一、非对称密码运用
1、# rpm --import https://packages.elastic.co/GPG-KEY-elasticsearch (下载公钥)
# vim /etc/yum.repos.d/elasticsearch.repo
[elasticsearch-2.x]
name=Elasticsearch repository for 2.x packages
baseurl=http://packages.elastic.co/elasticsearch/2.x/centos
gpgcheck=1 (红帽公司私钥加密好,再用公钥解密)
gpgkey=http://packages.elastic.co/GPG-KEY-elasticsearch
enabled=1
2、要求把211机子 /etc/fstab 文件加密传到132机子 ,只能由132解开。
[root@elk-node1 ~]# gpg --gen-key
gpg (GnuPG) 2.0.22; Copyright (C) 2013 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
Your selection? 1
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048)
Requested keysize is 2048 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0)
Key does not expire at all
Is this correct? (y/N) y
GnuPG needs to construct a user ID to identify your key.
Real name: zjz
Name must be at least 5 characters long
Real name: zjzzjz
Email address:
Comment:
You selected this USER-ID: "zjzzjz"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit?
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
You need a Passphrase to protect your secret key.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.

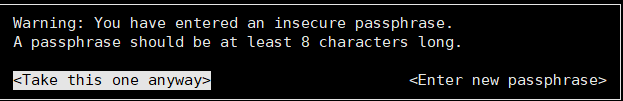
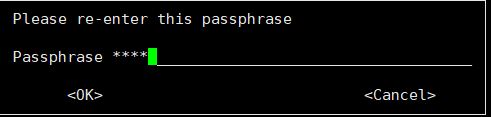
gpg: /root/.gnupg/trustdb.gpg: trustdb created gpg: key 5686364C marked as ultimately trusted
public and secret key created and signed.
gpg: checking the trustdb
gpg: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg: depth: 0 valid: 1 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 1u
pub 2048R/5686364C 2019-09-20
Key fingerprint = 23D3 6C44 4395 19F1 36EE 2069 998D 2612 5686 364C
uid zjzzjz (github) <fan@qq.com>
sub 2048R/59953D36 2019-09-20
[root@elk-node1 ~]# cd .gnupg/
[root@elk-node1 .gnupg]# ls
gpg.conf pubring.gpg(公钥) random_seed S.gpg-agent
private-keys-v1.d pubring.gpg~ secring.gpg(私钥) trustdb.gpg
[root@elk-node1 .gnupg]# gpg -a --export -o zjz.pubkey (-o指定文件,自己定,export导出公钥)
[root@elk-node1 .gnupg]# cat zjz.pubkey
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: GnuPG v2.0.22 (GNU/Linux)
mQENBF2ESysBCACw4/06u2L7vPsHsfNvI+h98llPbfLJ20fkf2bj8rM4cChRV0po
.......省略
4qAXe+TqCHYb2hWGA7RV3wf1MGATMkSc3+g5/d3Qz2nLNt1b3vHXIYuJJM2ymPf
=d+xw
-----END PGP PUBLIC KEY BLOCK-----
[root@elk-node1 .gnupg]# scp zjz.pubkey 192.168.40.211:/data (传给211)
root@192.168.40.211's password:
zjz.pubkey 100% 1715 1.4MB/s 00:00
211机子也生成自己的公钥(方法同上)
#mv /etc/fstab /data
[root@elk-node2 ~]# cd /data/
[root@elk-node2 data]# ls
fstab zjz.pubkey
[root@elk-node2 data]# gpg ---import /data/zjz.pubkey (导入132的公钥)
gpg: invalid option "---import"
[root@elk-node2 data]# gpg --import /data/zjz.pubkey
gpg: 密钥 5686364C:公钥“zjzzjz (github) <fan@qq.com>”已导入
gpg: 合计被处理的数量:1
gpg: 已导入:1 (RSA: 1)
[root@elk-node2 data]# gpg --list-keys (列出当前有的公钥)
/root/.gnupg/pubring.gpg
------------------------
pub 2048R/3CE68E6E 2019-09-20
uid qianfeng (211)
sub 2048R/C889590A 2019-09-20
pub 2048R/5686364C 2019-09-20
uid zjzzjz (github) <fan@qq.com>(132)
sub 2048R/59953D36 2019-09-20
[root@elk-node2 .gnupg]# cd
[root@elk-node2 ~]# cd /data/
[root@elk-node2 data]# ls
fstab zjz.pubkey
[root@elk-node2 data]# gpg -e -r zjz.pubkey fstab (使用132机子公钥加密fstab)
gpg: 59953D36:没有证据表明这把密钥真的属于它所声称的持有者(之前创建公钥没输入密码)
pub 2048R/59953D36 2019-09-20 zjzzjz (github) <fan@qq.com>
主钥指纹: 23D3 6C44 4395 19F1 36EE 2069 998D 2612 5686 364C
子钥指纹: 7DA0 92A3 0D4F D483 91DE 469C 5543 AFC5 5995 3D36
这把密钥并不一定属于用户标识声称的那个人。如果您真的知道自
己在做什么,您可以在下一个问题回答 yes。
无论如何还是使用这把密钥吗?(y/N)y
[root@elk-node2 data]# ls
es-data fstab fstab.gpg zjz.pubkey
[root@elk-node2 data]# scp fstab.gpg 192.168.40.132:/data/
[root@elk-node1 data]# gpg -d fstab.gpg (自动用私钥解密)
gpg: encrypted with 2048-bit RSA key, ID 59953D36, created 2019-09-20
。。。。。。省略
UUID=c58d6c48-302e-4c42-a700-7590de2926f6 /boot xfs defaults 0 0
/dev/mapper/centos-swap swap swap defaults 0 0
到此实验成功
注:成密钥时候卡住了:解决办法(新开一个终端)
#yum -y install rng-tools
#rngd -r /dev/urandom
3、ssh-genkey
二、对称密码运用
211机子:
[root@elk-node2 ~]# mkdir /aaa
[root@elk-node2 ~]# cd /aaa/
[root@elk-node2 aaa]# vim bb
[root@elk-node2 aaa]# ls
bb
[root@elk-node2 aaa]# gpg -c bb
[root@elk-node2 aaa]# ls
bb bb.gpg

输入两次密码
132机子:
[root@elk-node1 ~]# scp -r 192.168.40.211:/aaa/bb.gpg .
root@192.168.40.211's password:
bb.gpg 100% 46 0.5KB/s 00:00
[root@elk-node1 ~]# ls
anaconda-ks.cfg bb.gpg elsfk.sh homework2.0.sh
[root@elk-node1 ~]# cat bb.gpg
뺲(#K·⇝ԯHAOᄆ>¨¢±琳Y㶽6Xn/[root@elk-node1 ~]#
[root@elk-node1 ~]# gpg -o bb -d bb.gpg
[root@elk-node1 ~]# gpg -o bb -d bb.gpg

gpg: CAST5 encrypted data
gpg: encrypted with 1 passphrase
gpg: WARNING: message was not integrity protected
[root@elk-node1 ~]# ls
anaconda-ks.cfg bb bb.gpg elsfk.sh homework2.0.sh
[root@elk-node1 ~]# cat bb
2019