DMVPN基础拓扑:
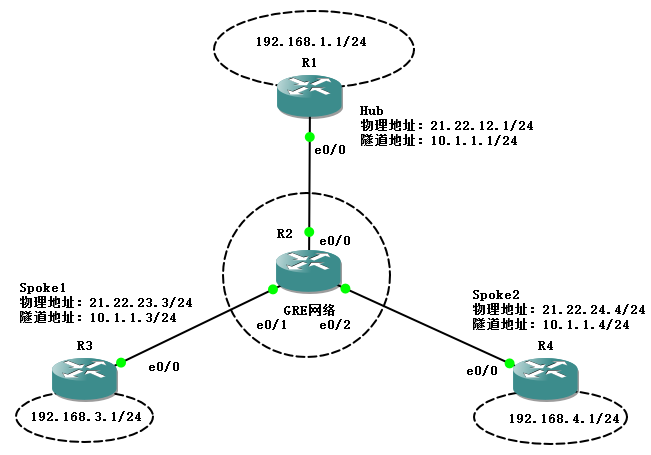
配置步骤:
1. 基本IP地址配置实现网络可达
2. 配置GRE多点隧道(mGRE)和NHRP(下一跳解析协议)
3. 配置EIGRP路由协议
4. 配置IPSec
------------------------------------------------------------------------------------------------------------------------------------------
备注:由于这里的IOS(IOU或EVE可以)不能在Hub配置ip nhrp redirect;也不能在Spoke配置ip nhrp shortcut;所以Spoke1到Spoke2的流量都需要经过Hub。
DMVPN中“包治百病”的大招(Hub端):
int tun 0
shut
no shu
------------------------------------------------------------------------------------------------------------------------------------------
R1
!
hostname Hub
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set Trans esp-des esp-md5-hmac
mode transport
!
crypto ipsec profile DMVPN
set transform-set Trans
!
interface Loopback0
ip address 192.168.1.1 255.255.255.0
!
interface Tunnel0
ip address 10.1.1.1 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication cisco
ip nhrp map multicast dynamic
ip nhrp network-id 10
ip summary-address eigrp 10 192.168.0.0 255.255.0.0 5
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 123
tunnel protection ipsec profile DMVPN
!
interface Ethernet0/0
ip address 21.22.12.1 255.255.255.0
ip ospf network point-to-point
half-duplex
!
router eigrp 10
network 10.1.1.0 0.0.0.255
network 192.168.1.0
no auto-summary
!
router ospf 10
router-id 192.168.1.1
log-adjacency-changes
network 21.22.12.0 0.0.0.255 area 0
!
R2
hostname R2
!
interface Ethernet0/0
ip address 21.22.12.2 255.255.255.0
ip ospf network point-to-point
half-duplex
!
router ospf 10
router-id 2.2.2.2
log-adjacency-changes
network 21.22.12.0 0.0.0.255 area 0
network 21.22.23.0 0.0.0.255 area 0
network 21.22.24.0 0.0.0.255 area 0
R3
hostname Spoke1
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set Trans esp-des esp-md5-hmac
mode transport
!
crypto ipsec profile DMVPN
set transform-set Trans
!
interface Loopback0
ip address 192.168.3.1 255.255.255.0
!
interface Tunnel0
ip address 10.1.1.3 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication cisco
ip nhrp map 10.1.1.1 21.22.12.1
ip nhrp map multicast 21.22.12.1
ip nhrp network-id 10
ip nhrp nhs 10.1.1.1
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 123
tunnel protection ipsec profile DMVPN
!
interface Ethernet0/0
ip address 21.22.23.3 255.255.255.0
ip ospf network point-to-point
half-duplex
!
router eigrp 10
network 10.1.1.0 0.0.0.255
network 192.168.3.0
no auto-summary
!
router ospf 10
router-id 192.168.3.1
log-adjacency-changes
network 21.22.23.0 0.0.0.255 area 0
R4
hostname Spoke2
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set Trans esp-des esp-md5-hmac
mode transport
!
crypto ipsec profile DMVPN
set transform-set Trans
!
interface Loopback0
ip address 192.168.4.1 255.255.255.0
!
interface Tunnel0
ip address 10.1.1.4 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication cisco
ip nhrp map 10.1.1.1 21.22.12.1
ip nhrp map multicast 21.22.12.1
ip nhrp network-id 10
ip nhrp nhs 10.1.1.1
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 123
tunnel protection ipsec profile DMVPN
!
interface Ethernet0/0
ip address 21.22.24.4 255.255.255.0
ip ospf network point-to-point
half-duplex
!
router eigrp 10
network 10.1.1.0 0.0.0.255
network 192.168.4.0
no auto-summary
!
router ospf 10
router-id 192.168.4.1
log-adjacency-changes
network 21.22.24.0 0.0.0.255 area 0
查看NHRP信息:
Hub#sho ip nhrp
10.1.1.3/32 via 10.1.1.3, Tunnel0 created 00:13:51, expire 01:49:43
Type: dynamic, Flags: authoritative unique registered
NBMA address: 21.22.23.3
10.1.1.4/32 via 10.1.1.4, Tunnel0 created 00:13:53, expire 01:50:40
Type: dynamic, Flags: authoritative unique registered
NBMA address: 21.22.24.4
Spoke1#sho ip nhrp
10.1.1.1/32 via 10.1.1.1, Tunnel0 created 00:24:26, never expire
Type: static, Flags: authoritative used
NBMA address: 21.22.12.1
Spoke2#sho ip nhrp
10.1.1.1/32 via 10.1.1.1, Tunnel0 created 00:22:03, never expire
Type: static, Flags: authoritative used
NBMA address: 21.22.12.1
可以看到在Hub上已经有两个分支的解析,同样的两个分支也可以解析到Hub物理接口的地址。
测试联通性:
Spoke1#ping 192.168.4.1 source 192.168.3.1 repeat 1000
Type escape sequence to abort.
Sending 1000, 100-byte ICMP Echos to 192.168.4.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.3.1
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!.
Success rate is 98 percent (50/51), round-trip min/avg/max = 20/44/88 ms
分支1到分支2的ping包可以通信,那么看是否需要经过Hub进行转发。
Spoke1#traceroute 192.168.4.1 source 192.168.3.1
Type escape sequence to abort.
Tracing the route to 192.168.4.1
1 10.1.1.1 20 msec 40 msec 16 msec
2 10.1.1.4 40 msec 32 msec 52 msec
路由表情况
Hub#sho ip route eigrp
D 192.168.4.0/24 [90/297372416] via 10.1.1.4, 00:13:14, Tunnel0
D 192.168.3.0/24 [90/297372416] via 10.1.1.3, 00:14:09, Tunnel0
D 192.168.0.0/16 is a summary, 00:17:48, Null0
Spoke1#sho ip route eigrp
D 192.168.0.0/16 [90/297372416] via 10.1.1.1, 00:14:02, Tunnel0
Spoke2#sho ip route eigrp
D 192.168.0.0/16 [90/297372416] via 10.1.1.1, 00:13:30, Tunnel0