一、登录ssh失败次数统计
1)错误的打开方式
awk '/Failed password/ {print $(NF-3)}' secure |sort -n |uniq -c|sort -n |tail /var/log/secure

2)拷贝文件,再查看失败
cp /var/log/secure .
awk '/Failed password/ {print $(NF-3)}' secure |sort -n |uniq -c|sort -n |tail
3)直接查看失败
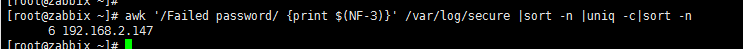
$ awk '/Failed password/ {print $(NF-3)}' /var/log/secure |sort -n |uniq -c|sort -n
4)查看最近失败的时间
less /var/log/secure
按G
二、对于防破解问题的处理
1)禁止密码登录方式
vi /etc/ssh/sshd_config
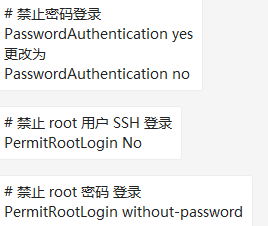
2)禁止失败的IP登录的方式

# # hosts.deny This file contains access rules which are used to # deny connections to network services that either use # the tcp_wrappers library or that have been # started through a tcp_wrappers-enabled xinetd. # # The rules in this file can also be set up in # /etc/hosts.allow with a 'deny' option instead. # # See 'man 5 hosts_options' and 'man 5 hosts_access' # for information on rule syntax. # See 'man tcpd' for information on tcp_wrappers # sshd:192.168.2.41:deny
在/etc/hosts.deny文件下面
添加 sshd:192.168.2.41:deny
重启sshd
三、实现python自动化写入文件
1)获取到失败IP的文件
awk '/Failed password/ {print $(NF-3)}' /var/log/secure |sort -n |uniq -c|sort -n > ip_fail.txt

2)查看原有的被限制IP的文件
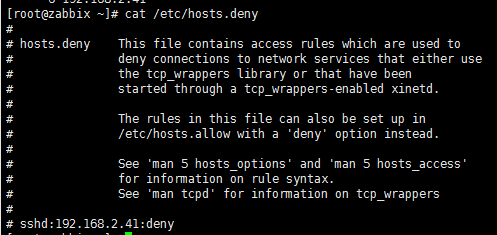
3)执行python脚本文件

def ip_index(): #读取文件获取到已经有被限制的IP ip_list = set() with open('hosts.deny',mode='r',encoding='utf-8') as f_log: for line in f_log: line = line.split(' ')[0].split(' ')[0] if len(line) !=0 and not line[0].startswith("#"): line = line.split(":") ip_list.add(line[1]) return ip_list def write(): # 写入失败的IP到配置文件中 with open('ip_fail.txt',mode='r',encoding='utf-8') as f: for line in f: line = line.split(' ')[0].split(' ') if int(line[6]) > 2: print('登录失败次数大于2的IP',line[7]) with open('hosts.deny',mode='a',encoding='utf-8') as f: if line[7] not in ip_list: f.write('sshd:%s:deny '%line[7]) if __name__ == '__main__': ip_list = ip_index() write()
四、定时任务自动写入hosts.deny配置文件的脚本
1)该脚本以失败次数大于3的进行测试(执行环境python3)

import subprocess command = "awk '/Failed password/ {print $(NF-3)}' /var/log/secure |sort -n |uniq -c|sort -n" def result(command): # 获取命令结果 obj=subprocess.Popen(command, shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE ) return obj.stdout def ip_list(result): # 根据命令结果获取到失败IP的字典 ip_set={} for line in result: line=str(line) ip = line.split(' ')[-1].split('\n')[0] count = line.split(' ')[-2] # 失败次数大于3的 if int(count) > 3: ip_set[count]=ip return ip_set def ip_index(): #读取文件获取到已经有被限制的IP out_ip = set() with open('/etc/hosts.deny',mode='r',encoding='utf-8') as f_log: for line in f_log: line = line.split(' ')[0].split(' ')[0] if len(line) !=0 and not line[0].startswith("#"): line = line.split(":") out_ip.add(line[1]) return out_ip def write(out_ip,in_ip): with open('/etc/hosts.deny',mode='a',encoding='utf-8') as f: for ip in out_ip: if out_ip[ip] not in in_ip: f.write('sshd:%s:deny '%out_ip[ip]) if __name__ == '__main__': in_ip = ip_index() # 获取已有被限制的IP result = result(command) # 得到命令结果 out_ip=ip_list(result) # 根据命令结果获取IP列表 write(out_ip,in_ip)
2) centos6默认的python2.6执行环境

import subprocess command = "awk '/Failed password/ {print $(NF-3)}' /var/log/secure |sort -n |uniq -c|sort -n" def result(command): obj=subprocess.Popen(command, shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE ) return obj.stdout def ip_list(result): ip_set={} for line in result: line=str(line) ip = line.split(' ')[-1].split('\n')[0] count = line.split(' ')[-2] if int(count) > 3: ip_set[count]=ip return ip_set def ip_index(): out_ip = set() with open('/etc/hosts.deny',mode='r') as f_log: for line in f_log: line = line.split(' ')[0].split(' ')[0] if len(line) !=0 and not line[0].startswith("#"): line = line.split(":") out_ip.add(line[1]) return out_ip def write(out_ip,in_ip): with open('/etc/hosts.deny',mode='a') as f: for ip in out_ip: if out_ip[ip] not in in_ip: f.write('sshd:%s:deny '%out_ip[ip]) if __name__ == '__main__': in_ip = ip_index() result = result(command) out_ip=ip_list(result) write(out_ip,in_ip)
3)修改bug。(以IP为key),前面是以次数为key。

import subprocess command = "awk '/Failed password/ {print $(NF-3)}' /var/log/secure |sort -n |uniq -c|sort -n" def result(command): # 获取命令结果 obj=subprocess.Popen(command, shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE ) return obj.stdout def ip_list(result): # 根据命令结果获取到失败IP的字典 ip_set={} for line in result: line=str(line) ip = line.split(' ')[-1].split('\n')[0] count = line.split(' ')[-2] # 失败次数大于3的 if int(count) > 3: ip_set[ip]=count return ip_set def ip_index(): #读取文件获取到已经有被限制的IP out_ip = set() with open('/etc/hosts.deny',mode='r',encoding='utf-8') as f_log: for line in f_log: line = line.split(' ')[0].split(' ')[0] if len(line) !=0 and not line[0].startswith("#"): line = line.split(":") out_ip.add(line[1]) return out_ip def write(out_ip,in_ip): with open('/etc/hosts.deny',mode='a',encoding='utf-8') as f: for ip in out_ip: print(ip) if ip not in in_ip: f.write('sshd:%s:deny '%ip) if __name__ == '__main__': in_ip = ip_index() # 获取已有被限制的IP result = result(command) # 得到命令结果 out_ip=ip_list(result) # 根据命令结果获取IP列表 write(out_ip,in_ip)
