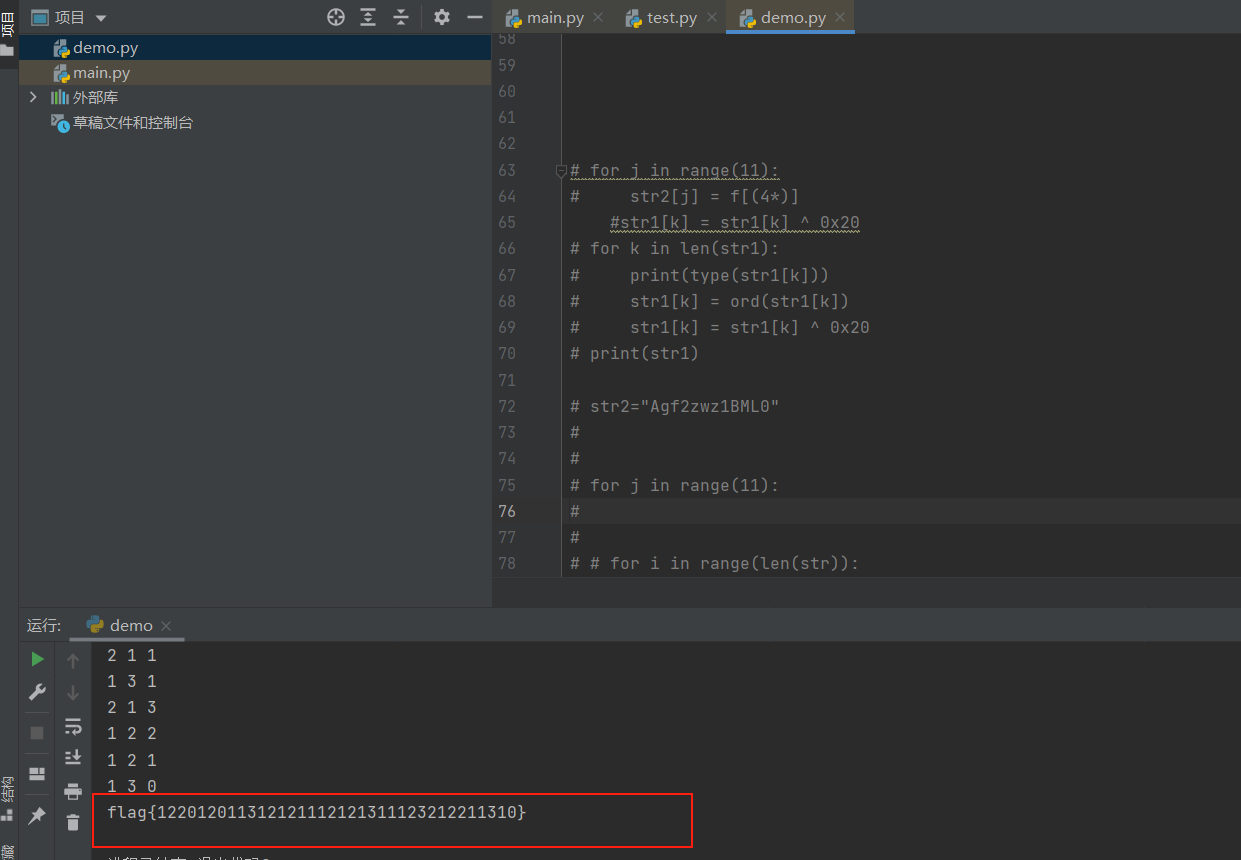
题目
链接: https://pan.baidu.com/s/1Ok1k3oxjIIydiUvYAuKydg 提取码: mhm9 复制这段内容后打开百度网盘手机App,操作更方便哦
解题思路
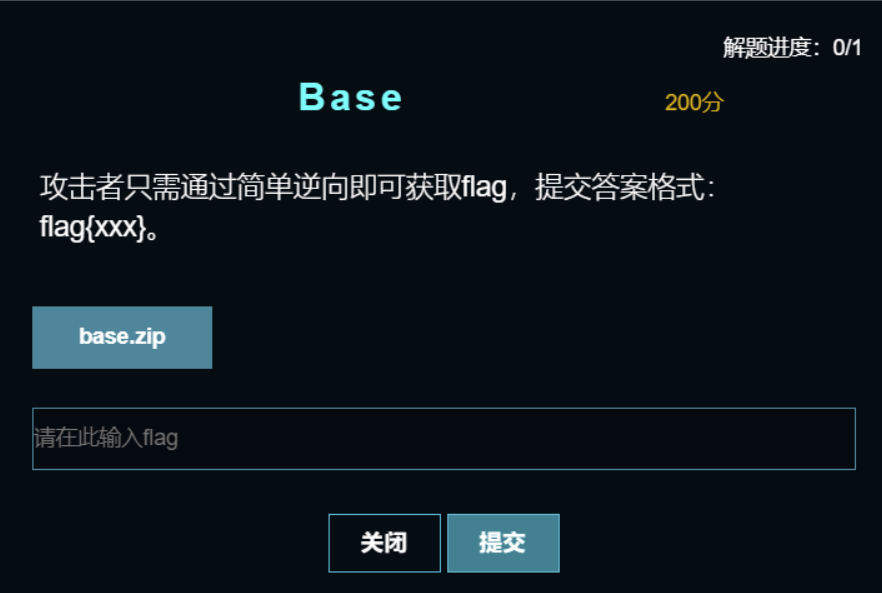
1、附件下载是一个base.exe,运行如下图:

2、扔到IDA,F5查看伪代码如下
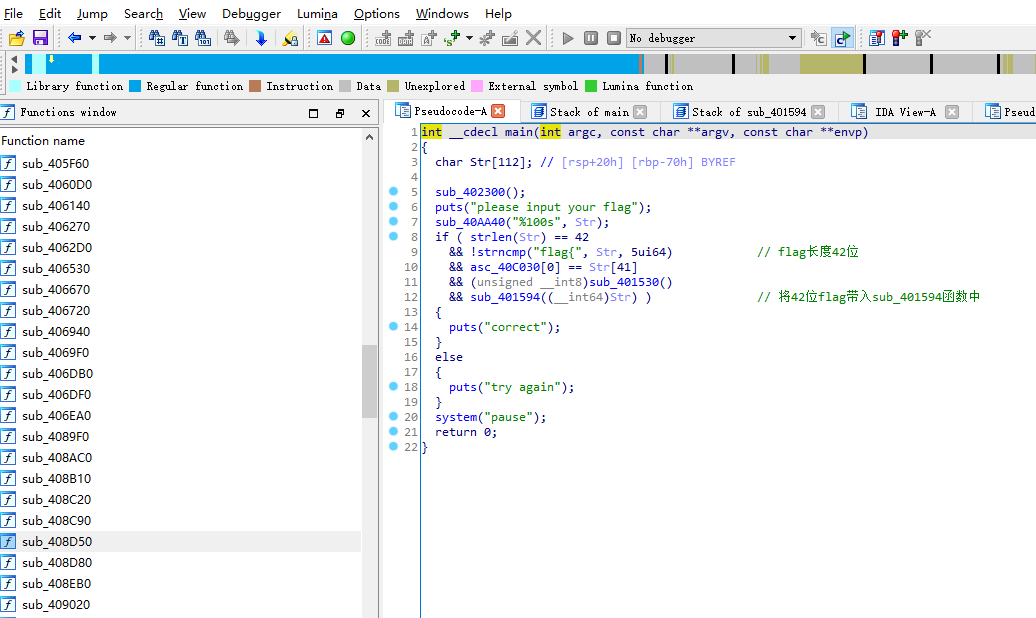
(1)对主函数进行分析,发现flag格式为flag{},总长度为42位
(2)需要分析sub_401530()函数与sub_401594()函数
主函数
int __cdecl main(int argc, const char **argv, const char **envp)
{
char Str[112]; // [rsp+20h] [rbp-70h] BYREF
sub_402300();
puts("please input your flag");
sub_40AA40("%100s", Str);
if ( strlen(Str) == 42
&& !strncmp("flag{", Str, 5ui64) // flag长度42位
&& asc_40C030[0] == Str[41]
&& (unsigned __int8)sub_401530()
&& sub_401594((__int64)Str) ) // 将42位flag带入sub_401594函数中
{
puts("correct");
}
else
{
puts("try again");
}
system("pause");
return 0;
}
sub_401530()函数分析
双击IDA sub_401530进入函数,内容如下
__int64 sub_401530()
{
int i; // [rsp+2Ch] [rbp-54h]
for ( i = 0; i < strlen(Str); ++i )
Str[i] ^= 0x20u;
return 1i64;
}
发现str[i]和0x20进行^运算得到新的str[],原始str[i]值如下:
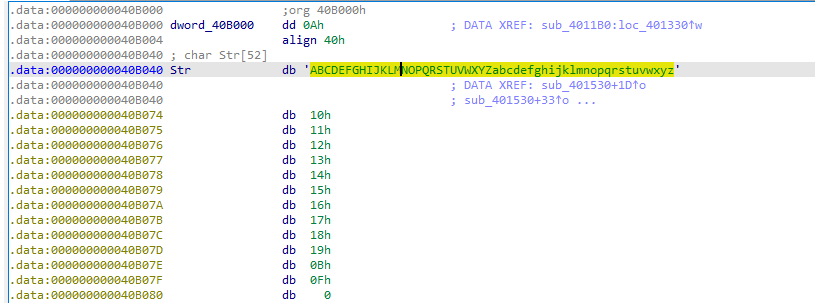
^结果为abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789+/,python代码如下:
str1="ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz"
str2=[]
str2.append(0x10)
str2.append(0x11)
str2.append(0x12)
str2.append(0x13)
str2.append(0x14)
str2.append(0x15)
str2.append(0x16)
str2.append(0x17)
str2.append(0x18)
str2.append(0x19)
str2.append(0x0B)
str2.append(0x0F)
print(str2)
f=""
c=32#0x20
for k in range(0,52):
print(k)
a = ord(str1[k])
d = int(a) ^ c
e = chr(d)
f = f+e
print(f)
for k in str2:
d = int(k) ^ c
e = chr(d)
f = f+e
print(f)
sub_401530函数分析
函数分析如下见注释
bool __fastcall sub_401594(__int64 a1)
{
char Destination[48]; // [rsp+20h] [rbp-50h] BYREF
char Str2[24]; // [rsp+50h] [rbp-20h] BYREF
int j; // [rsp+68h] [rbp-8h]
int i; // [rsp+6Ch] [rbp-4h]
strncpy(Destination, (const char *)(a1 + 5), 0x24ui64); //正向分析,将a1第5位,也就是flag括号中的内容赋值给destination数组
for ( i = 0; i <= 35; ++i )
{
if ( Destination[i] <= 47 || Destination[i] > 51 ) //说明flag的值只在48,49,50,51其中一位
return 0;
Destination[i] -= 48; //destination值0,1,2,3
}
for ( j = 0; j <= 11; ++j )
Str2[j] = Str[(4 * Destination[3 * j + 1]) | (16 * Destination[3 * j]) | Destination[3 * j + 2]]; //
return strncmp("Agf2zwz1BML0", Str2, 0xCui64) == 0; //str2的值要与Agf2zwz1BML0相等,因此Str[x]=A=str2[j] ,又因为str[26]=A,因此|运算结果是26,为flag—48
}
完整运行脚本如下
str1="ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz"
str2=[]
str2.append(0x10)
str2.append(0x11)
str2.append(0x12)
str2.append(0x13)
str2.append(0x14)
str2.append(0x15)
str2.append(0x16)
str2.append(0x17)
str2.append(0x18)
str2.append(0x19)
str2.append(0x0B)
str2.append(0x0F)
print(str2)
f=""
c=32#0x20
for k in range(0,52):
print(k)
a = ord(str1[k])
d = int(a) ^ c
e = chr(d)
f = f+e
print(f)
for k in str2:
d = int(k) ^ c
e = chr(d)
f = f+e
print(f)
str3=[]
g="Agf2zwz1BML0"
for i in g:
n = f.find(i)
str3.append(n)
print(str3)
str4=[0,1,2,3]
flag=''
for l in str3:
for i_4 in str4:
for i_16 in str4:
for i_1 in str4:
if(i_4*4 | i_16*16 | i_1*1) == l:
print(i_4,i_16,i_1)
flag = flag + chr(i_16+48)
flag = flag + chr(i_4 + 48)
flag = flag + chr(i_1+48)
print("flag{"+flag+"}")