cat /etc/redhat-release
CentOS Linux release 7.0.1406 (Core)
使用BIND构建DNS服务器
1.BIND服务器安装
yum install bind* -y
2.修改配置
vim /etc/named.conf
// // named.conf // // Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. // options { listen-on port 53 { 192.168.124.129; }; listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; allow-query { localhost; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; dnssec-lookaside auto; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; zone "nginxtest.com" IN { type master; file "nginxtest.com.zone"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";
cp /var/named/named.localhost /var/named/nginxtest.com.zone vim /var/named/nginxtest.com.zone
3.建立正向区域文件
$TTL 1D @ IN SOA nginxtest.com rname.invalid. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS @ @ A 192.168.124.129 www A 192.168.124.129 mail A 192.168.124.129
4.建立反向区域文件
5.修改权限
chmod 777 /var/named/nginxtest.com.zone
6.测试named.conf主配置文件
named-checkconf
7.测试区域文件
named-checkzone nginxtest.com /var/named/nginxtest.com.zone
8.配置DNS客户机配置文件
vim /etc/resolv.conf
# Generated by NetworkManager domain localdomain search localdomain nameserver 192.168.124.129 #nameserver 192.168.124.2
9.启动DNS服务器
systemctl daemon-reload
systemctl start named
systemctl status named
10.测试DNS服务器
DNS服务器的主要测试方法
使用nslookup、dig和host等专用工具可以对DNS服务器进行较全面的测试
nslookup命令在Linux和Windows系统中都默认安装,是比较常用的测试工具
进入nslookup命令交换环境
nslookup > server 192.168.124.129 测试localhost主机域名的正向解析 > localhost 测试localhost主机域名的反向解析 > 127.0.0.1 测试互联网中的域名解析 > www.nginxtest.com 测试nginxtest.com域中的A记录 > mail.nginxtest.com 测试nginxtest.com域中的CNAME记录 > www.nginxtest.com 测试nginxtest.com域中的NS记录 > set type=ns (设置域名查询类型为NS即域名记录) > nginxtest.com 测试nginxtest.com域中的MX记录 > set type=mx (设置域名查询类型为MX即邮件交换记录) > nginxtest.com 设置进行A记录的测试 > set type=a (设置域名查询类型为A即地址记录) >mail.nginxtest.com
测试DNS解析是否成功
host www.nginxtest.com
www.nginxtest.com has address 192.168.124.129
配置nginx.conf
#my nginx.conf user nginx; worker_processes 2; error_log /var/log/nginx/error.log warn; pid /var/run/nginx.pid; events { use epoll; worker_connections 1024; } http { include /etc/nginx/mime.types; default_type application/octet-stream; log_format main '$remote_addr - $remote_user [$time_local] "$request" ' '$status $body_bytes_sent "$http_referer" ' '"$http_user_agent" "$http_x_forwarded_for"'; access_log /var/log/nginx/access.log main; sendfile on; #tcp_nopush on; keepalive_timeout 65; #gzip on; include /etc/nginx/conf.d/*.conf; upstream v1 { server 192.168.124.130:8081; server 192.168.124.130:8082; } server { listen 443; ssl on; ssl_certificate /home/nginx/server.crt; ssl_certificate_key /home/nginx/server.key; ssl_session_timeout 5m; ssl_protocols SSLv2 SSLv3 TLSv1; ssl_ciphers ALL:!ADH:!EXPORT56:RC4+RSA:+HIGH:+MEDIUM:+LOW:+SSLv2:+EXP; ssl_prefer_server_ciphers on; server_name www.nginxtest.com; location / { proxy_pass http://v1; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; } } }
启动命令
#!/bin/bash docker run --name nginx -d -p 443:443 -p 80:80 -v /home/nginx/index.html:/usr/share/nginx/html/index.html -v /home/nginx/nginx.conf:/etc/nginx/nginx.conf -v /home/nginx/:/home/nginx/ -v /home/error/:/var/log/nginx/ nginx:latest
访问nginx
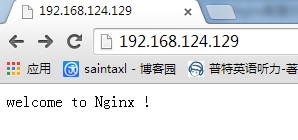
#/home/nginx/index.html
welcome to Nginx !
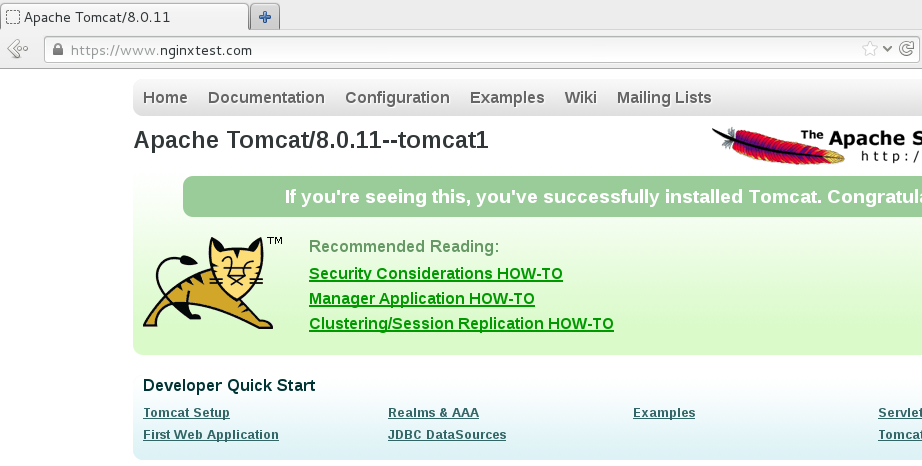
域名测试
Tomcat_1
Tomcat_2