原文网址:https://blog.csdn.net/zhayujie5200/article/details/80221361
前言
-
之前使用CA服务一直是在
docker容器中运行下载好的CA镜像,在应用程序中通过Node SDK中集成的接口来访问CA服务器,这次尝试手动部署CA服务; -
Fabric CA由服务端和客户端组件组成,CA服务端(
fabric-ca-server)可以看作一个web服务,执行了Go代码编译生成的二进制文件后,会监听一个端口,处理收到的请求; -
CA客户端(
fabric-ca-client)其实就是一个向CA服务端发送请求的程序,执行编译成的二进制文件并带上不同参数,可以向CA服务器发送相应的http请求,完成一系列操作。
准备工作
通过命令行安装和启动CA
-
直接从github下载并编译
go get -u github.com/hyperledger/fabric-ca/cmd/fabric-ca-server go get -u github.com/hyperledger/fabric-ca/cmd/fabric-ca-client -
go get命令会自动获取源码并编译至$GOPATH/bin,我的目录是~/go/bin,目录下出现编译好的二进制可执行文件fabric-ca-server和fabric-ca-client接着初始化和启动
fabric-ca-server,需要设置一个管理员用户的名称和密码fabric-ca-server init -b admin:adminpw fabric-ca-server start -b admin:adminpw -
在这里报错了
panic: Version is not set for fabric-ca library,可能与下载的v1.1版本的fabric-ca有关系。
手动编译生成
-
既然直接从github下载的版本出现错误,可以选择自己去编译生成指定版本的
fabric-ca-server。
首先下载fabric-ca源码并切换至相应版本:git clone https://github.com/hyperledger/fabric-ca.git 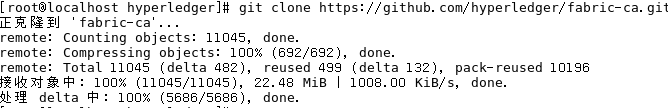
-
然后在
fabric-ca目录下进行编译make fabric-ca-server make fabric-ca-client 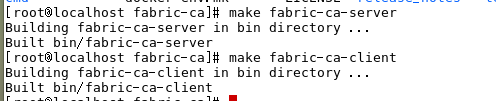
cd /home/admin/gocode/src/github.com/hyperledger/fabric-ca/bin
会在.../fabric-ca/bin目录下生成fabric-ca-server和fabric-ca-client。

接着进入bin目录对CA服务端进行初始化:
fabric-ca-server init -b admin:adminpw

初始化后在目录下生成

msp:包含keystore,CA服务器的私钥ca-cert.pem:CA服务端的证书fabric-ca-server.db:CA默认使用的嵌入型数据库 SQLitefabric-ca-server-config.yaml:CA服务端的配置文件
接着启动CA服务器
fabric-ca-server start -b admin:adminpw

CA server开始监听,默认监听地址为http://0.0.0.0:7054。如果直接执行start命令则会自动先进行初始化init然后启动服务开始监听。
通过docker镜像安装和启动CA
docker镜像中同时包含了fabric-ca-server和fabric-ca-client
-
直接下载fabric-ca镜像
首先可以选择从Docker Hub直接下载fabric-ca镜像:docker pull hyperledger/fabric-ca:x86_64-1.1.0 -
利用
docker-compose.yml文件来启动镜像,配置文件在.../fabric-ca/docker/server中,进入该目录后启动:docker-compose up -
即可启动ca容器,如果镜像不存在还会主动拉取镜像,在
.../server/fabric-ca-server目录中会生成上述的配置文件(这是利用docker-compose.yml文件设置的映射),证书私钥,数据库文件等,并且开始监听一个端口。 -
手动编译docker镜像
除了直接从Docker Hub拉取fabric-ca镜像,还可以通过源码编译生成镜像。
在fabric-ca目录下执行:make docker -
会生成四个镜像
fabric-ca,fabric-ca-tool,fabric-ca-peer,fabric-ca-orderer,镜像保存在.../fabric-ca/build/image中,之后和上面的方法相同根据docker-compose.yml文件启动ca节点。
Fabric CA的使用
访问Fabric CA服务端的方法有两种:通过客户端工具(fabric-ca-client)和RESTful接口。本质上,客户端工具也是调用服务端的RESTful接口实现的。这里采用客户端工具的方法来进行访问。
首先按照上述步骤初始化和启动CA服务器(执行fabric-ca-server或启动CA容器),如果已经下载fabric-ca-client,那移动到相应目录下即可开始操作(若已添加至环境变量则不用)。
如果是以docker容器方式运行CA服务器且未下载客户端工具,可以进入容器内部进行测试(ca镜像集成了服务端和客户端组件),二进制文件放在/usr/local/bin且已经添加环境变量,进入方法为:
docker exec -it fabric-ca-server bash这里选择运行编译好的可执行文件的方法,首先在一个终端下启动CA服务器:
fabric-ca-server start -b admin:adminpw在另一个终端操作CA客户端。首先需要注册(enroll)启动时设置的管理员用户, 注册前需要设置证书存储目录的环境变量:
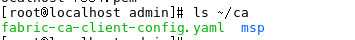
export FABRIC_CA_CLIENT_HOME=$HOME/ca
fabric-ca-client enroll -u http://admin:adminpw@localhost:7054

可以发现~/ca目录下生成了一个fabric-ca-client-config.yaml配置文件,以及msp目录,包含管理员的证书和私钥。
有了已经enroll成功的admin用户,接下来将admin作为登记员(Registrar)来登记(register)一个新用户:
fabric-ca-client register --id.name Jim --id.type user --id.affiliation org1.department1 --id.attrs 'hf.Revoker=true,foo=bar'
[root@localhost admin]# fabric-ca-client register --id.name Jim --id.type user --id.affiliation org1.department1 --id.attrs 'hf.Revoker=true,foo=bar' 2018/06/14 07:24:45 [INFO] Configuration file location: /root/ca/fabric-ca-client-config.yaml Password: iQEoXaLRWmNL
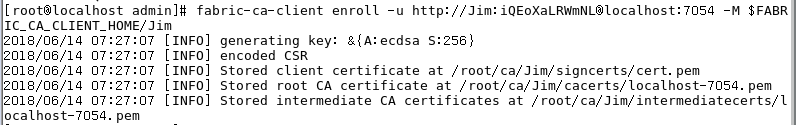
客户端可以接收到一个密码,用这个注册密码来注册(enroll)用户:
fabric-ca-client enroll -u http://Jim:iQEoXaLRWmNL@localhost:7054 -M $FABRIC_CA_CLIENT_HOME/Jim这样一个新用户就注册成功了,获取了属于自己的证书和私钥。
总结
总结一下,手动部署CA服务可以分为两类方法:
-
一种方法是在命令行直接运行编译过后的可执行文件,可以通过
go get命令自动获取并编译(最新版本有报错),也可以手动获取源码,切换版本后再进行编译; 然后在命令行中初始化和启动CA服务器; -
另一种方法是在容器中运行
docker镜像,镜像中包含编译好的可执行文件,镜像可以从Docker Hub直接下载,也可以在fabric-ca目录下利用make docker手动编译,然后利用docker-compose启动CA容器。
最后查看相关文件内容或者树结构
cd /home/admin/gocode/src/github.com/hyperledger/fabric-ca/bin
1 [root@localhost bin]# tree -F 2 . 3 ├── ca-cert.pem 4 ├── fabric-ca-client* 5 ├── fabric-ca-server* 6 ├── fabric-ca-server-config.yaml 7 ├── fabric-ca-server.db 8 └── msp/ 9 └── keystore/ 10 └── 73c8509d3f8b33d60ba9825a0ddeb10dc6a12fb22fc8912c7661e7a639baac0c_sk* 11 12 2 directories, 6 files
gedit fabric-ca-server-config.yaml
# Version of config file version: 1.1.1-snapshot-e656889 # Server's listening port (default: 7054) port: 7054 # Enables debug logging (default: false) debug: false # Size limit of an acceptable CRL in bytes (default: 512000) crlsizelimit: 512000 tls: # Enable TLS (default: false) enabled: false # TLS for the server's listening port certfile: keyfile: clientauth: type: noclientcert certfiles: ca: # Name of this CA name: # Key file (is only used to import a private key into BCCSP) keyfile: # Certificate file (default: ca-cert.pem) certfile: # Chain file chainfile: crl: # Specifies expiration for the generated CRL. The number of hours # specified by this property is added to the UTC time, the resulting time # is used to set the 'Next Update' date of the CRL. expiry: 24h registry: # Maximum number of times a password/secret can be reused for enrollment # (default: -1, which means there is no limit) maxenrollments: -1 # Contains identity information which is used when LDAP is disabled identities: - name: admin pass: adminpw type: client affiliation: "" attrs: hf.Registrar.Roles: "peer,orderer,client,user" hf.Registrar.DelegateRoles: "peer,orderer,client,user" hf.Revoker: true hf.IntermediateCA: true hf.GenCRL: true hf.Registrar.Attributes: "*" hf.AffiliationMgr: true db: type: sqlite3 datasource: fabric-ca-server.db tls: enabled: false certfiles: client: certfile: keyfile: ldap: # Enables or disables the LDAP client (default: false) # If this is set to true, the "registry" section is ignored. enabled: false # The URL of the LDAP server url: ldap://<adminDN>:<adminPassword>@<host>:<port>/<base> # TLS configuration for the client connection to the LDAP server tls: certfiles: client: certfile: keyfile: # Attribute related configuration for mapping from LDAP entries to Fabric CA attributes attribute: # 'names' is an array of strings containing the LDAP attribute names which are # requested from the LDAP server for an LDAP identity's entry names: ['uid','member'] converters: - name: value: maps: groups: - name: value: affiliations: org1: - department1 - department2 org2: - department1 signing: default: usage: - digital signature expiry: 8760h profiles: ca: usage: - cert sign - crl sign expiry: 43800h caconstraint: isca: true maxpathlen: 0 tls: usage: - signing - key encipherment - server auth - client auth - key agreement expiry: 8760h csr: cn: fabric-ca-server names: - C: US ST: "North Carolina" L: O: Hyperledger OU: Fabric hosts: - localhost.localdomain - localhost ca: expiry: 131400h pathlength: 1 bccsp: default: SW sw: hash: SHA2 security: 256 filekeystore: # The directory used for the software file-based keystore keystore: msp/keystore cacount: cafiles: intermediate: parentserver: url: caname: enrollment: hosts: profile: label: tls: certfiles: client: certfile: keyfile:
tree -L 1 fabric-ca
1 ├── api 2 ├── bin 3 ├── CHANGELOG.md 4 ├── ci.properties 5 ├── cmd 6 ├── CODE_OF_CONDUCT.md 7 ├── CONTRIBUTING.md 8 ├── docker 9 ├── docker-env.mk 10 ├── docs 11 ├── images 12 ├── lib 13 ├── LICENSE 14 ├── MAINTAINERS.md 15 ├── Makefile 16 ├── README.md 17 ├── release_notes 18 ├── scripts 19 ├── swagger 20 ├── test 21 ├── testdata 22 ├── util 23 └── vendor
fabric-ca-server-config.yaml
1 # Version of config file
2 version: 1.1.1-snapshot-e656889
3
4 # Server's listening port (default: 7054)
5 port: 7054
6
7 # Enables debug logging (default: false)
8 debug: false
9
10 # Size limit of an acceptable CRL in bytes (default: 512000)
11 crlsizelimit: 512000
12
13 tls:
14 # Enable TLS (default: false)
15 enabled: false
16 # TLS for the server's listening port
17 certfile:
18 keyfile:
19 clientauth:
20 type: noclientcert
21 certfiles:
22
23 ca:
24 # Name of this CA
25 name:
26 # Key file (is only used to import a private key into BCCSP)
27 keyfile:
28 # Certificate file (default: ca-cert.pem)
29 certfile:
30 # Chain file
31 chainfile:
32
33
34 crl:
35 expiry: 24h
36
37
38 registry:
39 # Maximum number of times a password/secret can be reused for enrollment
40 # (default: -1, which means there is no limit)
41 maxenrollments: -1
42
43 # Contains identity information which is used when LDAP is disabled
44 identities:
45 - name: admin
46 pass: adminpw
47 type: client
48 affiliation: ""
49 attrs:
50 hf.Registrar.Roles: "peer,orderer,client,user"
51 hf.Registrar.DelegateRoles: "peer,orderer,client,user"
52 hf.Revoker: true
53 hf.IntermediateCA: true
54 hf.GenCRL: true
55 hf.Registrar.Attributes: "*"
56 hf.AffiliationMgr: true
57
58
59 db:
60 type: sqlite3
61 datasource: fabric-ca-server.db
62 tls:
63 enabled: false
64 certfiles:
65 client:
66 certfile:
67 keyfile:
68
69
70 ldap:
71 # Enables or disables the LDAP client (default: false)
72 # If this is set to true, the "registry" section is ignored.
73 enabled: false
74 # The URL of the LDAP server
75 url: ldap://<adminDN>:<adminPassword>@<host>:<port>/<base>
76 # TLS configuration for the client connection to the LDAP server
77 tls:
78 certfiles:
79 client:
80 certfile:
81 keyfile:
82 # Attribute related configuration for mapping from LDAP entries to Fabric CA attributes
83 attribute:
84 names: ['uid','member']
85 converters:
86 - name:
87 value:
88 maps:
89 groups:
90 - name:
91 value:
92 affiliations:
93 org1:
94 - department1
95 - department2
96 org2:
97 - department1
98 signing:
99 default:
100 usage:
101 - digital signature
102 expiry: 8760h
103 profiles:
104 ca:
105 usage:
106 - cert sign
107 - crl sign
108 expiry: 43800h
109 caconstraint:
110 isca: true
111 maxpathlen: 0
112 tls:
113 usage:
114 - signing
115 - key encipherment
116 - server auth
117 - client auth
118 - key agreement
119 expiry: 8760h
120 csr:
121 cn: fabric-ca-server
122 names:
123 - C: US
124 ST: "North Carolina"
125 L:
126 O: Hyperledger
127 OU: Fabric
128 hosts:
129 - localhost.localdomain
130 - localhost
131 ca:
132 expiry: 131400h
133 pathlength: 1
134 bccsp:
135 default: SW
136 sw:
137 hash: SHA2
138 security: 256
139 filekeystore:
140 # The directory used for the software file-based keystore
141 keystore: msp/keystore
142 cacount:
143 cafiles:
144
145 intermediate:
146 parentserver:
147 url:
148 caname:
149
150 enrollment:
151 hosts:
152 profile:
153 label:
154 tls:
155 certfiles:
156 client:
157 certfile:
158 keyfile: