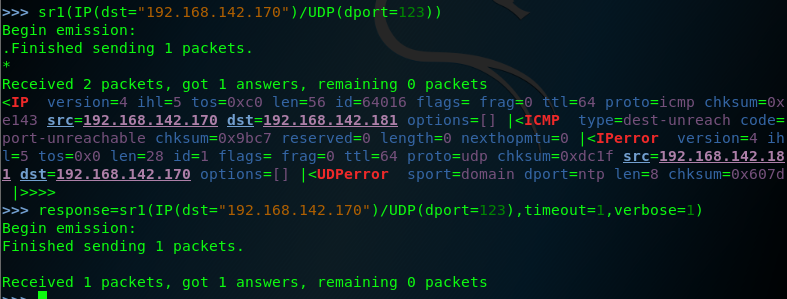
note that the response for these requests includes an ICMP packet that type indicating that the host is unreachable and code indicating that the port is unreachable this response is commonly if the UDP oprt is closed ,so we should attempt to modify the request so that it is sent to the destination port that correspond to an actual service on teh remote system , let's change the destination port back to port 53 and then send the request again .as follows:
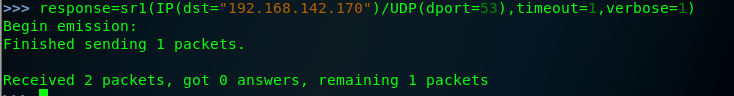
when the same request is sent to an actual aervice ,no replay is received , this is beacuse the DNS service running on the system's UDP port 53, will only respond to service-specific request ,this discrepancy can be used to scan for ICMP host-unreachable replies .
so we can identify potential service by flagging the noresponsive ports. edit a script to scan the port.