本篇随笔为对OSPF与ACL的综合运用使用
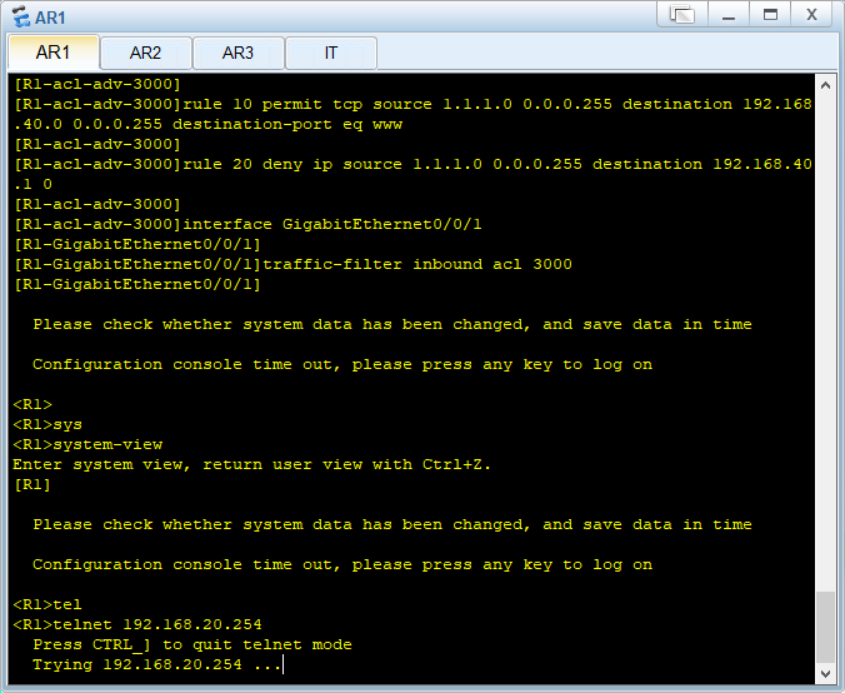
拓扑图如下所示
实验要求:
1.企业内网运行OSPF路由协议,区域规划如图所示;
2.财务和研发所在的区域不受其他区域链路不稳定性影响;
3.R1、R2、R3只允许被IT登录管理;
4.YF和CW之间不能互通,但都可以与IT互通;
5.IT和YF可以访问Client1,但CW不能访问Client1;
6.YF和CW只能访问Server1的WWW服务;
拓扑图中各线路与终端设备的地址已记录 然后对路由器与客户端等设备进行基本配置如下所示
R1
sysname R1
interface GigabitEthernet0/0/0
ip address 1.1.1.254 255.255.255.0
interface GigabitEthernet0/0/1
ip address 192.168.12.1 255.255.255.0
interface GigabitEthernet0/0/2
ip address 192.168.13.1 255.255.255.0
quit
R2
sysname R2
interface GigabitEthernet0/0/0
ip address 192.168.12.2 255.255.255.0
interface GigabitEthernet0/0/1
ip address 192.168.10.254 255.255.255.0
interface GigabitEthernet0/0/2
ip address 192.168.20.254 255.255.255.0
quit
R3
sysname R3
interface GigabitEthernet0/0/0
ip address 192.168.13.2 255.255.255.0
interface GigabitEthernet0/0/1
ip address 192.168.30.254 255.255.255.0
interface GigabitEthernet0/0/2
ip address 192.168.40.254 255.255.255.0
quit
将终端设备的ip地址配置好 将网关设置成与之相连的路由器的端口ip
下一步在每个路由器上配置OSPF 并设置相连的网段
R1
ospf 1 router-id 1.1.1.1
area 0.0.0.0
network 192.168.12.0 0.0.0.255
network 192.168.13.0 0.0.0.255
area 0.0.0.1
network 1.1.1.0 0.0.0.255
quit
R2
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 192.168.12.0 0.0.0.255
area 0.0.0.2
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
stub no-summary
quit
R3
ospf 1 router-id 3.3.3.3
area 0.0.0.0
network 192.168.13.0 0.0.0.255
area 0.0.0.3
network 192.168.30.0 0.0.0.255
network 192.168.40.0 0.0.0.255
stub no-summary
quit
sysname IT
interface GigabitEthernet0/0/0
ip address 192.168.10.1 255.255.255.0
ospf 1
area 0.0.0.2
network 192.168.10.0 0.0.0.255
stub no-summary
然后可以用display ospf brief查看一下自己的设置有没有问题


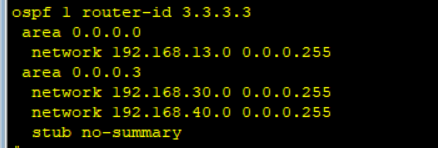

由于财务部与研发部所在区域不能受链路不稳定的影响 顾将其区域内路由器使用stub no-summary 设置为完全末梢区域 隔绝其他路由器路由表对其影响 ,
第三步 我们通过配置ACL 来完成题目对我们的要求
财务部ACL设置
R3
acl number 2000 仅允许IT部登录管理
rule 10 permit source 192.168.10.0 0.0.0.255
user-interface vty 0 4
acl 2000 inbound
authentication-mode password
123
acl name cw
rule 10 deny ip source 192.168.30.0 0.0.0.255 destination 1.1.1.0 0.0.0.255 禁止CW连接Client1
rule 20 deny ip source 192.168.30.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 CW与YF不能互通
rule 30 permit tcp source 192.168.30.0 0.0.0.255 destination 192.168.40.1 0 destination-port eq www CW允许访问server1的HTTP服务
rule 40 deny ip source 192.168.30.0 0.0.0.255 destination 192.168.40.1 0 CW不许连接server1
interface GigabitEthernet0/0/1
traffic-filter inbound acl name cw
研发部ACL设置
R2
acl number 2000
rule 10 permit source 192.168.10.0 0.0.0.255 仅允许IT部登录管理
user-interface vty 0 4
acl 2000 inbound
authentication-mode password
123
acl name yf
rule 10 deny ip source 192.168.20.0 0.0.0.255 destination 192.168.30.0 0.0.0.255 YF与CW不能互通
rule 20 permit tcp source 192.168.20.0 0.0.0.255 destination 192.168.40.1 0 destination-port eq www YF可以访问server1的HTTP服务
rule 30 deny ip source 192.168.20.0 0.0.0.255 destination 192.168.40.0 0.0.0.255 YF不能访问server1
interface GigabitEthernet0/0/2
traffic-filter inbound acl name yf
IT部ACL设置
R1
acl number 2000 仅允许IT部登录管理
rule 10 permit source 192.168.10.0 0.0.0.255
user-interface vty 0 4
acl 2000 inbound
authentication-mode password
123
acl number 3000
rule 10 permit tcp source 1.1.1.0 0.0.0.255 destination 192.168.40.0 0.0.0.255 destination-port eq www 允许client1访问server1的HTTP服务
rule 20 deny ip source 1.1.1.0 0.0.0.255 destination 192.168.40.1 0 禁止Client连接server1
interface GigabitEthernet0/0/1
traffic-filter inbound acl 3000
验证结果:
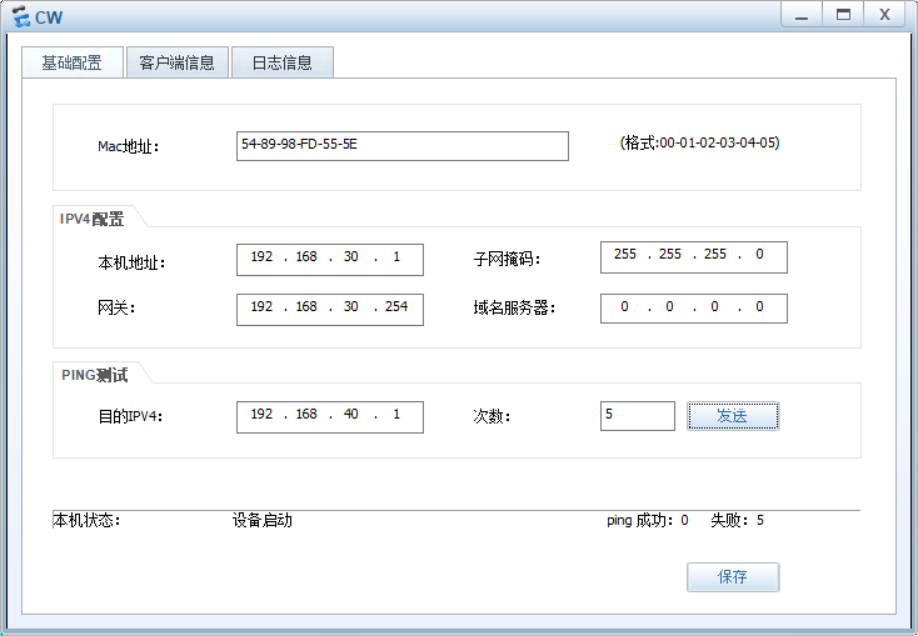
cw可以连接server1的http服务 但不能ping通server1
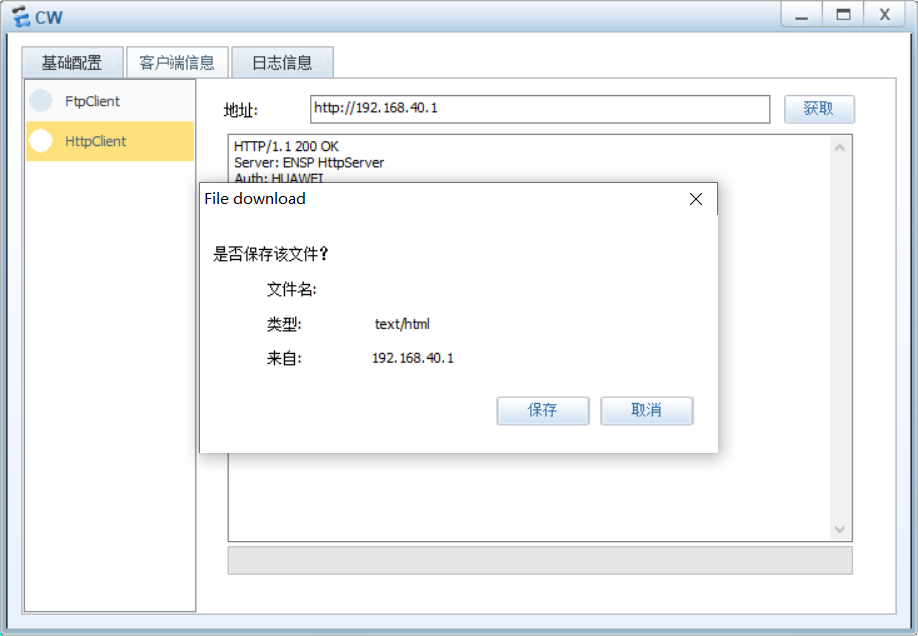
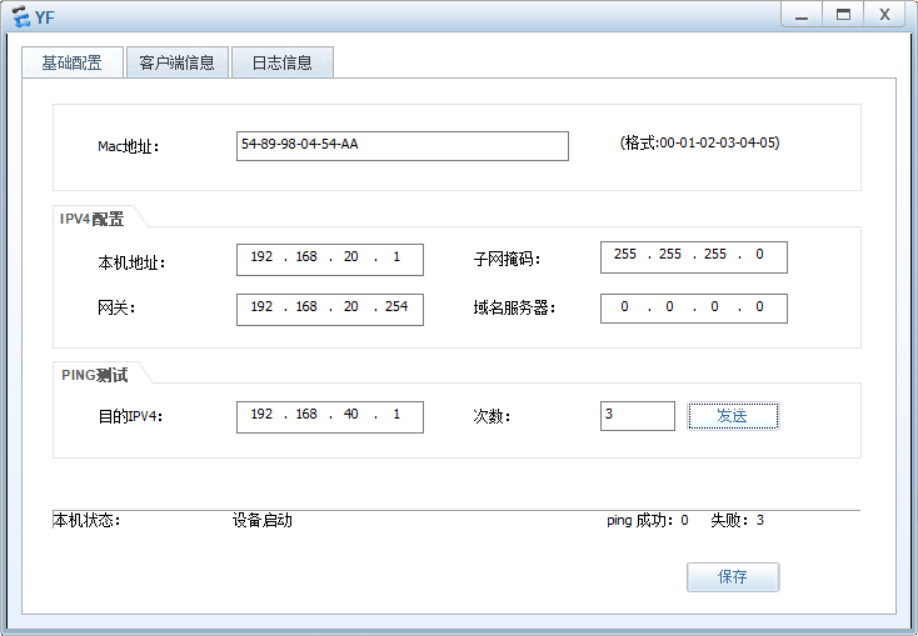
YF可以连接server1的HTTP服务 但不能ping通

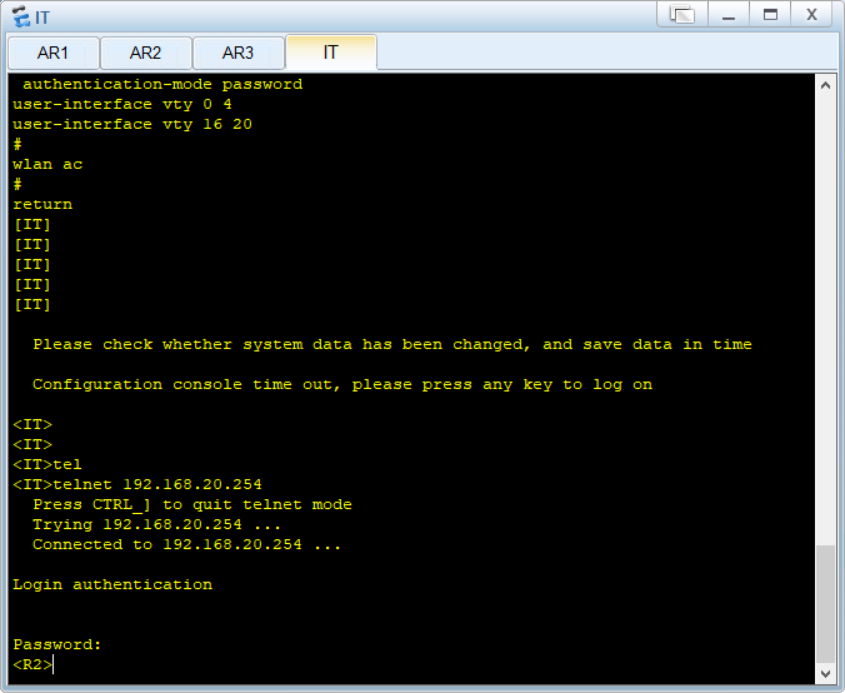
IT可以登录R2 等设备
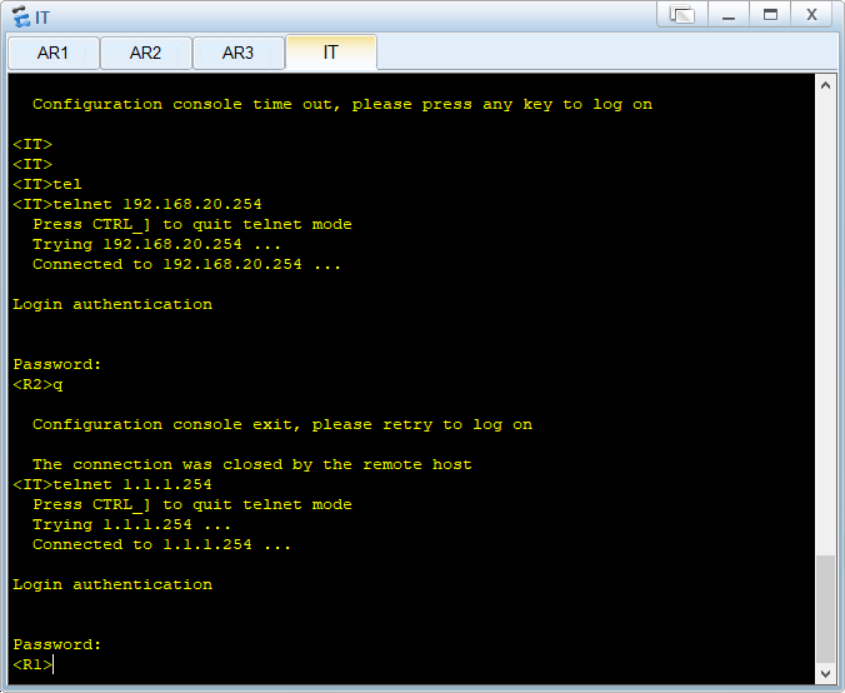
但R1无法登录