Hadoop生态圈-使用FreeIPA安装Kerberos和LDAP
作者:尹正杰
版权声明:原创作品,谢绝转载!否则将追究法律责任。
有些大数据平台只是简单地通过防火墙来解决他们的网络安全问题。十分不信的的是,防火墙有一个假设的前提,它总假设“破坏者”都来自于外部,这通常是一个非常糟糕的假设。大多数真正具有破坏性的计算机犯罪事件都是由内部人员进行的。防火墙也有一个明显的缺点,因为它们限制了用户使用Internet的方式。(毕竟,防火墙只是一个不那么极端的例子,没有什么比没有连接到网络的计算机更安全 - 并且关机!)在许多地方,这些限制是不切实际和不可接受的。
一.网络安全框架协议Kerberos简介
1>.什么是Kerberos
Kerberos是一个网络认证的框架协议,它的命名灵感来自于希腊神话中一只三头犬守护兽,寓意其拥有强大的保护能力。Kerberos协议通过强大密钥系统为Server(服务端)和Client(客户端)应用程序之间提供强大的通信加密和认证服务。在使用Kerberos协议认证的集群中,Client不会直接和他的Server服务进行通信认证,而是通过KDC(key Distribution Center)这样一个独立的服务来完成互相之间的认证。同时Kerberos 还能将服务之间的全部通信进行加密以保证其隐私于完整性。
Kerberos由麻省理工学院创建,作为解决这些网络安全问题的解决方案。Kerberos协议使用强加密技术,以便客户端可以通过不安全的网络连接向服务器(反之亦然)证明其身份。在客户端和服务器使用Kerberos证明其身份后,他们还可以加密所有通信,以确保在业务开展时的隐私和数据完整性。详情请参考:https://web.mit.edu/kerberos/。
2>.Kerberos核心概念
Kerberos协议中有一些重要的概念,了解这些概念有助于我们理解Kerberos的认证过程。
2.1>.KDC(Key Distribution Centor):
KDC用于验证各个模块,是统一认证服务。
2.2>.Kerberos KDC Server:
KDC所在的服务器。
2.3>.Kerberos Client
任何一个需要通过KDC认证的机器(或模块)。
2.4>.Principal
用于验证一个用户或者一个Service的唯一标识,相当于一个账号,需要为其设置密码。
2.5>.Keytab
包含一个或多个Principal以及其密码的文件,可用于用户登录。
2.6>.Relam
由KDC以及多个Kerberos Client组成的网络。
2.7>.KDC Admin Account
KDC中拥有管理权限的用户(例如添加,修改,删除Principal)。
2.8>.Authentication Sever(AS)
用于初始化认证,并生成Ticket Granting Ticket(TGT)。
2.9>.Ticket Granting Server(TGS)
在TGT的基础上生成Service Ticket。一般情况下AS和TGS都在KDC的Server上。
3>.Kerberos的认证流程
Kerberos协议主要由Key分发中心(即KDC,全称“Key Distribution Centor”),服务提供者(Server)和用户(User)三部分组成,它的认证过程如下图所示:
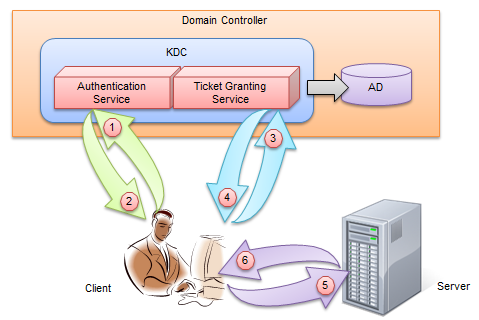
第 1 步:
client(一个User或者一个Service)会用Pricipal到Authentication Sever(AS)去认证,希望获取访问server的权限。
第 2 步:
kerberos得到了这个消息,首先得判断client是否是可信赖的,也就是白名单黑名单的说法。这就是AS服务完成的工作,通过在AD中存储黑名单和白名单来区分client。成功后,返回AS返回TGT给client。
第 3 步:
这是只有AS和这个Principal的使用者可以识别该TGT。在拿到加密的TGT之后,client(User或者Service)会使用Principal的Key来解密TGT。并使用解密后的TGT继续向kerberos请求,希望获取访问server的权限。
第 4 步:
kerberos又一次得到了这个消息,这时候通过client(User或者Service)消息中的TGT(注意:此时的TGT是第三步中解密后的TGT,并不是第二步的TGT哟!),判断出了client拥有了这个权限,给了client访问server的权限Server Ticket。
第 5~6 步:
client得到希望访问的Server Ticket后,终于可以成功访问该Server。需要注意的是,得到的这个Server Ticket只是针对这台Server,其他server需要继续向TGS申请(因为每台服务器都有自己的Server Ticket哟!)。在Kerberos认证的集群中,只有拿着这个Service Ticket才可以访问真正的Server从而实现自己的业务逻辑。
4>.Kerberos的优点
分析整个Kerberos的认证过程之后,我们来总结一下Kerberos都有哪些优点:
4.1>.较高的Performance
虽然我们一再地说Kerberos是一个涉及到3方的认证过程:Client、Server、KDC。但是一旦Client获得用过访问某个Server的Ticket,该Server就能根据这个Ticket实现对Client的验证,而无须KDC的再次参与。和传统的基于Windows NT 4.0的每个完全依赖Trusted Third Party的NTLM比较,具有较大的性能提升。
4.2>.实现了双向验证(Mutual Authentication)
传统的NTLM认证基于这样一个前提:Client访问的远程的Service是可信的、无需对于进行验证,所以NTLM不曾提供双向验证的功能。这显然有点理想主义,为此Kerberos弥补了这个不足:Client在访问Server的资源之前,可以要求对Server的身份执行认证。
4.3>.对Delegation的支持
Impersonation和Delegation是一个分布式环境中两个重要的功能。Impersonation允许Server在本地使用Logon 的Account执行某些操作,Delegation需用Server将logon的Account带入到另过一个Context执行相应的操作。NTLM仅对Impersonation提供支持,而Kerberos通过一种双向的、可传递的(Mutual 、Transitive)信任模式实现了对Delegation的支持。
4.4>.互操作性(Interoperability)
Kerberos最初由MIT首创,现在已经成为一行被广泛接受的标准。所以对于不同的平台可以进行广泛的互操作。
二.使用FreeIPA安装Kerberos和LDAP
Kerberos协议只是一种协议标准的框架,而MIT Kerberos则是实现了该协议的认证服务,是Kerberos协议的物理载体。将它于Hadoop服务进行集成便能够很好地解决安全性不足的问题。除了需要安装MIT Kerberos之外,我们还需要安装LDAP。Kerberos和LDAP服务这类基础设施组件虽好,但他们手动安装起来都十分的繁琐。这种手动安装的方式既低效又不利于管理。因此我们可以通过FreeIPA来安装这些基础组件。
FreeIPA是一个集成的安装信息管理解决方案。它整合了LDAP,Kerberos,NTP,Bind,Apache和Tomcat等核心软件包,从而形成来一个以LDAP为数据存储后端,Kerberos为验证前端,Bind为主机识别,同时还提供统一的命令行管理工具和WEB管理界面的集成信息管理系统。FreeIPA建立在著名的开源组件和标准协议之上,具有易于管理,安装和配置任务自动化的特点。FreeIPA是平台基础设施的一记强力组合拳,它就像大数据版本的XAMPP一样,为我们在基础设施安装于管理上带来了巨大的便利。FreeIPA它不仅继承了LDAP和Kerberos这两个非常重要的组件,并且在这些服务之上还创建了一个CLI接口。通过这层接口我们能够轻松地完成一系列动作,例如对Kerberos用户的管理工作。值得注意的是,当我们通过FreeIPA创建一个Kerberos用户的同时,他还会自动创建一个相同的LADP用户和Linux服务器用户,这意味着什么呢?这意味着从逻辑上来看,我们创建了一个Kerberos用户,而从物理上其实FreeIPA帮我们创建了三个用户,并且它能够保证这三个用户事物的一致性。这是一项非常重要且了不起的特性,它在某种程度上帮我们实现了用户的统一。
FreeIPA服务分为IPA-Server和IPA-Client两个部分,IPA-Server包含了所有集成的组件以及Web UI管理控制台,可以说它是控制于验证的中心服务。我们需要单独准备一台服务器来安装IPA-Server程序,这台服务器不能属于任何由Ambari管理的集群节点(本篇博客我使用的节点“node100.yinzhengjie.com”来部署)。这是因为安装IPA-Server的程序中,安装程序会将其所在的服务器地址注册到DNS服务中,而Ambari的集群节点也会进行相同的注册动作。如果一台服务器同时安装来IPA-Server并注册成为Ambari节点,就会造成名称的冲突,导致在注册DNS的过程中失败。IP-Server并注册成为Ambari节点,就会造成名称的冲突,导致在注册DNS的过程中失败。IPA-Client于IPA-Server则恰恰相反,Ambari管理的所有集群节点服务器上都必须安装IPA-Client。
XAMPP是完全免费且易于安装的Apache发行版,其中包含MariaDB、PHP和Perl。XAMPP开放源码包的设置让安装和使用出奇容易。是开源基础组件的一记强力组合拳。官网地址:https://www.apachefriends.org/zh_cn/index.html
温馨提示:在部署前建议直接关闭到selinux和firewalld服务,FreeIPA文档参考链接为:https://www.globo.tech/learning-center/install-freeipa-centos-7/。
1>.扩充密钥长度
Kerberos需要使用256为的AES加密算法,而JRE默认中的密钥长度比较短,并且不足以支撑。所以我们需要升级集群中所有服务器节点JRE的安全策略,使其能够解除密钥长度的限制。修改的方式是下载并替换JRE中的Unlimited JCEPolicy文件。以JDK1.8为例,下载地址为:https://www.oracle.com/technetwork/java/javase/downloads/jce8-download-2133166.html。

将其解压之后会得到“local_policy.jar”和“US_export_policy.jar”两个jar文件,将它们复制到每台服务器JDK路径下到“jre/lib/security”目录下(例如拷贝到“/yinzhengjie/softwares/jdk/jre/lib/security/”,点击下面的按钮查看详细的操作)即可完成安全策略的升级。
[root@node101 download]# ll total 12 -rw-r--r-- 1 root root 8409 Dec 12 13:58 jce_policy-8.zip [root@node101 download]# unzip jce_policy-8.zip Archive: jce_policy-8.zip creating: UnlimitedJCEPolicyJDK8/ inflating: UnlimitedJCEPolicyJDK8/local_policy.jar inflating: UnlimitedJCEPolicyJDK8/README.txt inflating: UnlimitedJCEPolicyJDK8/US_export_policy.jar [root@node101 download]# [root@node101 download]# ll total 16 -rw-r--r-- 1 root root 8409 Dec 12 13:58 jce_policy-8.zip drwxrwxr-x 2 root root 4096 Dec 21 2013 UnlimitedJCEPolicyJDK8 [root@node101 download]# [root@node101 UnlimitedJCEPolicyJDK8]# ll /yinzhengjie/softwares/jdk/jre/lib/security/ total 172 -rw-r--r--. 1 10 143 4054 Oct 6 20:52 blacklist -rw-r--r--. 1 10 143 1273 Oct 6 20:52 blacklisted.certs -rw-r--r--. 1 10 143 106896 Oct 6 20:52 cacerts -rw-r--r--. 1 10 143 2466 Oct 6 20:52 java.policy -rw-r--r--. 1 10 143 41516 Oct 6 20:52 java.security -rw-r--r--. 1 10 143 98 Oct 6 20:52 javaws.policy drwxr-xr-x. 4 10 143 4096 Oct 6 20:52 policy -rw-r--r--. 1 10 143 0 Oct 6 20:52 trusted.libraries [root@node101 UnlimitedJCEPolicyJDK8]# [root@node101 UnlimitedJCEPolicyJDK8]# scp local_policy.jar US_export_policy.jar /yinzhengjie/softwares/jdk/jre/lib/security/ [root@node101 UnlimitedJCEPolicyJDK8]# [root@node101 UnlimitedJCEPolicyJDK8]# ll /yinzhengjie/softwares/jdk/jre/lib/security/ total 180 -rw-r--r--. 1 10 143 4054 Oct 6 20:52 blacklist -rw-r--r--. 1 10 143 1273 Oct 6 20:52 blacklisted.certs -rw-r--r--. 1 10 143 106896 Oct 6 20:52 cacerts -rw-r--r--. 1 10 143 2466 Oct 6 20:52 java.policy -rw-r--r--. 1 10 143 41516 Oct 6 20:52 java.security -rw-r--r--. 1 10 143 98 Oct 6 20:52 javaws.policy -rw-r--r-- 1 root root 3035 Dec 12 14:03 local_policy.jar drwxr-xr-x. 4 10 143 4096 Oct 6 20:52 policy -rw-r--r--. 1 10 143 0 Oct 6 20:52 trusted.libraries -rw-r--r-- 1 root root 3023 Dec 12 14:03 US_export_policy.jar [root@node101 UnlimitedJCEPolicyJDK8]#

[root@node101 ~]# cat `which xrsync.sh ` #!/bin/bash #@author :yinzhengjie #blog:http://www.cnblogs.com/yinzhengjie #EMAIL:y1053419035@qq.com #判断用户是否传参 if [ $# -lt 1 ];then echo "请输入参数"; exit fi #获取文件路径 file=$@ #获取子路径 filename=`basename $file` #获取父路径 dirpath=`dirname $file` #获取完整路径 cd $dirpath fullpath=`pwd -P` #同步文件到DataNode for (( i=102;i<=103;i++ )) do #使终端变绿色 tput setaf 2 echo =========== node${i}.yinzhengjie.org.cn : $file =========== #使终端变回原来的颜色,即白灰色 tput setaf 7 #远程执行命令 rsync -lr $filename `whoami`@node${i}.yinzhengjie.org.cn:$fullpath #判断命令是否执行成功 if [ $? == 0 ];then echo "命令执行成功" fi done [root@node101 ~]#

[root@node101 ~]# cat `which xcall.sh` #!/bin/bash #@author :yinzhengjie #blog:http://www.cnblogs.com/yinzhengjie #EMAIL:y1053419035@qq.com #判断用户是否传参 if [ $# -lt 1 ];then echo "请输入参数" exit fi #获取用户输入的命令 cmd=$@ for (( i=101;i<=103;i++ )) do #使终端变绿色 tput setaf 2 echo ============= node${i}.yinzhengjie.org.cn : $cmd ============ #使终端变回原来的颜色,即白灰色 tput setaf 7 #远程执行命令 ssh node${i}.yinzhengjie.org.cn $cmd #判断命令是否执行成功 if [ $? == 0 ];then echo "命令执行成功" fi done [root@node101 ~]#

[root@node101 ~]# cat /etc/hosts | grep yinzhengjie 172.30.1.100 node100.yinzhengjie.org.cn 172.30.1.101 node101.yinzhengjie.org.cn 172.30.1.102 node102.yinzhengjie.org.cn 172.30.1.103 node103.yinzhengjie.org.cn [root@node101 ~]# [root@node101 ~]# [root@node101 ~]# xrsync.sh /etc/hosts =========== node102.yinzhengjie.org.cn : /etc/hosts =========== 命令执行成功 =========== node103.yinzhengjie.org.cn : /etc/hosts =========== 命令执行成功 [root@node101 ~]#

[root@node101 ~]# [root@node101 ~]# xrsync.sh /yinzhengjie/softwares/jdk/jre/lib/security/ =========== node102.yinzhengjie.org.cn : /yinzhengjie/softwares/jdk/jre/lib/security/ =========== 命令执行成功 =========== node103.yinzhengjie.org.cn : /yinzhengjie/softwares/jdk/jre/lib/security/ =========== 命令执行成功 [root@node101 ~]#

[root@node101 ~]# xcall.sh cat /etc/hosts | grep yinzhengjie ============= node101.yinzhengjie.org.cn : cat /etc/hosts ============ 172.30.1.100 node100.yinzhengjie.org.cn 172.30.1.101 node101.yinzhengjie.org.cn 172.30.1.102 node102.yinzhengjie.org.cn 172.30.1.103 node103.yinzhengjie.org.cn ============= node102.yinzhengjie.org.cn : cat /etc/hosts ============ 172.30.1.100 node100.yinzhengjie.org.cn 172.30.1.101 node101.yinzhengjie.org.cn 172.30.1.102 node102.yinzhengjie.org.cn 172.30.1.103 node103.yinzhengjie.org.cn ============= node103.yinzhengjie.org.cn : cat /etc/hosts ============ 172.30.1.100 node100.yinzhengjie.org.cn 172.30.1.101 node101.yinzhengjie.org.cn 172.30.1.102 node102.yinzhengjie.org.cn 172.30.1.103 node103.yinzhengjie.org.cn [root@node101 ~]#

[root@node101 ~]# xcall.sh ls -l /yinzhengjie/softwares/jdk/jre/lib/security/ ============= node101.yinzhengjie.org.cn : ls -l /yinzhengjie/softwares/jdk/jre/lib/security/ ============ total 180 -rw-r--r--. 1 10 143 4054 Oct 6 20:52 blacklist -rw-r--r--. 1 10 143 1273 Oct 6 20:52 blacklisted.certs -rw-r--r--. 1 10 143 106896 Oct 6 20:52 cacerts -rw-r--r--. 1 10 143 2466 Oct 6 20:52 java.policy -rw-r--r--. 1 10 143 41516 Oct 6 20:52 java.security -rw-r--r--. 1 10 143 98 Oct 6 20:52 javaws.policy -rw-r--r-- 1 root root 3035 Dec 12 14:03 local_policy.jar drwxr-xr-x. 4 10 143 4096 Oct 6 20:52 policy -rw-r--r--. 1 10 143 0 Oct 6 20:52 trusted.libraries -rw-r--r-- 1 root root 3023 Dec 12 14:03 US_export_policy.jar 命令执行成功 ============= node102.yinzhengjie.org.cn : ls -l /yinzhengjie/softwares/jdk/jre/lib/security/ ============ total 180 -rw-r--r-- 1 root root 4054 Dec 12 14:09 blacklist -rw-r--r-- 1 root root 1273 Dec 12 14:09 blacklisted.certs -rw-r--r-- 1 root root 106896 Dec 12 14:09 cacerts -rw-r--r-- 1 root root 2466 Dec 12 14:09 java.policy -rw-r--r-- 1 root root 41516 Dec 12 14:09 java.security -rw-r--r-- 1 root root 98 Dec 12 14:09 javaws.policy -rw-r--r-- 1 root root 3035 Dec 12 14:09 local_policy.jar drwxr-xr-x. 4 root root 4096 Dec 5 16:23 policy -rw-r--r-- 1 root root 0 Dec 12 14:09 trusted.libraries -rw-r--r-- 1 root root 3023 Dec 12 14:09 US_export_policy.jar 命令执行成功 ============= node103.yinzhengjie.org.cn : ls -l /yinzhengjie/softwares/jdk/jre/lib/security/ ============ total 180 -rw-r--r-- 1 root root 4054 Dec 12 14:09 blacklist -rw-r--r-- 1 root root 1273 Dec 12 14:09 blacklisted.certs -rw-r--r-- 1 root root 106896 Dec 12 14:09 cacerts -rw-r--r-- 1 root root 2466 Dec 12 14:09 java.policy -rw-r--r-- 1 root root 41516 Dec 12 14:09 java.security -rw-r--r-- 1 root root 98 Dec 12 14:09 javaws.policy -rw-r--r-- 1 root root 3035 Dec 12 14:09 local_policy.jar drwxr-xr-x. 4 root root 4096 Dec 5 16:23 policy -rw-r--r-- 1 root root 0 Dec 12 14:09 trusted.libraries -rw-r--r-- 1 root root 3023 Dec 12 14:09 US_export_policy.jar 命令执行成功 [root@node101 ~]#

[root@node101 ~]# scp jce_policy-8.zip jdk-8u191-linux-x64.tar.gz node100.yinzhengjie.org.cn:~ root@node100.yinzhengjie.org.cn's password: jce_policy-8.zip 100% 8409 8.2KB/s 00:00 jdk-8u191-linux-x64.tar.gz 100% 183MB 182.9MB/s 00:01 [root@node101 ~]#

[root@node100 ~]# yum -y install unzip zip Loaded plugins: fastestmirror Loading mirror speeds from cached hostfile * base: mirrors.huaweicloud.com * extras: mirrors.huaweicloud.com * updates: mirrors.huaweicloud.com Resolving Dependencies --> Running transaction check ---> Package unzip.x86_64 0:6.0-19.el7 will be installed ---> Package zip.x86_64 0:3.0-11.el7 will be installed --> Finished Dependency Resolution Dependencies Resolved ================================================================================================================================= Package Arch Version Repository Size ================================================================================================================================= Installing: unzip x86_64 6.0-19.el7 base 170 k zip x86_64 3.0-11.el7 base 260 k Transaction Summary ================================================================================================================================= Install 2 Packages Total download size: 430 k Installed size: 1.1 M Downloading packages: (1/2): unzip-6.0-19.el7.x86_64.rpm | 170 kB 00:00:00 (2/2): zip-3.0-11.el7.x86_64.rpm | 260 kB 00:00:01 --------------------------------------------------------------------------------------------------------------------------------- Total 238 kB/s | 430 kB 00:00:01 Running transaction check Running transaction test Transaction test succeeded Running transaction Installing : zip-3.0-11.el7.x86_64 1/2 Installing : unzip-6.0-19.el7.x86_64 2/2 Verifying : unzip-6.0-19.el7.x86_64 1/2 Verifying : zip-3.0-11.el7.x86_64 2/2 Installed: unzip.x86_64 0:6.0-19.el7 zip.x86_64 0:3.0-11.el7 Complete! [root@node100 ~]#
[root@node100 ~]# mkdir -pv /yinzhengjie/softwares/ mkdir: created directory ‘/yinzhengjie’ mkdir: created directory ‘/yinzhengjie/softwares/’ [root@node100 ~]# [root@node100 ~]# [root@node100 ~]# ll total 187276 -rw-r--r--. 1 root root 8409 Dec 12 01:23 jce_policy-8.zip -rw-r--r--. 1 root root 191753373 Dec 12 01:23 jdk-8u191-linux-x64.tar.gz [root@node100 ~]# [root@node100 ~]# tar -zxf jdk-8u191-linux-x64.tar.gz -C /yinzhengjie/softwares/ [root@node100 ~]# ln -s /yinzhengjie/softwares/jdk1.8.0_191/ /yinzhengjie/softwares/jdk [root@node100 ~]# [root@node100 ~]# unzip jce_policy-8.zip Archive: jce_policy-8.zip creating: UnlimitedJCEPolicyJDK8/ inflating: UnlimitedJCEPolicyJDK8/local_policy.jar inflating: UnlimitedJCEPolicyJDK8/README.txt inflating: UnlimitedJCEPolicyJDK8/US_export_policy.jar [root@node100 ~]# [root@node100 ~]# cd UnlimitedJCEPolicyJDK8/ [root@node100 UnlimitedJCEPolicyJDK8]# cp local_policy.jar US_export_policy.jar /yinzhengjie/softwares/jdk/jre/lib/security/ [root@node100 UnlimitedJCEPolicyJDK8]# [root@node100 UnlimitedJCEPolicyJDK8]# ll /yinzhengjie/softwares/jdk/jre/lib/security/ total 180 -rw-r--r--. 1 10 143 4054 Oct 6 08:52 blacklist -rw-r--r--. 1 10 143 1273 Oct 6 08:52 blacklisted.certs -rw-r--r--. 1 10 143 106896 Oct 6 08:52 cacerts -rw-r--r--. 1 10 143 2466 Oct 6 08:52 java.policy -rw-r--r--. 1 10 143 41516 Oct 6 08:52 java.security -rw-r--r--. 1 10 143 98 Oct 6 08:52 javaws.policy -rw-r--r--. 1 root root 3035 Dec 12 01:31 local_policy.jar drwxr-xr-x. 4 10 143 4096 Oct 6 08:52 policy -rw-r--r--. 1 10 143 0 Oct 6 08:52 trusted.libraries -rw-r--r--. 1 root root 3023 Dec 12 01:31 US_export_policy.jar [root@node100 UnlimitedJCEPolicyJDK8]# [root@node100 UnlimitedJCEPolicyJDK8]# cd [root@node100 ~]# [root@node100 ~]# vi /etc/profile [root@node100 ~]# [root@node100 ~]# tail -3 /etc/profile #ADD JAVA_PATH JAVA_HOME=/yinzhengjie/softwares/jdk PATH=$PATH:$JAVA_HOME/bin [root@node100 ~]# [root@node100 ~]# source /etc/profile [root@node100 ~]# java -version java version "1.8.0_191" Java(TM) SE Runtime Environment (build 1.8.0_191-b12) Java HotSpot(TM) 64-Bit Server VM (build 25.191-b12, mixed mode) [root@node100 ~]#
2>.安装IPA-Server
在安装新软件包之前,最好确保服务器是最新的。作为root用户,使用带有-y标志的yum更新CentOS 7服务器,以避免提示为yes,如下所示:
[root@node100 ~]# hostname node100.yinzhengjie.com [root@node100 ~]# [root@node100 ~]# ip a | grep global | awk '{print $2}' | awk -F "/" '{print $1}' 172.30.1.100 [root@node100 ~]# [root@node100 ~]# yum -y update
在我们安装FreeIPA之前,我们必须采取一些基本步骤来配置我们的机器准备就绪。如果尚未安装,请使用以下命令安装我们的安装所需的软件包依赖项:
[root@node100 ~]# yum -y install bind-dyndb-ldap ipa-server-dns sssd-client sssd-common sssd-common-pac sssd-ldap sssd-proxy python-sssdconfig authconfig authconfig-gtk
我们还需要确保我们的服务器主机名可以解析为有效的IP地址,以便能够安装和访问FreeIPA。出于本教程的目的,我们将使用“172.30.1.100”作为我们服务器的IP地址,使用“
node100.yinzhengjie.com”作为我们的URL。当然我们也可以手动配置一下DNS地址。执行以下命令,替换为您自己的IP和URL以及DNS服务器:
[root@node100 ~]# echo 172.30.1.100 node100.yinzhengjie.com node100 >>/etc/hosts [root@node100 ~]# [root@node100 ~]# cat /etc/hostname node100.yinzhengjie.com [root@node100 ~]# [root@node100 ~]# cat /etc/resolv.conf | grep nameserver nameserver 127.0.0.1 nameserver 8.8.8.8 [root@node100 ~]#
现在我们准备安装实际的FreeIPA服务器了。再次使用yum安装必要的包。不要忘记所有命令必须以root用户身份完成:
[root@node100 ~]# yum -y install ipa-server Loaded plugins: fastestmirror Loading mirror speeds from cached hostfile * base: mirrors.huaweicloud.com * extras: mirrors.aliyun.com * updates: mirrors.huaweicloud.com Package ipa-server-4.6.4-10.el7.centos.x86_64 already installed and latest version #看来在上面安装依赖包的时候已经默认把它也给安装啦! Nothing to do [root@node100 ~]#
3>.配置IPA-Server
安装成功之后,就能执行“ipa-server”相关的shell命令了,FreeIPA的设置过程可能需要很长时间才能完成,具体取决于服务器规格。通过“ipa-server-install --setup-dns”命令开始安装过程:

[root@node100 ~]# ipa-server-install --setup-dns The log file for this installation can be found in /var/log/ipaserver-install.log #这里告诉了我们日志的存放位置。 ============================================================================== This program will set up the IPA Server. This includes: * Configure a stand-alone CA (dogtag) for certificate management * Configure the Network Time Daemon (ntpd) * Create and configure an instance of Directory Server * Create and configure a Kerberos Key Distribution Center (KDC) * Configure Apache (httpd) * Configure DNS (bind) * Configure the KDC to enable PKINIT To accept the default shown in brackets, press the Enter key. WARNING: conflicting time&date synchronization service 'chronyd' will be disabled in favor of ntpd Enter the fully qualified domain name of the computer on which you're setting up server software. Using the form <hostname>.<domainname> Example: master.example.com. Server host name [node100.yinzhengjie.com]: #指定名称,默认是当前的主机的FQDN Warning: skipping DNS resolution of host node100.yinzhengjie.com The domain name has been determined based on the host name. Please confirm the domain name [yinzhengjie.com]: #指定域名,默认是将FQDN的主机名去掉后的字符串当作域名 The kerberos protocol requires a Realm name to be defined. This is typically the domain name converted to uppercase. Please provide a realm name [YINZHENGJIE.COM]: #指定realm,就是将域名的字母大写 Certain directory server operations require an administrative user. This user is referred to as the Directory Manager and has full access to the Directory for system management tasks and will be added to the instance of directory server created for IPA. The password must be at least 8 characters long. Directory Manager password: #这里需要设置LDAP的管理员密码,密码长度至少为8个字符串。 Password (confirm): #这里需要重复上述的密码,如果你两次输入的密码不一致,会持续让你重置密码的哟! The IPA server requires an administrative user, named 'admin'. This user is a regular system account used for IPA server administration. IPA admin password: #指定IPA管理员的密码,这个密码切记要妥善保存,因为后续会多次使用它。 Password (confirm): Checking DNS domain yinzhengjie.com., please wait ... Please provide the IP address to be used for this host name: 172.30.1.100 #指定当前主机的IP地址即可! Enter an additional IP address, or press Enter to skip: Do you want to configure DNS forwarders? [yes]: #这里默认即可,默认为yes,咱们直接回车,下面很多选项都均可用默认回车,如果有需要修改的我会提示大家的! Following DNS servers are configured in /etc/resolv.conf: 172.30.1.1, 8.8.8.8 Do you want to configure these servers as DNS forwarders? [yes]: All DNS servers from /etc/resolv.conf were added. You can enter additional addresses now: Enter an IP address for a DNS forwarder, or press Enter to skip: Checking DNS forwarders, please wait ... DNS server 172.30.1.1: answer to query '. SOA' is missing DNSSEC signatures (no RRSIG data) Please fix forwarder configuration to enable DNSSEC support. (For BIND 9 add directive "dnssec-enable yes;" to "options {}") WARNING: DNSSEC validation will be disabled Do you want to search for missing reverse zones? [yes]: Do you want to create reverse zone for IP 172.30.1.100 [yes]: Please specify the reverse zone name [1.30.172.in-addr.arpa.]: Using reverse zone(s) 1.30.172.in-addr.arpa. The IPA Master Server will be configured with: Hostname: node100.yinzhengjie.com IP address(es): 172.30.1.100 Domain name: yinzhengjie.com Realm name: YINZHENGJIE.COM BIND DNS server will be configured to serve IPA domain with: Forwarders: 172.30.1.1, 8.8.8.8 Forward policy: only Reverse zone(s): 1.30.172.in-addr.arpa. Continue to configure the system with these values? [no]: yes #输入“yes”继续配置系统 The following operations may take some minutes to complete. Please wait until the prompt is returned. Adding [172.30.1.100 node100.yinzhengjie.com] to your /etc/hosts file Configuring NTP daemon (ntpd) [1/4]: stopping ntpd [2/4]: writing configuration [3/4]: configuring ntpd to start on boot [4/4]: starting ntpd Done configuring NTP daemon (ntpd). Configuring directory server (dirsrv). Estimated time: 30 seconds [1/44]: creating directory server instance [2/44]: enabling ldapi [3/44]: configure autobind for root [4/44]: stopping directory server [5/44]: updating configuration in dse.ldif [6/44]: starting directory server [7/44]: adding default schema [8/44]: enabling memberof plugin [9/44]: enabling winsync plugin [10/44]: configuring replication version plugin [11/44]: enabling IPA enrollment plugin [12/44]: configuring uniqueness plugin [13/44]: configuring uuid plugin [14/44]: configuring modrdn plugin [15/44]: configuring DNS plugin [16/44]: enabling entryUSN plugin [17/44]: configuring lockout plugin [18/44]: configuring topology plugin [19/44]: creating indices [20/44]: enabling referential integrity plugin [21/44]: configuring certmap.conf [22/44]: configure new location for managed entries [23/44]: configure dirsrv ccache [24/44]: enabling SASL mapping fallback [25/44]: restarting directory server [26/44]: adding sasl mappings to the directory [27/44]: adding default layout [28/44]: adding delegation layout [29/44]: creating container for managed entries [30/44]: configuring user private groups [31/44]: configuring netgroups from hostgroups [32/44]: creating default Sudo bind user [33/44]: creating default Auto Member layout [34/44]: adding range check plugin [35/44]: creating default HBAC rule allow_all [36/44]: adding entries for topology management [37/44]: initializing group membership [38/44]: adding master entry [39/44]: initializing domain level [40/44]: configuring Posix uid/gid generation [41/44]: adding replication acis [42/44]: activating sidgen plugin [43/44]: activating extdom plugin [44/44]: configuring directory to start on boot Done configuring directory server (dirsrv). Configuring Kerberos KDC (krb5kdc) [1/10]: adding kerberos container to the directory [2/10]: configuring KDC [3/10]: initialize kerberos container WARNING: Your system is running out of entropy, you may experience long delays [4/10]: adding default ACIs [5/10]: creating a keytab for the directory [6/10]: creating a keytab for the machine [7/10]: adding the password extension to the directory [8/10]: creating anonymous principal [9/10]: starting the KDC [10/10]: configuring KDC to start on boot Done configuring Kerberos KDC (krb5kdc). Configuring kadmin [1/2]: starting kadmin [2/2]: configuring kadmin to start on boot Done configuring kadmin. Configuring ipa-custodia [1/5]: Making sure custodia container exists [2/5]: Generating ipa-custodia config file [3/5]: Generating ipa-custodia keys [4/5]: starting ipa-custodia [5/5]: configuring ipa-custodia to start on boot Done configuring ipa-custodia. Configuring certificate server (pki-tomcatd). Estimated time: 3 minutes [1/28]: configuring certificate server instance [2/28]: exporting Dogtag certificate store pin [3/28]: stopping certificate server instance to update CS.cfg [4/28]: backing up CS.cfg [5/28]: disabling nonces [6/28]: set up CRL publishing [7/28]: enable PKIX certificate path discovery and validation [8/28]: starting certificate server instance [9/28]: configure certmonger for renewals [10/28]: requesting RA certificate from CA [11/28]: setting audit signing renewal to 2 years [12/28]: restarting certificate server [13/28]: publishing the CA certificate [14/28]: adding RA agent as a trusted user [15/28]: authorizing RA to modify profiles [16/28]: authorizing RA to manage lightweight CAs [17/28]: Ensure lightweight CAs container exists [18/28]: configure certificate renewals [19/28]: configure Server-Cert certificate renewal [20/28]: Configure HTTP to proxy connections [21/28]: restarting certificate server [22/28]: updating IPA configuration [23/28]: enabling CA instance [24/28]: migrating certificate profiles to LDAP [25/28]: importing IPA certificate profiles [26/28]: adding default CA ACL [27/28]: adding 'ipa' CA entry [28/28]: configuring certmonger renewal for lightweight CAs Done configuring certificate server (pki-tomcatd). Configuring directory server (dirsrv) [1/3]: configuring TLS for DS instance [2/3]: adding CA certificate entry [3/3]: restarting directory server Done configuring directory server (dirsrv). Configuring ipa-otpd [1/2]: starting ipa-otpd [2/2]: configuring ipa-otpd to start on boot Done configuring ipa-otpd. Configuring the web interface (httpd) [1/22]: stopping httpd [2/22]: setting mod_nss port to 443 [3/22]: setting mod_nss cipher suite [4/22]: setting mod_nss protocol list to TLSv1.0 - TLSv1.2 [5/22]: setting mod_nss password file [6/22]: enabling mod_nss renegotiate [7/22]: disabling mod_nss OCSP [8/22]: adding URL rewriting rules [9/22]: configuring httpd [10/22]: setting up httpd keytab [11/22]: configuring Gssproxy [12/22]: setting up ssl [13/22]: configure certmonger for renewals [14/22]: importing CA certificates from LDAP [15/22]: publish CA cert [16/22]: clean up any existing httpd ccaches [17/22]: configuring SELinux for httpd [18/22]: create KDC proxy config [19/22]: enable KDC proxy [20/22]: starting httpd [21/22]: configuring httpd to start on boot [22/22]: enabling oddjobd Done configuring the web interface (httpd). Configuring Kerberos KDC (krb5kdc) [1/1]: installing X509 Certificate for PKINIT Done configuring Kerberos KDC (krb5kdc). Applying LDAP updates Upgrading IPA:. Estimated time: 1 minute 30 seconds [1/10]: stopping directory server [2/10]: saving configuration [3/10]: disabling listeners [4/10]: enabling DS global lock [5/10]: disabling Schema Compat [6/10]: starting directory server [7/10]: upgrading server [8/10]: stopping directory server [9/10]: restoring configuration [10/10]: starting directory server Done. Restarting the KDC Configuring DNS (named) [1/12]: generating rndc key file WARNING: Your system is running out of entropy, you may experience long delays [2/12]: adding DNS container [3/12]: setting up our zone [4/12]: setting up reverse zone [5/12]: setting up our own record [6/12]: setting up records for other masters [7/12]: adding NS record to the zones [8/12]: setting up kerberos principal [9/12]: setting up named.conf [10/12]: setting up server configuration [11/12]: configuring named to start on boot [12/12]: changing resolv.conf to point to ourselves Done configuring DNS (named). Restarting the web server to pick up resolv.conf changes Configuring DNS key synchronization service (ipa-dnskeysyncd) [1/7]: checking status [2/7]: setting up bind-dyndb-ldap working directory [3/7]: setting up kerberos principal [4/7]: setting up SoftHSM [5/7]: adding DNSSEC containers [6/7]: creating replica keys [7/7]: configuring ipa-dnskeysyncd to start on boot Done configuring DNS key synchronization service (ipa-dnskeysyncd). Restarting ipa-dnskeysyncd Restarting named Updating DNS system records Configuring client side components Using existing certificate '/etc/ipa/ca.crt'. Client hostname: node100.yinzhengjie.com Realm: YINZHENGJIE.COM DNS Domain: yinzhengjie.com IPA Server: node100.yinzhengjie.com BaseDN: dc=yinzhengjie,dc=com Skipping synchronizing time with NTP server. New SSSD config will be created Configured sudoers in /etc/nsswitch.conf Configured /etc/sssd/sssd.conf trying https://node100.yinzhengjie.com/ipa/json [try 1]: Forwarding 'schema' to json server 'https://node100.yinzhengjie.com/ipa/json' trying https://node100.yinzhengjie.com/ipa/session/json [try 1]: Forwarding 'ping' to json server 'https://node100.yinzhengjie.com/ipa/session/json' [try 1]: Forwarding 'ca_is_enabled' to json server 'https://node100.yinzhengjie.com/ipa/session/json' Systemwide CA database updated. Adding SSH public key from /etc/ssh/ssh_host_ed25519_key.pub Adding SSH public key from /etc/ssh/ssh_host_rsa_key.pub Adding SSH public key from /etc/ssh/ssh_host_ecdsa_key.pub [try 1]: Forwarding 'host_mod' to json server 'https://node100.yinzhengjie.com/ipa/session/json' SSSD enabled Configured /etc/openldap/ldap.conf Configured /etc/ssh/ssh_config Configured /etc/ssh/sshd_config Configuring yinzhengjie.com as NIS domain. Client configuration complete. The ipa-client-install command was successful ============================================================================== Setup complete Next steps: 1. You must make sure these network ports are open: TCP Ports: * 80, 443: HTTP/HTTPS * 389, 636: LDAP/LDAPS * 88, 464: kerberos * 53: bind UDP Ports: * 88, 464: kerberos * 53: bind * 123: ntp 2. You can now obtain a kerberos ticket using the command: 'kinit admin' This ticket will allow you to use the IPA tools (e.g., ipa user-add) and the web user interface. Be sure to back up the CA certificates stored in /root/cacert.p12 These files are required to create replicas. The password for these files is the Directory Manager password [root@node100 ~]#
安装过程中,我踩过一些坑,我就不在这里一一举例了,如果你没有遇到错误,跟我上面的输出一致的话,那再好不过了。如果你也遇到了一些列问题的话,可以参考我踩过的坑,希望对你有帮助吧。参考链接:“https://www.cnblogs.com/yinzhengjie/p/10106337.html”。
4>.测试安装程序
经过一系列的安装于设置之后,IPA-Server就安装好了。现在可以进入IPA-Server附带的Web UI管理界面控制台一探究竟。打开浏览器,输入:“https://node100.yinzhengjie.com/ipa/ui/”,输入你自定义的freeIPA的管理员密码。

登录成功后,你可能会看到如下图所示的界面:
三.IPA-Server 管理控制台功能介绍
FreeIPA在整合了LDAP和Kerberos等众多核心软件包等同时,也提供了Web UI管理控制台,接下来我们会介绍它都提供了那些功能。
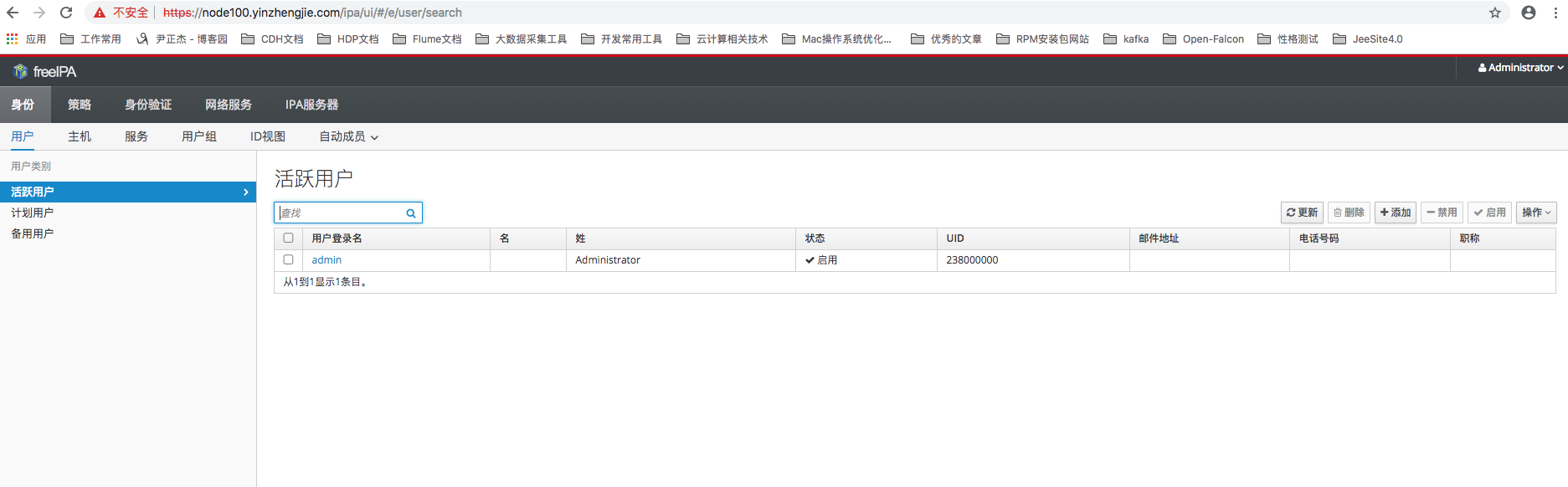
1>.用户管理
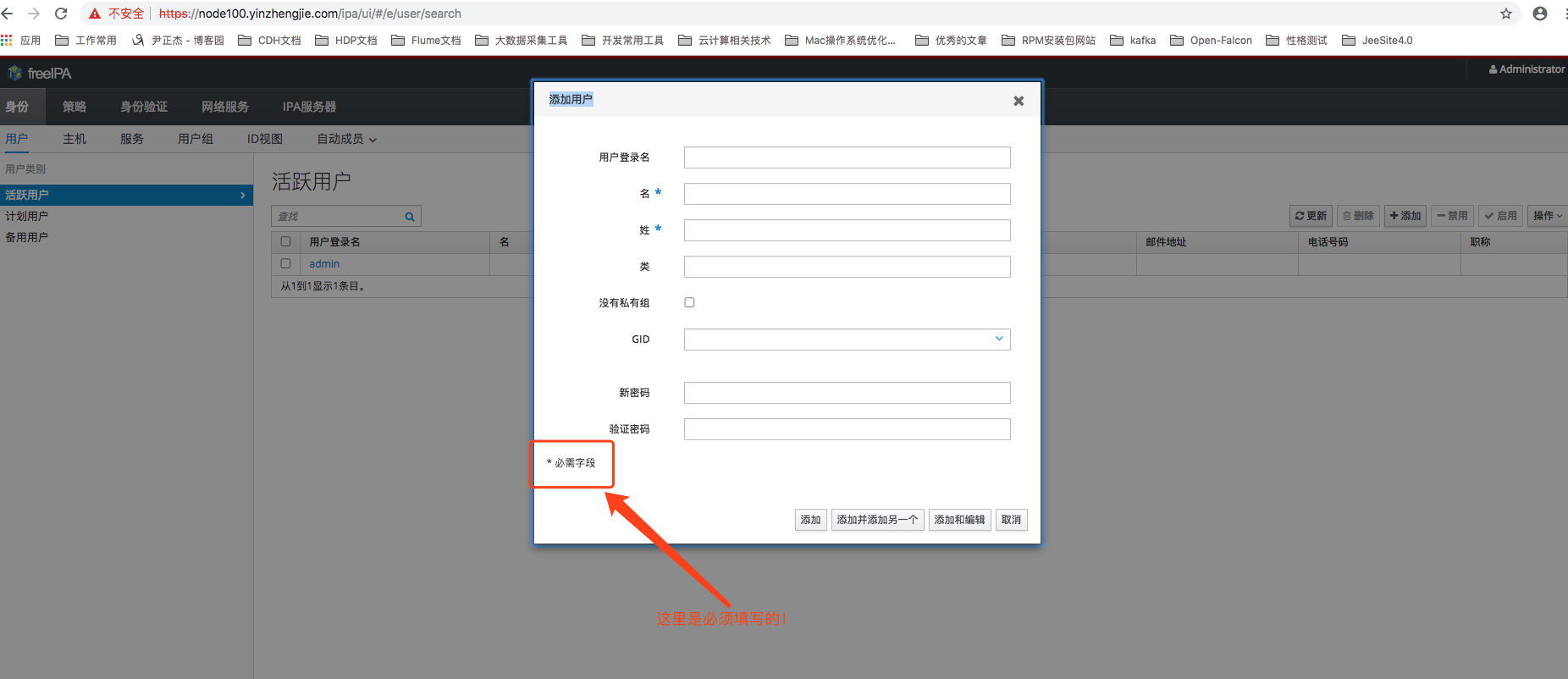
登入系统之后通过“身份”分类下都“用户”菜单能够进入到用户管理页面,通过用户列表能查看到系统内的所有Kerberos用户,可以发现经过刚才安装的过程中,系统已经创建了一个admin管理员用户,如下图所示。除此之外,这里还提供用户的创建,修改和删除功能。单击Add按钮打开创建用户的窗口,只需要填写必填项之后就能新建一个Kerberos用户。注意,在创建Kerberos用户的过程中FreeIPA还会帮我们同时创建一个完全一致(包括用户名和密码)的LDAP用户和Linux用户(所有的注册服务器都会创建),并能保证用户数据事物一致性。
2>.主机管理
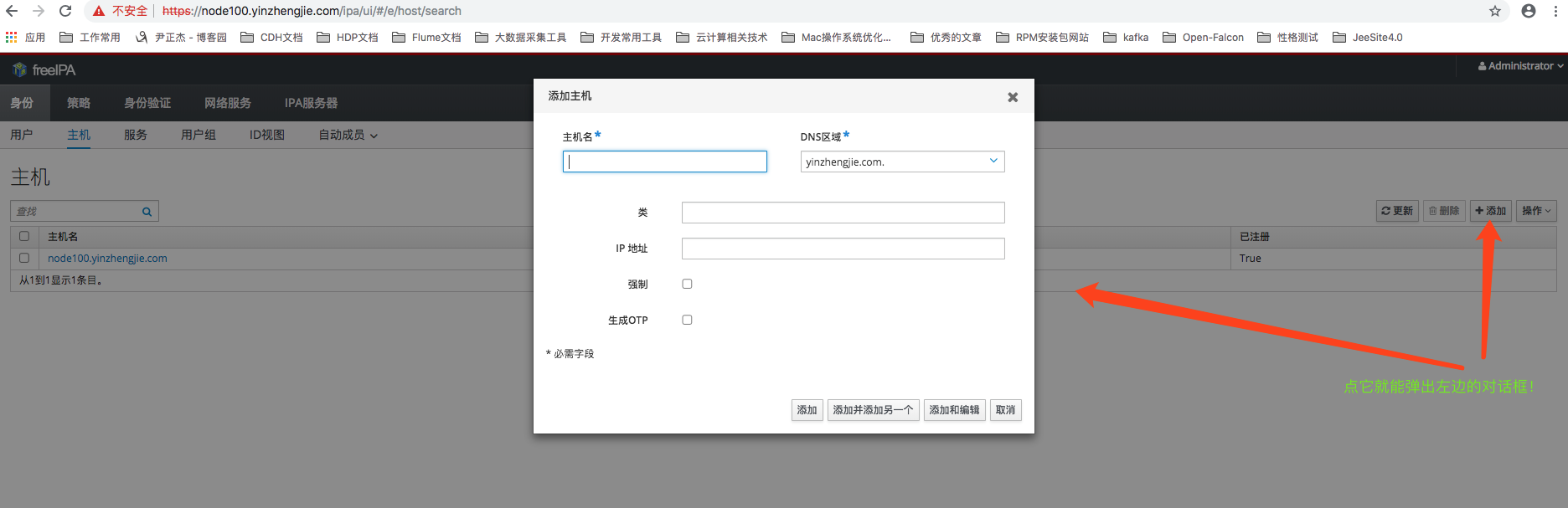
在“身份”分类下单击“主机”菜单能够进入到主机管理页面,通过主机列表可以查看到所有向IPA-Server注册过的服务器。除此之外,这里也提供主机的注册和删除功能。单击Add 按钮打开注册主机的窗口,只需填写必填项之后就能注册一个新的主机,如下图所示。注意,在创建主机的过程中FreeIPA同时也会将这台主机的信息注册到他的DNS服务之中。
3>.服务管理
通过“身份”分类下的“服务”菜单能够进入到服务管理页面,这里能够维护所有通过IPA-Server创建的服务。可以看到经过刚才安装IPA-Server的过程后,FreeIPA已经创建了DNS,HTTP和LDAP等多个服务,如下图所示:
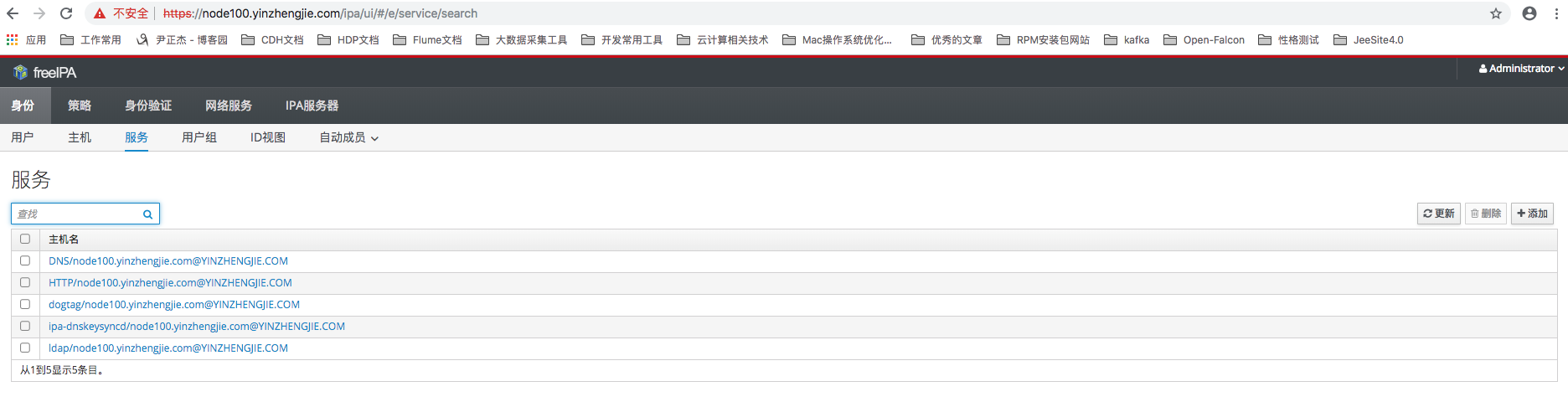
4>.密码策略
通过“策略”分类下的“密码策略”菜单能够进入到密码策略设置页面,这里能够维护全局的密码策略配置,例如密码的最小长度,失效时间和允许的错误密码登陆次数等等,如下图所示:
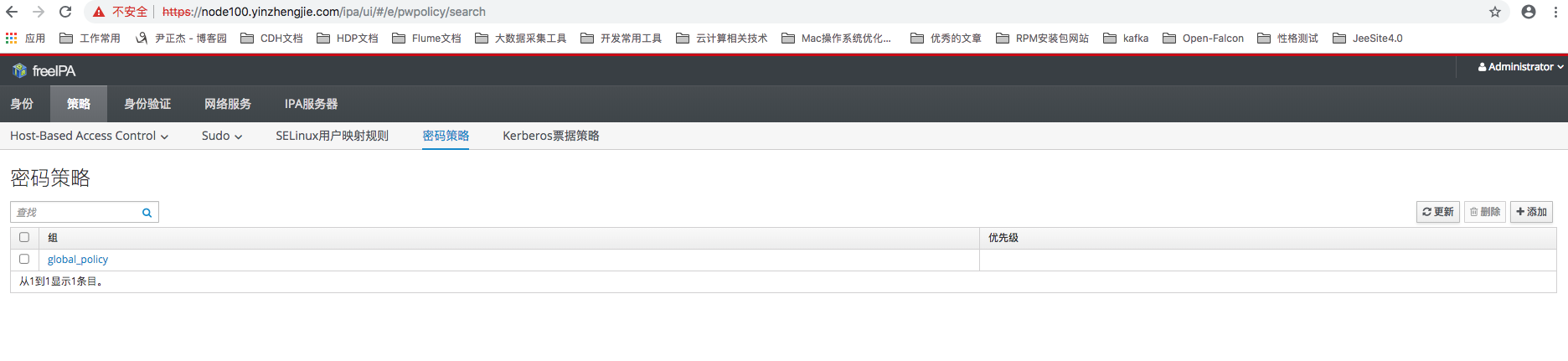
四.IPA CLI 功能介绍
FreeIPA除了Web UI控制台之外,FreeIPA还提供了另外一种利器,那就是它的CLI接口。通过CLI接口我们即可完成对IPA对管理工作。IPA的CLI登录分为远程和本地两种模式,
远程登录通过ipa命令进行,执行此命令需要服务器安装ipa-admintools工具,远程登录的方式适用于拥有IPA管理权限但没有IPA-Server服务器登陆权限的使用场景;
而本地登录则通过“kadmin.local”命令进行,此命令只能在IPA-Server所在的服务器上执行,本地登录的方式适用于直接拥有IPA-Server登录权限的使用场景。接下来我们会分别介绍这两种登录方式以及如何通过CLI创建用户。
1>.使用远程登录(操作节点:node101.yinzhengjie.org.cn)
若要使用远程登录管理IPA-Server的话,那得安装IPA-Admin管理工具
[root@node101 ~]# hostname node101.yinzhengjie.org.cn [root@node101 ~]# [root@node101 ~]# hostname -i 172.30.1.101 [root@node101 ~]# [root@node101 ~]# yum -y install ipa-admintools #安装ipa-admintools管理工具。

[root@node100 ~]# hostname node100.yinzhengjie.com [root@node100 ~]# [root@node100 ~]# hostname -i 172.30.1.100 [root@node100 ~]# [root@node100 ~]# cat /etc/hosts | grep yinzhengjie 172.30.1.100 node100.yinzhengjie.com node100 172.30.1.101 node101.yinzhengjie.org.cn 172.30.1.102 node102.yinzhengjie.org.cn 172.30.1.103 node103.yinzhengjie.org.cn [root@node100 ~]# [root@node100 ~]# scp /etc/krb5.conf node101.yinzhengjie.org.cn:/etc/ The authenticity of host 'node101.yinzhengjie.org.cn (<no hostip for proxy command>)' can't be established. ECDSA key fingerprint is SHA256:SDslkKHyBt925hWfb2K7C+lKWcQ6PTSN3B+G5fetFQ0. ECDSA key fingerprint is MD5:e5:24:dc:52:ee:e6:ed:83:de:45:39:a8:c4:14:27:e7. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'node101.yinzhengjie.org.cn' (ECDSA) to the list of known hosts. root@node101.yinzhengjie.org.cn's password: krb5.conf 100% 1022 1.6MB/s 00:00 [root@node100 ~]#

[root@node101 ~]# cat /etc/krb5.conf # Configuration snippets may be placed in this directory as well includedir /etc/krb5.conf.d/ [logging] default = FILE:/var/log/krb5libs.log kdc = FILE:/var/log/krb5kdc.log admin_server = FILE:/var/log/kadmind.log [libdefaults] dns_lookup_realm = false ticket_lifetime = 24h renew_lifetime = 7d forwardable = true rdns = false default_realm = YINZHENGJIE.COM #default_ccache_name = KEYRING:persistent:%{uid} [realms] YINZHENGJIE.COM = { kdc = node100.yinzhengjie.com:88 admin_server = node100.yinzhengjie.com:749 } [domain_realm] .yinzhengjie.com = YINZHENGJIE.COM yinzhengjie.com = YINZHENGJIE.COM [root@node101 ~]#

[root@node101 ~]# ipa-client-install --domain=YINZHENGJIE.COM --server=node100.yinzhengjie.com --realm=YINZHENGJIE.COM --principal=admin@YINZHENGJIE.COM --enable-dns-updates WARNING: ntpd time&date synchronization service will not be configured as conflicting service (chronyd) is enabled Use --force-ntpd option to disable it and force configuration of ntpd Autodiscovery of servers for failover cannot work with this configuration. If you proceed with the installation, services will be configured to always access the discovered server for all operations and will not fail over to other servers in case of failure. Proceed with fixed values and no DNS discovery? [no]: yes Client hostname: node101.yinzhengjie.org.cn Realm: YINZHENGJIE.COM DNS Domain: yinzhengjie.com IPA Server: node100.yinzhengjie.com BaseDN: dc=yinzhengjie,dc=com Continue to configure the system with these values? [no]: yes Skipping synchronizing time with NTP server. Password for admin@YINZHENGJIE.COM: Successfully retrieved CA cert Subject: CN=Certificate Authority,O=YINZHENGJIE.COM Issuer: CN=Certificate Authority,O=YINZHENGJIE.COM Valid From: 2018-12-12 11:15:53 Valid Until: 2038-12-12 11:15:53 Enrolled in IPA realm YINZHENGJIE.COM Created /etc/ipa/default.conf New SSSD config will be created Configured sudoers in /etc/nsswitch.conf Configured /etc/sssd/sssd.conf Configured /etc/krb5.conf for IPA realm YINZHENGJIE.COM trying https://node100.yinzhengjie.com/ipa/json [try 1]: Forwarding 'schema' to json server 'https://node100.yinzhengjie.com/ipa/json' trying https://node100.yinzhengjie.com/ipa/session/json [try 1]: Forwarding 'ping' to json server 'https://node100.yinzhengjie.com/ipa/session/json' [try 1]: Forwarding 'ca_is_enabled' to json server 'https://node100.yinzhengjie.com/ipa/session/json' Systemwide CA database updated. Hostname (node101.yinzhengjie.org.cn) does not have A/AAAA record. Failed to update DNS records. Missing A/AAAA record(s) for host node101.yinzhengjie.org.cn: 172.30.1.101. Missing reverse record(s) for address(es): 172.30.1.101. Adding SSH public key from /etc/ssh/ssh_host_rsa_key.pub Adding SSH public key from /etc/ssh/ssh_host_ed25519_key.pub Adding SSH public key from /etc/ssh/ssh_host_ecdsa_key.pub [try 1]: Forwarding 'host_mod' to json server 'https://node100.yinzhengjie.com/ipa/session/json' Could not update DNS SSHFP records. SSSD enabled Configured /etc/openldap/ldap.conf Configured /etc/ssh/ssh_config Configured /etc/ssh/sshd_config Configuring yinzhengjie.com as NIS domain. Client configuration complete. The ipa-client-install command was successful [root@node101 ~]#
通过SSH登入安装了ipa-admintools工具的服务器,使用kinit命令登入Kerberos管理员用户(安装IPA-Server时设置的管理员密码)。
[root@node101 ~]# kinit admin Password for admin@YINZHENGJIE.COM: [root@node101 ~]# [root@node101 ~]# klist Ticket cache: KEYRING:persistent:0:0 Default principal: admin@YINZHENGJIE.COM Valid starting Expires Service principal 12/13/2018 16:51:08 12/14/2018 16:51:06 krbtgt/YINZHENGJIE.COM@YINZHENGJIE.COM [root@node101 ~]#

[root@node101 ~]# ipa -h Usage: ipa [global-options] COMMAND [command-options] Manage an IPA domain Options: --version show program's version number and exit -h, --help Show this help message and exit -e KEY=VAL Set environment variable KEY to VAL -c FILE Load configuration from FILE. -d, --debug Produce full debuging output --delegate Delegate the TGT to the IPA server -v, --verbose Produce more verbose output. A second -v displays the XML-RPC request -a, --prompt-all Prompt for ALL values (even if optional) -n, --no-prompt Prompt for NO values (even if required) -f, --no-fallback Only use the server configured in /etc/ipa/default.conf See "ipa help topics" for available help topics. See "ipa help <TOPIC>" for more information on a specific topic. See "ipa help commands" for the full list of commands. See "ipa <COMMAND> --help" for more information on a specific command. [root@node101 ~]#
Kerberos认证成功之后,现在使用ipa user-add创建一个“yinzhengjie-Kerberos”的用户,与命令一起顺带传入用户的first和last名称,如下所示:
[root@node101 ~]# ipa user-add yinzhengjie-kerberos --first=yinzhengjie-kerberos --last=yinzhengjie-kerberos --password #我们这里添加一个yinzhengjie-Kerberos的用户。 Password: #这里需要为“yinzhengjie-Kerberos”用户输入其密码 Enter Password again to verify: --------------------------------- Added user "yinzhengjie-kerberos" --------------------------------- User login: yinzhengjie-kerberos First name: yinzhengjie-kerberos Last name: yinzhengjie-kerberos Full name: yinzhengjie-kerberos yinzhengjie-kerberos Display name: yinzhengjie-kerberos yinzhengjie-kerberos Initials: yy Home directory: /home/yinzhengjie-kerberos GECOS: yinzhengjie-kerberos yinzhengjie-kerberos Login shell: /bin/sh Principal name: yinzhengjie-kerberos@YINZHENGJIE.COM Principal alias: yinzhengjie-kerberos@YINZHENGJIE.COM User password expiration: 20181213102930Z Email address: yinzhengjie-kerberos@yinzhengjie.com UID: 238000001 GID: 238000001 Password: True Member of groups: ipausers Kerberos keys available: True [root@node101 ~]#
用户创建好了之后,再次使用kinit命令登录刚刚建好的用户。可以发现系统会提示密码过期,需要修改密码。这是因为默认的密码策略会要求新建的用户在第一次登录的时候进行修改密码操作,修改密码成功后就完成了登录,通过klist命令可以看到用户以及登录成功啦!具体操作步骤如下:
[root@node101 ~]# klist Ticket cache: KEYRING:persistent:0:0 Default principal: admin@YINZHENGJIE.COM Valid starting Expires Service principal 12/13/2018 18:29:22 12/14/2018 16:51:06 HTTP/node100.yinzhengjie.com@YINZHENGJIE.COM 12/13/2018 18:27:07 12/14/2018 16:51:06 host/node101.yinzhengjie.org.cn@YINZHENGJIE.COM 12/13/2018 16:51:08 12/14/2018 16:51:06 krbtgt/YINZHENGJIE.COM@YINZHENGJIE.COM [root@node101 ~]# [root@node101 ~]# [root@node101 ~]# kinit yinzhengjie-kerberos Password for yinzhengjie-kerberos@YINZHENGJIE.COM: Password expired. You must change it now. Enter new password: Enter it again: [root@node101 ~]# [root@node101 ~]# [root@node101 ~]# klist Ticket cache: KEYRING:persistent:0:krb_ccache_pKnvRro Default principal: yinzhengjie-kerberos@YINZHENGJIE.COM Valid starting Expires Service principal 12/13/2018 18:37:35 12/14/2018 18:37:35 krbtgt/YINZHENGJIE.COM@YINZHENGJIE.COM [root@node101 ~]#
为了验证用户,还可以进入IPA的Web UI控制台,可以发现用户管理页面也能查询到刚刚新建的“yinzhnegjie-kerberos”用户了,如下图所示:
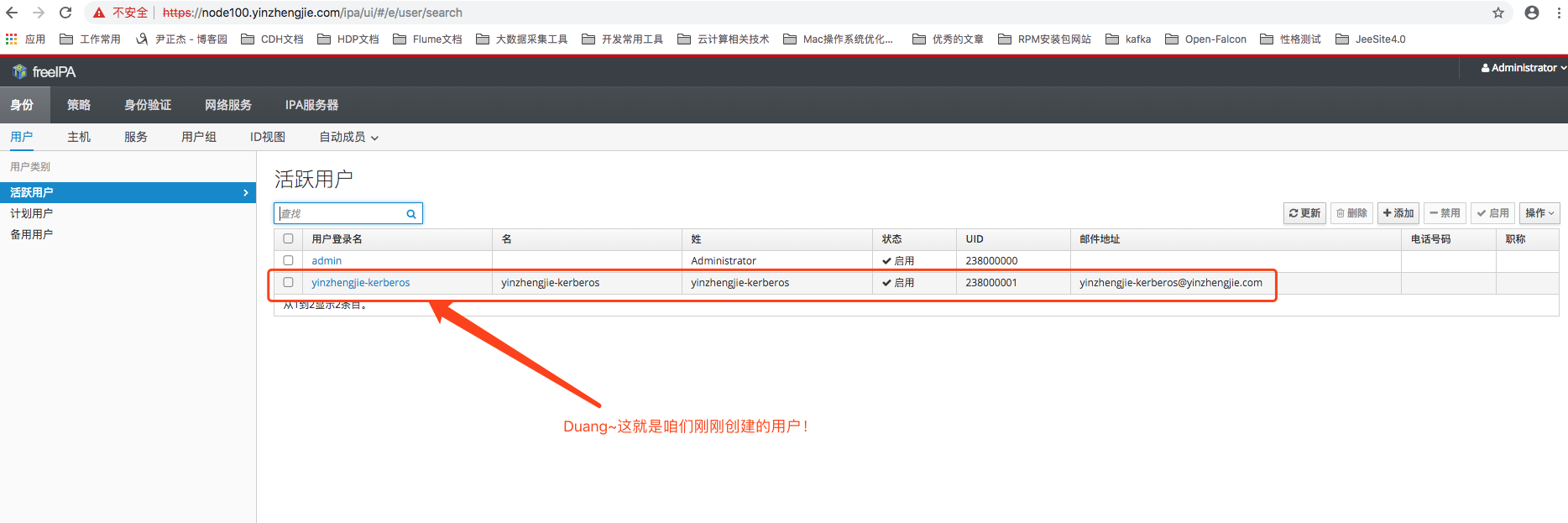
2>.使用本地登录方式(操作节点:node100.yinzhengjie.com。)
使用SSH登录IPA-Server所在的服务器,使用kinit命令登入Kerberos管理员用户。
[root@node100 ~]# hostname #这台机器是用来部署IPA-Server的服务器。 node100.yinzhengjie.com [root@node100 ~]# [root@node100 ~]# hostname -i #IPA-Server对应的IP地址。 172.30.1.100 [root@node100 ~]# [root@node100 ~]# kinit admin #使用Kerberos的管理员admin用户进行登录,需要输入登录密码,这个密码是你在部署IPA-Server时指定的!输入密码成功后,若没有任何输说明你登录成功了,没有输出就是最好的结果。若有输出可能是你登录失败啦! Password for admin@YINZHENGJIE.COM: [root@node100 ~]# [root@node100 ~]# klist #登录成功之后,可以使用klist命令查看当前登录会话信息,信息显示当前登录的admin用户。 Ticket cache: KEYRING:persistent:0:0 Default principal: admin@YINZHENGJIE.COM #注意,这个admin是当前登录的用户,那个“@”是分隔符,而“YINZHENGJIE.COM”是咱们配置IPA-Server时指定的域名 Valid starting Expires Service principal 12/13/2018 01:29:53 12/14/2018 01:29:50 krbtgt/YINZHENGJIE.COM@YINZHENGJIE.COM [root@node100 ~]#
登录成功之后,接着使用kadmin.local命令进入本地管理员模式:
[root@node100 ~]# kadmin.local #进入本地管理员模式 Authenticating as principal admin/admin@YINZHENGJIE.COM with password. kadmin.local: kadmin.local: ? #输入“?”可以查看命令列表。 Available kadmin.local requests: add_principal, addprinc, ank Add principal delete_principal, delprinc Delete principal modify_principal, modprinc Modify principal rename_principal, renprinc Rename principal change_password, cpw Change password get_principal, getprinc Get principal list_principals, listprincs, get_principals, getprincs List principals add_policy, addpol Add policy modify_policy, modpol Modify policy delete_policy, delpol Delete policy get_policy, getpol Get policy list_policies, listpols, get_policies, getpols List policies get_privs, getprivs Get privileges ktadd, xst Add entry(s) to a keytab ktremove, ktrem Remove entry(s) from a keytab lock Lock database exclusively (use with extreme caution!) unlock Release exclusive database lock purgekeys Purge previously retained old keys from a principal get_strings, getstrs Show string attributes on a principal set_string, setstr Set a string attribute on a principal del_string, delstr Delete a string attribute on a principal list_requests, lr, ? List available requests. quit, exit, q Exit program. kadmin.local:
除了使用密码登录之外,Kerberos还允许用keytab密码文件登录。接下来这个案例为咱们之前使用远程登录IPA-Server服务器创建的“yinzhengjie-Kerberos”用户创建它的keytab文件,并使用创建出来的keytab文件进行无密码登录。

kadmin.local: listprincs admin@YINZHENGJIE.COM K/M@YINZHENGJIE.COM krbtgt/YINZHENGJIE.COM@YINZHENGJIE.COM kadmin/node100.yinzhengjie.com@YINZHENGJIE.COM kadmin/admin@YINZHENGJIE.COM kadmin/changepw@YINZHENGJIE.COM kiprop/node100.yinzhengjie.com@YINZHENGJIE.COM ldap/node100.yinzhengjie.com@YINZHENGJIE.COM host/node100.yinzhengjie.com@YINZHENGJIE.COM WELLKNOWN/ANONYMOUS@YINZHENGJIE.COM dogtag/node100.yinzhengjie.com@YINZHENGJIE.COM HTTP/node100.yinzhengjie.com@YINZHENGJIE.COM DNS/node100.yinzhengjie.com@YINZHENGJIE.COM ipa-dnskeysyncd/node100.yinzhengjie.com@YINZHENGJIE.COM host/node101.yinzhengjie.org.cn@YINZHENGJIE.COM yinzhengjie-kerberos@YINZHENGJIE.COM kadmin.local:

[root@node100 ~]# kadmin.local Authenticating as principal admin/admin@YINZHENGJIE.COM with password. kadmin.local: listprincs admin@YINZHENGJIE.COM K/M@YINZHENGJIE.COM krbtgt/YINZHENGJIE.COM@YINZHENGJIE.COM kadmin/node100.yinzhengjie.com@YINZHENGJIE.COM kadmin/admin@YINZHENGJIE.COM kadmin/changepw@YINZHENGJIE.COM kiprop/node100.yinzhengjie.com@YINZHENGJIE.COM ldap/node100.yinzhengjie.com@YINZHENGJIE.COM host/node100.yinzhengjie.com@YINZHENGJIE.COM WELLKNOWN/ANONYMOUS@YINZHENGJIE.COM dogtag/node100.yinzhengjie.com@YINZHENGJIE.COM HTTP/node100.yinzhengjie.com@YINZHENGJIE.COM DNS/node100.yinzhengjie.com@YINZHENGJIE.COM ipa-dnskeysyncd/node100.yinzhengjie.com@YINZHENGJIE.COM host/node101.yinzhengjie.org.cn@YINZHENGJIE.COM yinzhengjie-kerberos@YINZHENGJIE.COM kadmin.local: kadmin.local: xst -k /home/yinzhengjie/yinzhengjie.keytab yinzhengjie-kerberos@YINZHENGJIE.COM Entry for principal yinzhengjie-kerberos@YINZHENGJIE.COM with kvno 5, encryption type aes256-cts-hmac-sha1-96 added to keytab WRFILE:/home/yinzhengjie/yinzhengjie.keytab. Entry for principal yinzhengjie-kerberos@YINZHENGJIE.COM with kvno 5, encryption type aes128-cts-hmac-sha1-96 added to keytab WRFILE:/home/yinzhengjie/yinzhengjie.keytab. Entry for principal yinzhengjie-kerberos@YINZHENGJIE.COM with kvno 5, encryption type des3-cbc-sha1 added to keytab WRFILE:/home/yinzhengjie/yinzhengjie.keytab. Entry for principal yinzhengjie-kerberos@YINZHENGJIE.COM with kvno 5, encryption type arcfour-hmac added to keytab WRFILE:/home/yinzhengjie/yinzhengjie.keytab. Entry for principal yinzhengjie-kerberos@YINZHENGJIE.COM with kvno 5, encryption type camellia128-cts-cmac added to keytab WRFILE:/home/yinzhengjie/yinzhengjie.keytab. Entry for principal yinzhengjie-kerberos@YINZHENGJIE.COM with kvno 5, encryption type camellia256-cts-cmac added to keytab WRFILE:/home/yinzhengjie/yinzhengjie.keytab. kadmin.local: kadmin.local: quit [root@node100 ~]#

[root@node100 ~]# klist Ticket cache: KEYRING:persistent:0:0 Default principal: admin@YINZHENGJIE.COM Valid starting Expires Service principal 12/13/2018 05:50:44 12/14/2018 05:50:43 krbtgt/YINZHENGJIE.COM@YINZHENGJIE.COM [root@node100 ~]# [root@node100 ~]# ll /home/yinzhengjie/yinzhengjie.keytab -rw------- 1 root root 510 Dec 13 05:51 /home/yinzhengjie/yinzhengjie.keytab [root@node100 ~]# [root@node100 ~]# kinit -kt /home/yinzhengjie/yinzhengjie.keytab yinzhengjie-kerberos [root@node100 ~]# [root@node100 ~]# klist Ticket cache: KEYRING:persistent:0:krb_ccache_VY3GwmU Default principal: yinzhengjie-kerberos@YINZHENGJIE.COM Valid starting Expires Service principal 12/13/2018 05:53:33 12/14/2018 05:53:33 krbtgt/YINZHENGJIE.COM@YINZHENGJIE.COM [root@node100 ~]#
怎么样?是不是很神奇?和使用密码一样,使用keytab密码文件也能完成登录动作,并且使用这种方式更加安全。接下来我们介绍一些蟾宫的kadmin.local命令,如果你是做大数据相关运维的工作人员,你应该很熟悉使用这些命令,我这里只是蜻蜓点水式的提一下知识点:
addprinc:
新增一个用户。
modprinc:
修改用户信息。
listprincs:
查询所有的用户。
xst:
生成用户的keytab文件。
cpw:
重置用户密码。
