OAuth 2.0 All In One
OAuth 2.0 原理剖析
https://tools.ietf.org/html/rfc6749
OAuth 2.1
OAuth 2.0 Playground
https://www.oauth.com/playground/

OpenID Connect / OIDC
https://www.oauth.com/playground/oidc.html
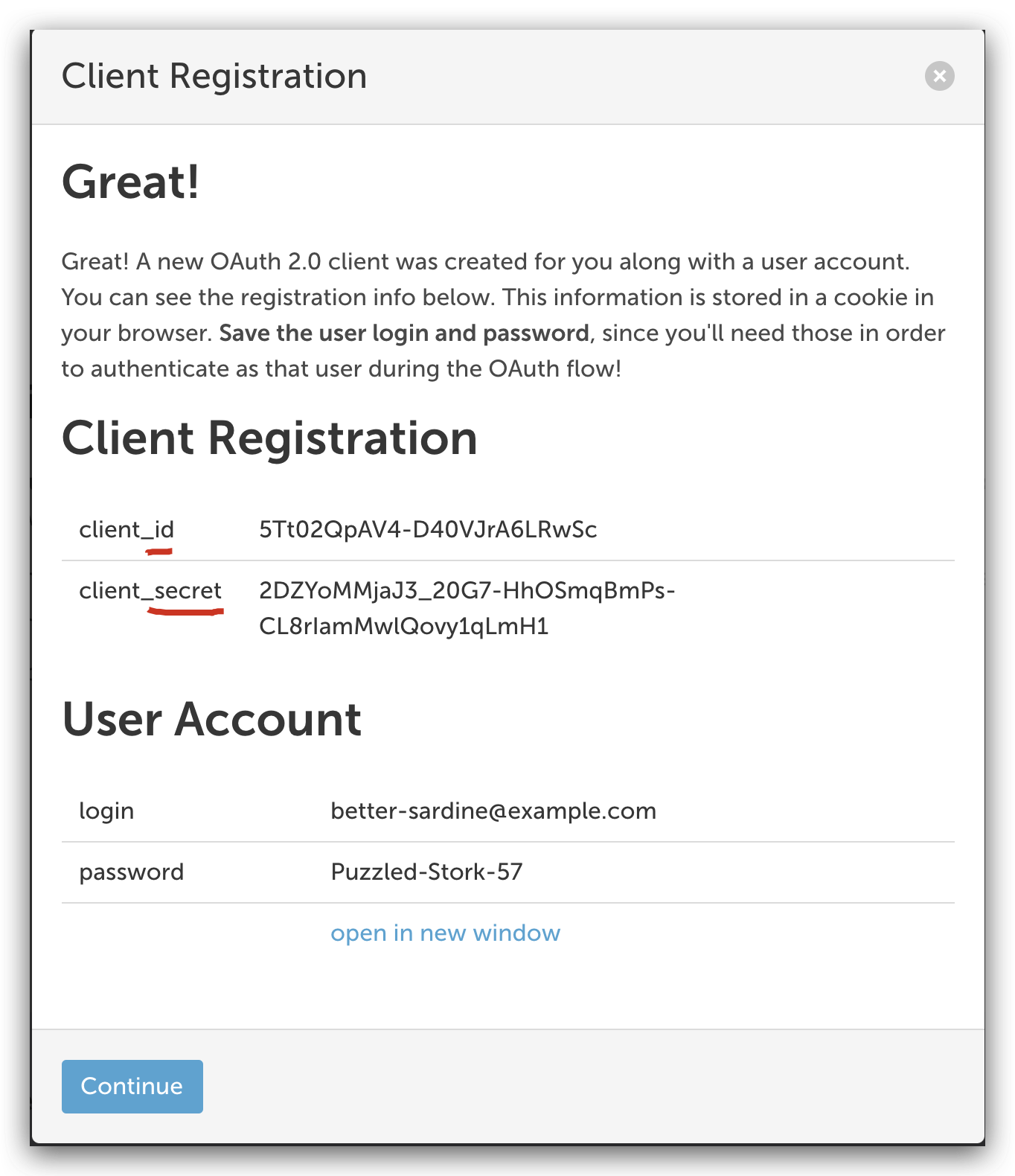
# Client Registration
client_id 5Tt02QpAV4-D40VJrA6LRwSc
client_secret 2DZYoMMjaJ3_20G7-HhOSmqBmPs-CL8rIamMwlQovy1qLmH1
# User Account
login better-sardine@example.com
password Puzzled-Stork-57
https://www.oauth.com/playground/client-registration.html?returnto=oidc.html#
Step 1, Build the authorization URL and redirect the user to the authorization server
Step 2, After the user is redirected back to the client, verify the state matches
Step 3, Exchange the authorization code for an ID token and access token

?state=7hNgmIWkGPBIn2Ad&code=4YN7iqdzBjDewsH9D0dgZ4xjW7JxMJ7Ywy2V04qW6ksTNCIr
POST https://authorization-server.com/token
grant_type=authorization_code
&client_id=5Tt02QpAV4-D40VJrA6LRwSc
&client_secret=2DZYoMMjaJ3_20G7-HhOSmqBmPs-CL8rIamMwlQovy1qLmH1
&redirect_uri=https://www.oauth.com/playground/oidc.html
&code=4YN7iqdzBjDewsH9D0dgZ4xjW7JxMJ7Ywy2V04qW6ksTNCIr
{
"token_type": "Bearer",
"expires_in": 86400,
"access_token": "2A1vb3_SsQfuIbC7ZTzKzIzpVQ1uRbFx5kuzTfyIw-4T3a85rLmQviNH_tpJ5Qei_rbVPyyU",
"scope": "openid profile email photo",
"id_token": "eyJraWQiOiJzMTZ0cVNtODhwREo4VGZCXzdrSEtQUkFQRjg1d1VEVGxteW85SUxUZTdzIiwiYWxnIjoiUlMyNTYifQ.eyJzdWIiOiJiZXR0ZXItc2FyZGluZUBleGFtcGxlLmNvbSIsIm5hbWUiOiJCZXR0ZXIgU2FyZGluZSIsImVtYWlsIjoiYmV0dGVyLXNhcmRpbmVAZXhhbXBsZS5jb20iLCJpc3MiOiJodHRwczovL3BrLWRlbW8ub2t0YS5jb20vb2F1dGgyL2RlZmF1bHQiLCJhdWQiOiI1VHQwMlFwQVY0LUQ0MFZKckE2TFJ3U2MiLCJpYXQiOjE1OTk4MTMzNDcsImV4cCI6MTYwMjQwNTM0NywiYW1yIjpbInB3ZCJdfQ.ZoPvZPaomdOnnz2GFRGbgaW7PPWIMFDqSBp0gbN4An4a9F-Bc-4_T9EBGV8aGetyjZYAON0gjNV0p0NGFiwettePWKuxBzusuGCEd9iXWWUO9-WTF5e2AGr3_jkg34dbxfiFXy3KgH7m0czm809cMaiZ_ofLYgJHVD8lqMQoWifhoNhpjPqa19Svc3nCHzSYHUgTXQWvA56NmQvyVPh_OM7GMpc6zHopmihJqt3eREof8N-bOd7FL39jeam2-k1TFSDogyJE513aC0OssRADr_TWvtL8xoaPkXM_7bXYs9_7erXmzF9la0hvmOuasieetpLhOvFeoiOJWCU9xhxj4Q"
}
access_token & refresh_token
OAuth 2.0 的 4 种认证流程
Authorization Code
Implicit
Resource Owner Password Credentials
Client Credentials
Authorization Code
最常见的也是最安全的第一种 Authorization Code
JWT
refs
https://www.chrisyue.com/security-issue-about-oauth-2-0-you-should-know.html
https://dev.fitbit.com/build/reference/web-api/oauth2/
https://developers.google.com/identity/protocols/oauth2
https://developers.google.com/youtube/v3/guides/auth/server-side-web-apps
https://swagger.io/docs/specification/authentication/oauth2/
©xgqfrms 2012-2020
www.cnblogs.com 发布文章使用:只允许注册用户才可以访问!