1、准备:
系统环境:Centos7.4
软件及版本:
nginx:OpenResty1.13.6.1 ModSecurity:ModSecurity v3.0.0rc1 (Linux) modsecurity connector:ModSecurity-nginx v0.1.1-beta
下载源文件:
mkdir /opt/waf cd /opt/waf #下载openresty wget https://openresty.org/download/openresty-1.13.6.1.tar.gz #下载ModSecurity,附:git安装yum -y install git git clone https://github.com/SpiderLabs/ModSecurity.git cd ModSecurity git checkout v3.0.0 #克隆modsecurity nginx connector
cd /opt/waf git clone --depth 1 https://github.com/SpiderLabs/ModSecurity-nginx.git
2、依赖安装
yum -y install libtool gcc gcc-c++ pcre-devel zlib-devel libxml2-devel libxslt-devel gd-devel perl perl-devel perl-ExtUtils-Embed GeoIP GeoIP-devel GeoIP-data libatomic_ops-devel
#openssl源码安装(如果系统自带,可以不用装)
cd /opt/tools/ wget http://www.openssl.org/source/openssl-1.0.2f.tar.gz tar -zxvf openssl-1.0.2f.tar.gz cd openssl-1.0.2f ./config --prefix=/usr/local/openssl make make install
#GeoIP源码安装(应该可以不用装,yum -y GeoIP-devel已经安装,当时应该是重新configure的时候未clean导致GeoIP动态库没添加到modsecurity的so库依赖)
cd /opt/tools/ mkdir GeoIP cd GeoIP wget http://geolite.maxmind.com/download/geoip/api/c/GeoIP.tar.gz tar -zxvf GeoIP.tar.gz cd GeoIP-1.4.8/ make make install
3、modsecurity编译
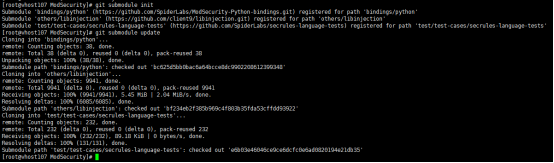
cd /opt/waf/ModSecurity git submodule init git submodule update
出现 以下,说明更新模块成功
./build.sh
#后面的编译参数可以去掉,如果最后链接有问题可以用自己源码安装的 ./configure --with-geoip=/usr/local/GeoIP make make install
注意:make可能会报错,缺少依赖,缺少依赖后安装相关依赖,然后make clean下再重新执行三部曲。
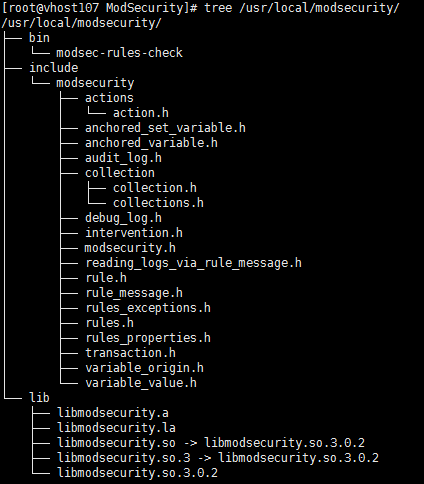
查看
tree /usr/local/modsecurity/
4、openresty编译
cd /opt/waf tar zxvf openresty-1.13.6.1.tar.gz cd openresty-1.13.6.1 ./configure --prefix=/usr/local/nginx --sbin-path=/usr/sbin/nginx --conf-path=/usr/local/nginx/nginx.conf --pid-path=/var/run/nginx.pid --error-log-path=/var/log/nginx/error.log --http-log-path=/var/log/nginx/access.log --lock-path=/var/lock/nginx.lock --with-luajit --with-http_gunzip_module --with-pcre --with-pcre-jit --with-http_perl_module --with-ld-opt="-Wl,-E" --with-http_realip_module --with-http_secure_link_module --with-http_slice_module --with-http_ssl_module --with-http_stub_status_module --with-http_sub_module --with-http_v2_module --with-http_addition_module --with-http_xslt_module --with-http_image_filter_module --with-http_geoip_module --with-http_dav_module --with-http_flv_module --with-http_mp4_module --with-http_gzip_static_module --with-http_auth_request_module --with-http_random_index_module --with-select_module --with-poll_module --with-file-aio --with-http_degradation_module --with-libatomic --http-client-body-temp-path=/var/tmp/nginx/client_body --http-proxy-temp-path=/var/tmp/nginx/proxy --http-fastcgi-temp-path=/var/tmp/nginx/fastcgi --http-uwsgi-temp-path=/var/tmp/nginx/uwsgi --http-scgi-temp-path=/var/tmp/nginx/scgi --add-dynamic-module=/opt/waf/ModSecurity-nginx/ --with-openssl=/opt/tools/openssl-1.0.2f
make
make install
注意:1、--add-dynamic-module=/opt/waf/ModSecurity-nginx/ --with-openssl=/opt/tools/openssl/openssl-1.0.2f/ 这两个路径为自己的安装路径。
2、make可能会报错,缺少依赖,缺少依赖后安装相关依赖,然后make clean下再重新执行三部曲。
5、规则下载
cd /opt/waf git clone https://github.com/SpiderLabs/owasp-modsecurity-crs.git cd owasp-modsecurity-crs/ cp crs-setup.conf.example crs-setup.conf cd rules cp REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf.example REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf cp RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf.example RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf
6、openresty配置添加
cd /usr/local/nginx/
vi nginx.conf 如下
#user nobody; worker_processes 1; #error_log logs/error.log; #modsecurity动态库加载 load_module /usr/local/nginx/nginx/modules/ngx_http_modsecurity_module.so; #error_log logs/error.log notice; #error_log logs/error.log info; #pid logs/nginx.pid; events { worker_connections 1024; } http { include mime.types; default_type application/octet-stream; #log_format main '$remote_addr - $remote_user [$time_local] "$request" ' # '$status $body_bytes_sent "$http_referer" ' # '"$http_user_agent" "$http_x_forwarded_for"'; #access_log logs/access.log main; sendfile on; #tcp_nopush on; #keepalive_timeout 0; keepalive_timeout 65; #gzip on; server { listen 80; server_name localhost; #access_log logs/host.access.log main; #modsecurity 支持 modsecurity on; location / { #modsecurity配置文件路径 modsecurity_rules_file /usr/local/nginx/modsecurity.conf; root html; index index.html index.htm; } location = /50x.html { root html; } } }
添加modsecurity配置
cp /opt/waf/ModSecurity/modsecurity.conf-recommended modsecurity.conf vi modsecurity.conf
最后添加
Include /opt/waf/owasp-modsecurity-crs/crs-setup.conf
Include /opt/waf/owasp-modsecurity-crs/rules/*.conf
保存
测试
nginx -t
发现如下错误
nginx: the configuration file /usr/local/nginx/nginx.conf syntax is ok nginx: [emerg] mkdir() "/var/tmp/nginx/client_body" failed (2: No such file or directory) nginx: configuration file /usr/local/nginx/nginx.conf test failed
mkdir /var/tmp/nginx nginx -t没问题了
启动nginx
nginx
测试
打开modsecurity检测日志
tail -f /var/log/modsec_audit.log
在浏览器访问
http://[your ip or hostname]/?a=<script>alert(aa)</script>
可以看到日志

---v3gm3tZj---A-- [17/Apr/2018:16:53:12 +0800] 152395519294.104760 172.23.11.56 31223 172.23.11.56 80 ---v3gm3tZj---B-- GET /favicon.ico HTTP/1.1 Host: 172.23.26.157 User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/64.0.3282.167 Safari/537.36 Accept: image/webp,image/apng,image/*,*/*;q=0.8 Referer: http://172.23.26.157/?a=%3Cscript%3Ealert(aa)%3C/script%3E Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close ---v3gm3tZj---D-- ---v3gm3tZj---F-- HTTP/1.1 404 Server: openresty/1.13.6.1 Date: Tue, 17 Apr 2018 08:53:12 GMT Content-Length: 577 Content-Type: text/html Connection: close ---v3gm3tZj---H-- ModSecurity: Warning. Matched "Operator `Rx' with parameter `^[d.:]+$' against variable `REQUEST_HEADERS:Host' (Value: `172.23.26.157' ) [file "/opt/waf/owasp-modsecurity-crs/rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf"] [line "733"] [id "920350"] [rev "2"] [msg "Host header is a numeric IP address"] [data "172.23.26.157"] [severity "4"] [ver "OWASP_CRS/3.0.0"] [maturity "9"] [accuracy "9"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-protocol"] [tag "OWASP_CRS/PROTOCOL_VIOLATION/IP_HOST"] [tag "WASCTC/WASC-21"] [tag "OWASP_TOP_10/A7"] [tag "PCI/6.5.10"] [hostname "172.23.11.56"] [uri "/favicon.ico"] [unique_id "152395519294.104760"] [ref "o0,13v32,13"] ModSecurity: Warning. Matched "Operator `Rx' with parameter `(?i)([<xefxbcx9c]script[^>xefxbcx9e]*[>xefxbcx9e][sS]*?)' against variable `REQUEST_HEADERS:Referer' (Value: `http://172.23.26.157/?a=%3Cscript%3Ealert(aa)%3C/script%3E' ) [file "/opt/waf/owasp-modsecurity-crs/rules/REQUEST-941-APPLICATION-ATTACK-XSS.conf"] [line "63"] [id "941110"] [rev "2"] [msg "XSS Filter - Category 1: Script Tag Vector"] [data "Matched Data: <script> found within REQUEST_HEADERS:Referer: http://172.23.26.157/?a=%3Cscript%3Ealert(aa)%3C/script%3E"] [severity "2"] [ver "OWASP_CRS/3.0.0"] [maturity "4"] [accuracy "9"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-xss"] [tag "OWASP_CRS/WEB_ATTACK/XSS"] [tag "WASCTC/WASC-8"] [tag "WASCTC/WASC-22"] [tag "OWASP_TOP_10/A3"] [tag "OWASP_AppSensor/IE1"] [tag "CAPEC-242"] [hostname "172.23.11.56"] [uri "/favicon.ico"] [unique_id "152395519294.104760"] [ref "o24,8o24,8v230,58t:utf8toUnicode,t:urlDecodeUni,t:htmlEntityDecode,t:jsDecode,t:cssDecode,t:removeNulls"] ModSecurity: Warning. Matched "Operator `Rx' with parameter `(?i)<[^w<>]*(?:[^<>"'s]*:)?[^w<>]*(?:W*?sW*?cW*?rW*?iW*?pW*?t|W*?fW*?oW*?rW*?m|W*?sW*?tW*?yW*?lW*?e|W*?sW*?vW*?g|W*?mW*?aW*?rW*?qW*?uW*?eW*?e|(?:W*?lW*?iW*?nW*?k|W*?o (3246 characters omitted)' against variable `REQUEST_HEADERS:Referer' (Value: `http://172.23.26.157/?a=%3Cscript%3Ealert(aa)%3C/script%3E' ) [file "/opt/waf/owasp-modsecurity-crs/rules/REQUEST-941-APPLICATION-ATTACK-XSS.conf"] [line "195"] [id "941160"] [rev "2"] [msg "NoScript XSS InjectionChecker: HTML Injection"] [data "Matched Data: <script found within REQUEST_HEADERS:Referer: http://172.23.26.157/?a=%3Cscript%3Ealert(aa)%3C/script%3E"] [severity "2"] [ver "OWASP_CRS/3.0.0"] [maturity "1"] [accuracy "8"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-xss"] [tag "OWASP_CRS/WEB_ATTACK/XSS"] [tag "WASCTC/WASC-8"] [tag "WASCTC/WASC-22"] [tag "OWASP_TOP_10/A3"] [tag "OWASP_AppSensor/IE1"] [tag "CAPEC-242"] [hostname "172.23.11.56"] [uri "/favicon.ico"] [unique_id "152395519294.104760"] [ref "o24,7o41,8v230,58t:utf8toUnicode,t:urlDecodeUni,t:htmlEntityDecode,t:jsDecode,t:cssDecode,t:removeNulls"] ModSecurity: Warning. Matched "Operator `Ge' with parameter `5' against variable `TX:ANOMALY_SCORE' (Value: `13' ) [file "/opt/waf/owasp-modsecurity-crs/rules/REQUEST-949-BLOCKING-EVALUATION.conf"] [line "36"] [id "949110"] [rev ""] [msg "Inbound Anomaly Score Exceeded (Total Score: 13)"] [data ""] [severity "2"] [ver ""] [maturity "0"] [accuracy "0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-generic"] [hostname "172.23.11.56"] [uri "/favicon.ico"] [unique_id "152395519294.104760"] [ref ""] ModSecurity: Warning. Matched "Operator `Ge' with parameter `5' against variable `TX:INBOUND_ANOMALY_SCORE' (Value: `13' ) [file "/opt/waf/owasp-modsecurity-crs/rules/RESPONSE-980-CORRELATION.conf"] [line "61"] [id "980130"] [rev ""] [msg "Inbound Anomaly Score Exceeded (Total Inbound Score: 13 - SQLI=0,XSS=10,RFI=0,LFI=0,RCE=0,PHPI=0,HTTP=0,SESS=0): NoScript XSS InjectionChecker: HTML Injection'"] [data ""] [severity "0"] [ver ""] [maturity "0"] [accuracy "0"] [tag "event-correlation"] [hostname "172.23.11.56"] [uri "/favicon.ico"] [unique_id "152395519294.104760"] [ref ""] ---v3gm3tZj---I-- ---v3gm3tZj---J-- ---v3gm3tZj---Z--
默认只是检测,不拦截,可以修改配置,将
SecRuleEngine DetectionOnly改为
SecRuleEngine On
vi /usr/local/nginx/modsecurity.conf # Enable ModSecurity, attaching it to every transaction. Use detection # only to start with, because that minimises the chances of post-installation # disruption. # SecRuleEngine DetectionOnly #SecRuleEngine On
重启nginx
nginx -s reload
再测试,发现被拦截了。
更多modsecurity配置修改请参考 modsecurity配置学习文章
