alert udp $EXTERNAL_NET any -> $HOME_NET 1812 (msg:"SERVER-OTHER Microsoft Internet Authentication Service EAP-MSCHAPv2 authentication bypass attempt "; flow:to_server; content:"|01|"; depth:1; content:"|1A 02|"; distance:25; content:"|4F|"; within:2; distance:-8; content:"|02|"; within:1; distance:1; byte_test:2,<,74,1,relative; metadata:policy max-detect-ips drop; reference:cve,2009-3677; reference:url,technet.microsoft.com/en-us/security/bulletin/MS09-071; classtype:attempted-user; sid:16329; rev:8;)
最近写脚本时遇到这样的,distance带负号的偏移量。很容易理解是往前偏移8个字节再向后取两个,但是一定要注意,后面的规则 relative是根据上次content匹配的位置末尾再向后匹配,所以这里是在content:"|4F|"的匹配末尾再匹配。而不是content:"|1A 02|"
具体的nasl脚本可以这样写:
先组织udp报文,然后发送出去即可: 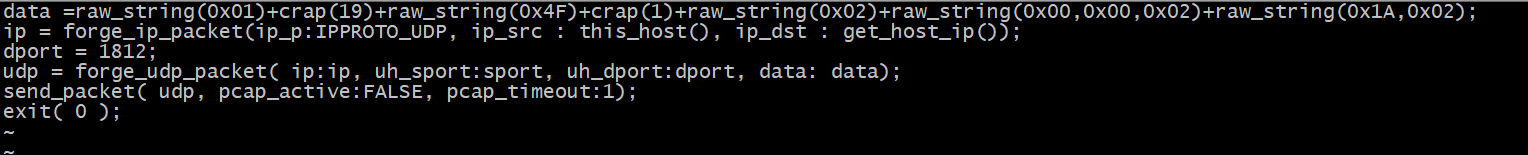
如果看不到完整图片,点击右键在新标签页中查看,或者复制图片即可