step by step

连接上,查看文件
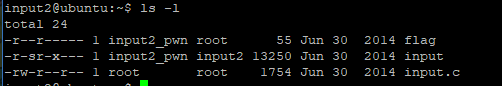
input.c内容:
#include <stdio.h> #include <stdlib.h> #include <string.h> #include <sys/socket.h> #include <arpa/inet.h> int main(int argc, char* argv[], char* envp[]){ printf("Welcome to pwnable.kr "); printf("Let's see if you know how to give input to program "); printf("Just give me correct inputs then you will get the flag :) "); // argv if(argc != 100) return 0; if(strcmp(argv['A'],"x00")) return 0; if(strcmp(argv['B'],"x20x0ax0d")) return 0; printf("Stage 1 clear! "); // stdio char buf[4]; read(0, buf, 4); if(memcmp(buf, "x00x0ax00xff", 4)) return 0; read(2, buf, 4); if(memcmp(buf, "x00x0ax02xff", 4)) return 0; printf("Stage 2 clear! "); // env if(strcmp("xcaxfexbaxbe", getenv("xdexadxbexef"))) return 0; printf("Stage 3 clear! "); // file FILE* fp = fopen("x0a", "r"); if(!fp) return 0; if( fread(buf, 4, 1, fp)!=1 ) return 0; if( memcmp(buf, "x00x00x00x00", 4) ) return 0; fclose(fp); printf("Stage 4 clear! "); // network int sd, cd; struct sockaddr_in saddr, caddr; sd = socket(AF_INET, SOCK_STREAM, 0); if(sd == -1){ printf("socket error, tell admin "); return 0; } saddr.sin_family = AF_INET; saddr.sin_addr.s_addr = INADDR_ANY; saddr.sin_port = htons( atoi(argv['C']) ); if(bind(sd, (struct sockaddr*)&saddr, sizeof(saddr)) < 0){ printf("bind error, use another port "); return 1; } listen(sd, 1); int c = sizeof(struct sockaddr_in); cd = accept(sd, (struct sockaddr *)&caddr, (socklen_t*)&c); if(cd < 0){ printf("accept error, tell admin "); return 0; } if( recv(cd, buf, 4, 0) != 4 ) return 0; if(memcmp(buf, "xdexadxbexef", 4)) return 0; printf("Stage 5 clear! "); // here's your flag system("/bin/cat flag"); return 0; }
看出来,要一关一关通过各种输入,然后可以执行system("/bin/cat flag")。
参考博客:https://r00tk1ts.github.io/2018/03/06/input/
然后在/tmp/input目录建立时,建立失败,原因是存在,所以进去看看,发现:
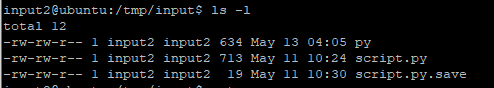
有文件,cat一下py,发现是这个题的payload,直接运行了一下,发现没问题,只差建立一个软链接:
ln -s /home/input2/flag flag
建立链接后,运行得到flag。
当然还是自己做做看
我的payload:
import os import socket import time import subprocess stdinr,stdinw = os.pipe() stderrr,stderrw = os.pipe() #argv args = list("a"*99) args[ord('A')-1] = "" args[ord('B')-1] = "x20x0ax0d" args[ord("C")-1] = "8888" #stdio os.write(stdinw,"x00x0ax00xff") os.write(stderrw,"x00x0ax02xff") #env envir = {"xdexadxbexef":"xcaxfexbaxbe"} #file f = open("x0a","w") f.write("x00"*4) f.close() pro = subprocess.Popen(["/home/input2/input"]+args,stdin=stdinr,stderr=stderrr,env=envir) #network s = socket.socket(socket.AF_INET,socket.SOCK_STREAM) time.sleep(2) s.connect(("127.0.0.1",8888)) s.send("xdexadxbexef") s.close()
在子进程中打开一个程序,并通过管道将父进程构造的参数传到子进程的程序中
使用到的知识:
subprocess:https://www.cnblogs.com/Security-Darren/p/4733368.html