为什么会有INLNE HOOK呢?
它比起IAT HOOK会比较隐蔽
需要注意的事项:
1、在进行INLINE HOOK的时候一定要注意堆栈的平衡
2、整个过程要有来回,CALL OR JMP跳过去之后还需要RETN OR JMP跳回来
3、了解 E8 E9 跳转的计算公式
4、发现无法修改可以尝试用VirtualProtect对物理页进行修改
#include<Windows.h>
#include<cstdio>
typedef struct _Register{
DWORD eax;
DWORD ecx;
DWORD edx;
DWORD ebx;
DWORD esp;
DWORD ebp;
DWORD esi;
DWORD edi;
}Register;
_Register reg = { 0 };
DWORD dwPlusFunctionAddr;
DWORD dwPlusFunctionHookAfterAddr;
PBYTE pEditedAddr;
DWORD dwX;
DWORD dwY;
extern "C" _declspec(naked)void HookProc(){
__asm{
pushad;
pushfd;
}
__asm{
mov reg.eax, eax;
mov reg.ecx, ecx;
mov reg.edx, edx;
mov reg.ebx, ebx;
mov reg.esp, esp;
mov reg.ebp, ebp;
mov reg.esi, esi;
mov reg.edi, edi;
mov eax, DWORD ptr SS : [esp + 0x28];
mov dwX, eax;
mov eax, DWORD ptr SS : [esp + 0x2C];
mov dwY, eax;
}
printf("%x %x %x %x %x %x %x %x
", reg.eax, reg.ecx, reg.edx, reg.ebx, reg.esp, reg.ebp, reg.esi, reg.edi);
printf("dwX: %d, dwY: %d
", dwX, dwY);
MessageBox(NULL, TEXT("it's my inline HoOk"), 0, MB_OK);
__asm{
popfd;
popad;
}
__asm{
push ebp;
mov ebp, esp;
sub esp, 40h;
}
__asm{
jmp dwPlusFunctionHookAfterAddr;
}
}
void InstallInlineHook(DWORD dwPlusFunctionAddr, DWORD dwHookLength){
//保存原有的dwHookLength个字节
pEditedAddr = (PBYTE)malloc(dwHookLength);
memcpy(pEditedAddr, (LPVOID)dwPlusFunctionAddr, dwHookLength);
DWORD dwOldProtect;
BOOL ret = VirtualProtect((LPVOID)dwPlusFunctionAddr, dwHookLength, PAGE_EXECUTE_READWRITE, &dwOldProtect);
if (!ret){
printf("VirtualProtect Failed, the error is %d
", GetLastError());
return;
}
//获取HOOK的地址
DWORD dwHookProc = (DWORD)HookProc;
//计算JMP之后的地址
DWORD dwJmpAddr = dwHookProc - (dwPlusFunctionAddr + 5);
//初始化0x90数据
memset((PBYTE)dwPlusFunctionAddr, 0x90, dwHookLength);
//进行替换跳转的硬编码
*(PCHAR)dwPlusFunctionAddr = 0xE9;
*(PDWORD)((PCHAR)dwPlusFunctionAddr + 1) = dwJmpAddr;
}
void UninstallInlineHook(DWORD dwPlusFunctionAddr, DWORD dwHookLength){
DWORD dwOldProtect;
BOOL ret = VirtualProtect((LPVOID)dwPlusFunctionAddr, dwHookLength, PAGE_EXECUTE_READWRITE, &dwOldProtect);
if (!ret){
printf("VirtualProtect Failed, the error is %d
", GetLastError());
return;
}
memcpy((PVOID)dwPlusFunctionAddr, pEditedAddr, dwHookLength);
free(pEditedAddr);
pEditedAddr = NULL;
}
int plus(int x, int y)
{
return x + y;
}
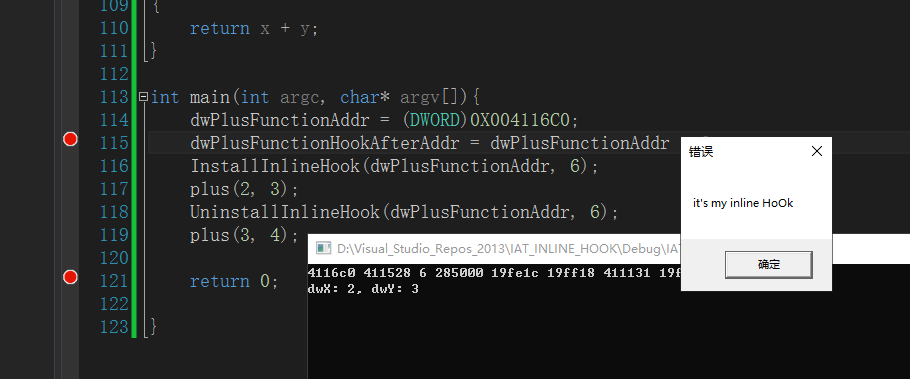
int main(int argc, char* argv[]){
dwPlusFunctionAddr = (DWORD)0X004116C0;
dwPlusFunctionHookAfterAddr = dwPlusFunctionAddr + 6;
InstallInlineHook(dwPlusFunctionAddr, 6);
plus(2, 3);
UninstallInlineHook(dwPlusFunctionAddr, 6);
plus(3, 4);
return 0;
}