在linux环境抓包,此次用百度来抓包测试分析TCP的三次握手四次挥手
同一个客户端开启两个窗口
- 一个窗口执行 tcpdump -nn -i eth0 port 80 ,开启抓包监听
- 另一个窗口访问www.baidu.com
[root@localhost ~]# tcpdump -nn -i eth0 port 80 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 06:59:50.264655 IP 192.168.64.128.60592 > 180.101.49.11.80: Flags [S], seq 4130871516, win 14600, options [mss 1460,sackOK,TS val 4294934992 ecr 0,nop,wscale 6], length 0 06:59:50.293444 IP 180.101.49.11.80 > 192.168.64.128.60592: Flags [S.], seq 528643112, ack 4130871517, win 64240, options [mss 1460], length 0 06:59:50.293475 IP 192.168.64.128.60592 > 180.101.49.11.80: Flags [.], ack 1, win 14600, length 0 06:59:50.293642 IP 192.168.64.128.60592 > 180.101.49.11.80: Flags [P.], seq 1:173, ack 1, win 14600, length 172 06:59:50.293838 IP 180.101.49.11.80 > 192.168.64.128.60592: Flags [.], ack 173, win 64240, length 0 06:59:50.311657 IP 180.101.49.11.80 > 192.168.64.128.60592: Flags [.], seq 1:1461, ack 173, win 64240, length 1460 06:59:50.311672 IP 192.168.64.128.60592 > 180.101.49.11.80: Flags [.], ack 1461, win 17520, length 0 06:59:50.311706 IP 180.101.49.11.80 > 192.168.64.128.60592: Flags [P.], seq 1461:2782, ack 173, win 64240, length 1321 06:59:50.311710 IP 192.168.64.128.60592 > 180.101.49.11.80: Flags [.], ack 2782, win 20440, length 0 06:59:50.311898 IP 192.168.64.128.60592 > 180.101.49.11.80: Flags [F.], seq 173, ack 2782, win 20440, length 0 06:59:50.312100 IP 180.101.49.11.80 > 192.168.64.128.60592: Flags [.], ack 174, win 64239, length 0 06:59:50.330974 IP 180.101.49.11.80 > 192.168.64.128.60592: Flags [FP.], seq 2782, ack 174, win 64239, length 0 06:59:50.330991 IP 192.168.64.128.60592 > 180.101.49.11.80: Flags [.], ack 2783, win 20440, length 0 ^C 13 packets captured 14 packets received by filter 0 packets dropped by kernel [root@localhost ~]#
开启监听后访问百度
[root@localhost ~]# curl www.baidu.com
<!DOCTYPE html>
<!--STATUS OK--><html> <head><meta http-equiv=content-type content=text/html;charset=utf-8><meta http-equiv=X-UA-Compatible content=IE=Edge><meta content=always name=referrer><link rel=stylesheet type=text/css href=http://s1.bdstatic.com/r/www/cache/bdorz/baidu.min.css><title>百度一下,你就知道</title></head> <body link=#0000cc> <div id=wrapper> <div id=head> <div class=head_wrapper> <div class=s_form> <div class=s_form_wrapper> <div id=lg> <img hidefocus=true src=//www.baidu.com/img/bd_logo1.png width=270 height=129> </div> <form id=form name=f action=//www.baidu.com/s class=fm> <input type=hidden name=bdorz_come value=1> <input type=hidden name=ie value=utf-8> <input type=hidden name=f value=8> <input type=hidden name=rsv_bp value=1> <input type=hidden name=rsv_idx value=1> <input type=hidden name=tn value=baidu><span class="bg s_ipt_wr"><input id=kw name=wd class=s_ipt value maxlength=255 autocomplete=off autofocus></span><span class="bg s_btn_wr"><input type=submit id=su value=百度一下 class="bg s_btn"></span> </form> </div> </div> <div id=u1> <a href=http://news.baidu.com name=tj_trnews class=mnav>新闻</a> <a href=http://www.hao123.com name=tj_trhao123 class=mnav>hao123</a> <a href=http://map.baidu.com name=tj_trmap class=mnav>地图</a> <a href=http://v.baidu.com name=tj_trvideo class=mnav>视频</a> <a href=http://tieba.baidu.com name=tj_trtieba class=mnav>贴吧</a> <noscript> <a href=http://www.baidu.com/bdorz/login.gif?login&tpl=mn&u=http%3A%2F%2Fwww.baidu.com%2f%3fbdorz_come%3d1 name=tj_login class=lb>登录</a> </noscript> <script>document.write('<a href="http://www.baidu.com/bdorz/login.gif?login&tpl=mn&u='+ encodeURIComponent(window.location.href+ (window.location.search === "" ? "?" : "&")+ "bdorz_come=1")+ '" name="tj_login" class="lb">登录</a>');</script> <a href=//www.baidu.com/more/ name=tj_briicon class=bri style="display: block;">更多产品</a> </div> </div> </div> <div id=ftCon> <div id=ftConw> <p id=lh> <a href=http://home.baidu.com>关于百度</a> <a href=http://ir.baidu.com>About Baidu</a> </p> <p id=cp>©2017 Baidu <a href=http://www.baidu.com/duty/>使用百度前必读</a> <a href=http://jianyi.baidu.com/ class=cp-feedback>意见反馈</a> 京ICP证030173号 <img src=//www.baidu.com/img/gs.gif> </p> </div> </div> </div> </body> </html>
[root@localhost ~]#
接下来重点分析一下客户端和服务端之间tcp协议具体是怎么进行的,简化后,我们逐行分析,P.S. 我本地是192.168.64.128开启了60592端口(即client) 百度是180.101.49.11开启80端口(即server),简化后如下
client > server: Flags [S], seq 4130871516, win 14600, options [mss 1460,sackOK,TS val 4294934992 ecr 0,nop,wscale 6], length 0 server > client : Flags [S.], seq 528643112, ack 4130871517, win 64240, options [mss 1460], length 0 client > server: Flags [.], ack 1, win 14600, length 0 client > server: Flags [P.], seq 1:173, ack 1, win 14600, length 172 server > client : Flags [.], ack 173, win 64240, length 0 server > client : Flags [.], seq 1:1461, ack 173, win 64240, length 1460 client > server: Flags [.], ack 1461, win 17520, length 0 server > client : Flags [P.], seq 1461:2782, ack 173, win 64240, length 1321 client > server: Flags [.], ack 2782, win 20440, length 0 client > server: Flags [F.], seq 173, ack 2782, win 20440, length 0 server > client : Flags [.], ack 174, win 64239, length 0 server > client : Flags [FP.], seq 2782, ack 174, win 64239, length 0 client > server: Flags [.], ack 2783, win 20440, length 0
man tcpdump后查看Flag对应的意义如下
查看Flags的解释
Flags are some combination of S (SYN), F (FIN), P (PUSH), R (RST), W (ECN CWR) or E (ECN-Echo), or a single ‘.’ (no flags).
即
Flags[S] ----------->SYN
Flags[.] ----------->无符号,即ACK(acknowledge确认)
Flags[P] ----------->PUSH 推送数据
Flags[F] ----------->FIN,发起终止信号
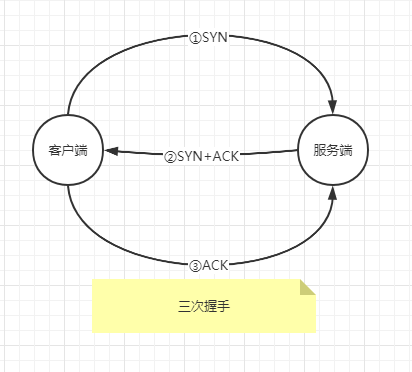
一、握手
1)第一行中客户端向服务端发送SYN,发起建立连接请求--------------------------------------------------------------------------------第一次握手
2)第二行服务端回复客户端SYNC+ACK,第二次握手,此时能确定客户端的输出能力和服务端的输入接收能力----------第二次握手
3)第三行客户端向服务器发送ACK,此时能确定服务端的输出能力和客户端的输入接收能力---------------------------------第三次握手
二、.传输数据,数据量过大的话会进行数据拆包传输
1)第四行中客户端开始向服务端发起PUSH,即发送实际数据包了
2)第五行中服务端向客户端发送ACK,确认收到了
3)第六行中服务端向客户端发送数据包,返回响应数据
4)第七行中客户端向服务器发送ACK,确认收到响应数据
5)第八行服务器又向客户端发送PUSH,又响应发送了一个数据包,数据包拆分成小的进行传输
6)第九行客户端向服务器确认收到了数据包
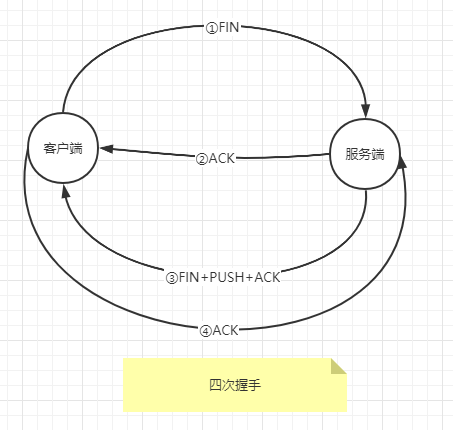
三、挥手
1)第十行客户端向服务器端发送FIN,发起断开请求--------------------------------------------第一次挥手
2)第十一行服务端确定收到了客户端消息--------------------------------------------------------第二次挥手
3)第十二行服务器向客户端发送FIN+PUSH+ACK,服务端也同意断开--------------------第三次挥手
4)第十三行客户端收到了服务端的消息后也通知服务端已收到要求了--------------------第四次挥手
总结:
- 三次握手是为了确定客户端和服务端双方的输入输出能力,从而判断是否能建立稳定的连接
- 四次挥手是为了确定双方都同意断开,将为连接而分配的空间释放掉
- 每次请求都会有响应,即使没数据都会用ACK来确认收到了消息
- 连接是什么? 双方都分配空间,为此次连接生成一个fd(文件表述符)
- socket是什么意思? socket中文翻译是“套接字”,“套”的是什么呢?ip:port + ip:port (客户端的ip和端口 套接 服务端的ip和端口)