curl -k https:/www.test.com -v –-key key.pem –-cacert ca.pem –-cert client.pem
-k allows insecure connections,makes everything here insecure
PKI – Public key infrastructure
CA – Certificate Authority
CSR – Certificate signing request
SSL – Secure Socket Layer
TLS – Transport Layer Security
Root CA – Root Certificate Authority Certificate (Public)
3 types of SSL Certificates.
Self Signed SSL
SSL from Trusted Certificate Authorities
SSL signed by own Certificate Authority
generates a private key and certificate
private.key certificate.crt
openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:4096 -keyout private.key -out certificate.crt
req - Command passed to OpenSSL intended for creating and processing certificate requests usually in the PKCS#10 format.
-x509 - This multipurpose command allows OpenSSL to sign the certificate somewhat like a certificate authority. X.509 refers to a digitally signed document according to RFC 5280.
-sha256 - This is the hash to use when encrypting the certificate.
-nodes - This command is for no DES, which means that the private key will not be password protected.
-days - The number of days that the certificate will be valid.
-newkey - The format of the key, in this case an RSA key with 4096 bit encryption.
-keyout - The location to output the private key of the self-signed certificate.
-out - The location to output the certificate file itself.
verify that it is correct according to the parameters that we have set
openssl x509 -in certificate.crt -text -noout
x509 - This is a multipurpose command, and when combined with the other parameters here, it is for retrieving information about the passed in the certificate.
-in - The certificate that we are verifying.
-text - Strips the text headers from the output.
-noout - Needed not to output the encoded version of the certificate
create certificate signing requests for requesting a certificate from a certificate authority that is trusted.
equest.csr
openssl req -new -newkey rsa:2048 -nodes -out request.csr -keyout private.key
this command generates a CSR.
You will notice that the -x509, -sha256, and -days parameters are missing.
By leaving those off, we are telling OpenSSL that another certificate authority will issue the certificate.
In this case, we are leaving the -nodes option on to not prompt for a password with the private key.
verify that the CSR is correct
openssl req -in request.csr -text -noout -verify
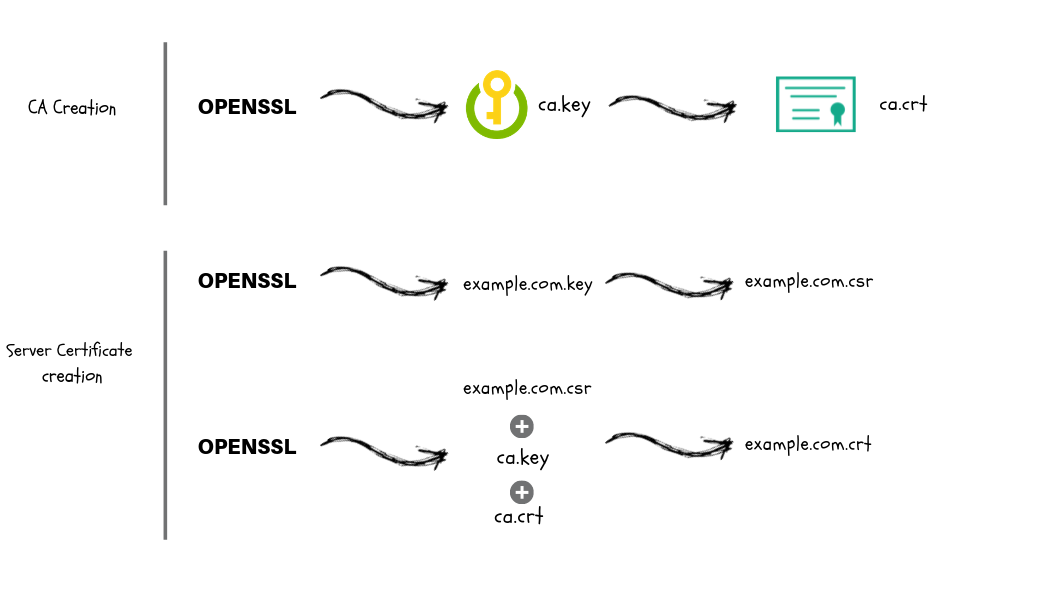
Generate the CA private key file.
ca.key
openssl genrsa -out ca.key 2048
Generate CA x509 certificate file using the CA key
ca.crt
openssl req -x509 -new -nodes -key ca.key -sha256 -days 1825 -out ca.crt
openssl req -x509 -new -nodes -key ca.key -subj "/CN=scriptcrunch/C=US/L=CALIFORNIA" -days 1825 -out ca.crt
Create a server private key
openssl genrsa -out server.key 2048
Create a configuration file named csr.conf for generating the Certificate Signing Request (CSR)
cat > csr.conf <<EOF
[ req ]
default_bits = 2048
prompt = no
default_md = sha256
req_extensions = req_ext
distinguished_name = dn
[ dn ]
C = US
ST = California
L = San Fransisco
O = Scriptcrunch
OU = Scriptcrunch Dev
CN = scriptcrunch.com
[ req_ext ]
subjectAltName = @alt_names
[ alt_names ]
DNS.1 = scriptcrunch
DNS.2 = scriptcrunch.com
IP.1 = 10.34.12.5
IP.2 = 10.34.12.5
EOF
Generate the CSR using the private key and config file
openssl req -new -key server.key -out server.csr -config csr.conf
Generate the server SSL certificate using ca.key, ca.crt and server.csr
openssl x509 -req -in server.csr -CA ca.crt -CAkey ca.key
-CAcreateserial -out server.crt -days 10000
-extfile csr.conf
https://scriptcrunch.com/create-ca-tls-ssl-certificates-keys/