1、Use Namp performing SYN scanning of the remote system
- in the lab ,there are two systems in you windows.an instance of Metasploitable2 is used to performing TCP SYN scan ,as following :
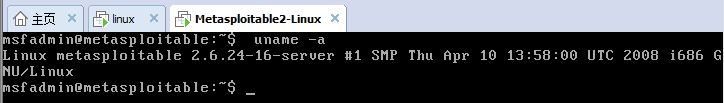
- you can also use the telnet to collect the Metasploitable2 below the windows's console ,and suspend this system .it's fine to kali linux System , to dowlnload the Xshell .

To performing TCP stealth scans with Nmap the -sS option must should include in this option , then we scan the IP address of the host that the host is to be scanned .
eg : nmap -sS 192.168.142.170 -p 80

we can see the screenshot ,Nmap listens for a response and identifies the open ports by analyzing the TCP flags that are activated in any response received .we can use Nmap to performing multiple sepcified ports use the comma-delimited list of port numbers like this : nmap -sS 192.168142.17 -p 21 ,80, 443
besides, we can scanning a list ports like this : nmap -sS 192.168.142.170 -p 21-98 , but if we did not specify the ports ,default scanning the ports is from 1 to 1000 . in fact a full scan is always best practice when attempting to identify all of the possible attack surface on a target . addinational we can scanning multiple addresses simultaneously .like this : nmap 192.168.142.0-255 -sS -p 80 .and use the iplist.txt download the ip addresses .use the option -iL appoint targets .. generally speaking Nmap is a fast and highly effextive way to perform the stealth scanning .
2、Stealth scanning with Metasploit
Metasploit has an auxiliary module that can be used to perform SYN scans on specified TCP ports ,use the command "msfconsole" to start the Metasploit like this:

we use the auxiliary : syn

and then to configure : set the ports 、 host 、 and therads
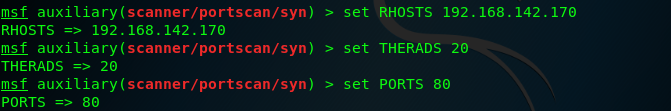
to run the auxiliary,,,also set the port list


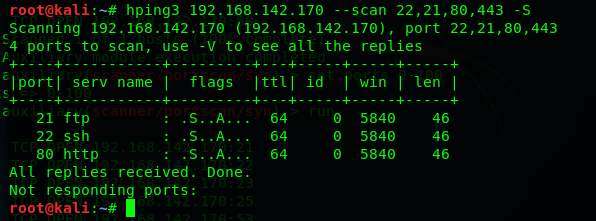
3、Stealth scanning with hping3
hping3 can also be used to perform a TCP stealth scan , we use the command : hping3 192.168.142.170 --scan 80 -S
4、use the Lazy script to penetration to test wesite
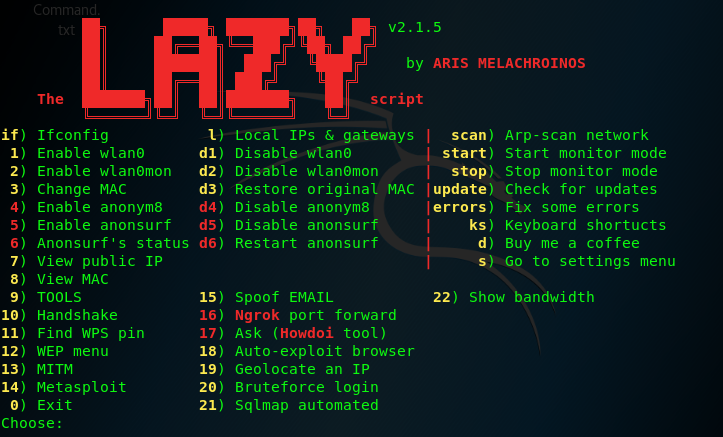
configure the option and performing

and then use the fsociety to guess the auxiliary
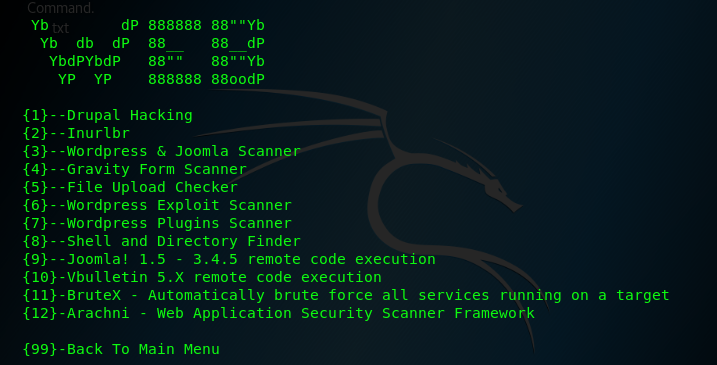
and then input the target ip address

after Violence test ,we can get the A weak password for obtaining services on the target host.
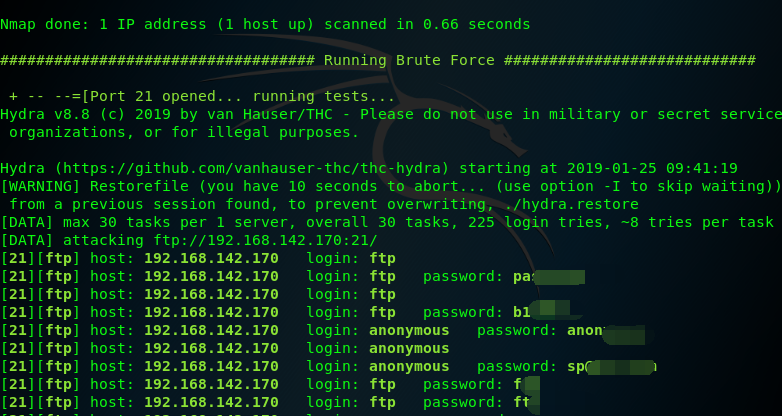
..