php服务端与客户端交互、提供开放api时,通常需要对敏感的部分api数据传输进行数据加密,这时候rsa非对称加密就能派上用处了,下面通过一个例子来说明如何用php来实现数据的加密解密
加密解密的第一步是生成公钥、私钥对,私钥加密的内容能通过公钥解密(反过来亦可以)
通过私钥能生成对应的公钥,因此我们将私钥用在服务器端,公钥发放给android、ios等前端。
以下是加密类文件(Rsa.class.php)代码:
<?php /** * RSA算法类 * 签名及密文编码:base64字符串/十六进制字符串/二进制字符串流 * 填充方式: PKCS1Padding(加解密)/NOPadding(解密) * * Notice:Only accepts a single block. Block size is equal to the RSA key size! * 如密钥长度为1024 bit,则加密时数据需小于128字节,加上PKCS1Padding本身的11字节信息,所以明文需小于117字节 */ class RSA { private $pubKey = null; private $priKey = null; /** * 构造函数 */ public function __construct() { // 需要开启openssl扩展 if (!extension_loaded("openssl")) { $this->_error("Please open the openssl extension first."); } } /** * 读取公钥和私钥 * @param string $public_key_file 公钥文件(验签和加密时传入) * @param string $private_key_file 私钥文件(签名和解密时传入) */ public function init($public_key_file = '', $private_key_file = '') { if ($public_key_file) { $this->_getPublicKey($public_key_file); } if ($private_key_file) { $this->_getPrivateKey($private_key_file); } } /** * 自定义错误处理 */ private function _error($msg) { die('RSA Error:' . $msg); //TODO } /** * 检测填充类型 * 加密只支持PKCS1_PADDING * 解密支持PKCS1_PADDING和NO_PADDING * * @param int 填充模式 * @param string 加密en/解密de * @return bool */ private function _checkPadding($padding, $type) { if ($type == 'en') { switch ($padding) { case OPENSSL_PKCS1_PADDING: $ret = true; break; default: $ret = false; } } else { switch ($padding) { case OPENSSL_PKCS1_PADDING: case OPENSSL_NO_PADDING: $ret = true; break; default: $ret = false; } } return $ret; } private function _encode($data, $code) { switch (strtolower($code)) { case 'base64': $data = base64_encode('' . $data); break; case 'hex': $data = bin2hex($data); break; case 'bin': default: } return $data; } private function _decode($data, $code) { switch (strtolower($code)) { case 'base64': $data = base64_decode($data); break; case 'hex': $data = $this->_hex2bin($data); break; case 'bin': default: } return $data; } private function _getPublicKey($file) { $key_content = $this->_readFile($file); if ($key_content) { $this->pubKey = openssl_get_publickey($key_content); } } private function _getPrivateKey($file) { $key_content = $this->_readFile($file); if ($key_content) { $this->priKey = openssl_get_privatekey($key_content); } } private function _readFile($file) { $ret = false; if (!file_exists($file)) { $this->_error("The file {$file} is not exists"); } else { $ret = file_get_contents($file); } return $ret; } private function _hex2bin($hex = false) { $ret = $hex !== false && preg_match('/^[0-9a-fA-F]+$/i', $hex) ? pack("H*", $hex) : false; return $ret; } /** * 生成Rsa公钥和私钥 * @param int $private_key_bits 建议:[512, 1024, 2048, 4096] * @return array */ public function generate($private_key_bits = 2048) { $rsa = [ "private_key" => "", "public_key" => "" ]; $config = [ "digest_alg" => "sha512", "private_key_bits" => $private_key_bits, #此处必须为int类型 "private_key_type" => OPENSSL_KEYTYPE_RSA, "config" => "D:phpStudyPHPTutorialApacheconfopenssl.cnf" //如果没有配置这项,openssl_pkey_new会返回false ]; //创建公钥和私钥 $res = openssl_pkey_new($config); //提取私钥 由于上一步传入了$config参数,所以这一步也需要传入这个参数, openssl_pkey_export($res, $rsa['private_key'],null,$config);// //生成公钥 $rsa['public_key'] = openssl_pkey_get_details($res)["key"]; // print_r($rsa);die; return $rsa; } /** * 生成签名 * * @param string 签名材料 * @param string 签名编码(base64/hex/bin) * @return bool|string 签名值 */ public function sign($data, $code = 'base64') { $ret = false; if (openssl_sign($data, $ret, $this->priKey)) { $ret = $this->_encode($ret, $code); } return $ret; } /** * 验证签名 * * @param string 签名材料 * @param string 签名值 * @param string 签名编码(base64/hex/bin) * @return bool */ public function verify($data, $sign, $code = 'base64') { $ret = false; $sign = $this->_decode($sign, $code); if ($sign !== false) { switch (openssl_verify($data, $sign, $this->pubKey)) { case 1: $ret = true; break; case 0: case -1: default: $ret = false; } } return $ret; } /** * 加密 * * @param string 明文 * @param string 密文编码(base64/hex/bin) * @param int 填充方式(貌似php有bug,所以目前仅支持OPENSSL_PKCS1_PADDING) * @return string 密文 */ public function encrypt($data, $code = 'base64', $padding = OPENSSL_PKCS1_PADDING) { $ret = false; if (!$this->_checkPadding($padding, 'en')) $this->_error('padding error'); if (openssl_public_encrypt($data, $result, $this->pubKey, $padding)) { $ret = $this->_encode($result, $code); } return $ret; } /** * 解密 * * @param string 密文 * @param string 密文编码(base64/hex/bin) * @param int 填充方式(OPENSSL_PKCS1_PADDING / OPENSSL_NO_PADDING) * @param bool 是否翻转明文(When passing Microsoft CryptoAPI-generated RSA cyphertext, revert the bytes in the block) * @return string 明文 */ public function decrypt($data, $code = 'base64', $padding = OPENSSL_PKCS1_PADDING, $rev = false) { $ret = false; $data = $this->_decode($data, $code); if (!$this->_checkPadding($padding, 'de')) $this->_error('padding error'); if ($data !== false) { if (openssl_private_decrypt($data, $result, $this->priKey, $padding)) { $ret = $rev ? rtrim(strrev($result), "�") : '' . $result; } } return $ret; } }
下面是测试文件(user.php)代码:
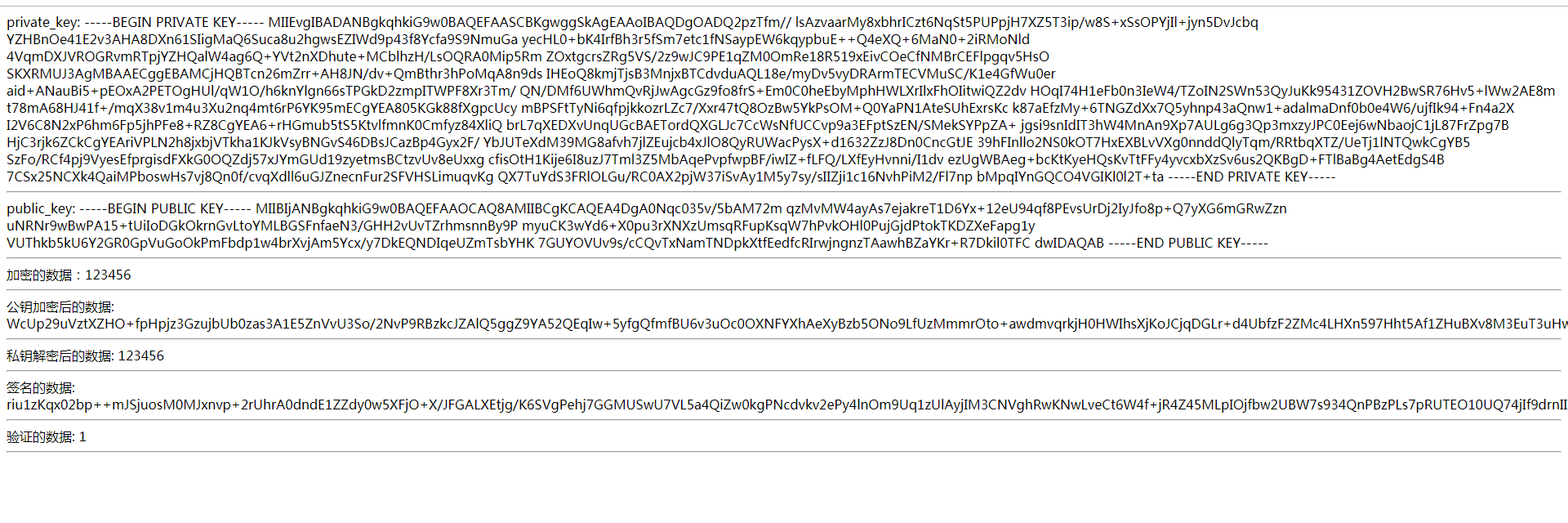
<?php if (!class_exists("RSA")) { require_once "Rsa.class.php"; } $private_key_file = __DIR__ . "/private_key.pem"; $public_key_file = __DIR__ . "/public_key.pem"; $rsa = new RSA(); // 没有就生成一对 if (!file_exists($private_key_file) || !file_exists($public_key_file)) { $key = $rsa->generate(); file_put_contents($private_key_file, $key['private_key'], LOCK_EX); file_put_contents($public_key_file, $key['public_key'], LOCK_EX); } else { $key = [ "private_key" => file_get_contents($private_key_file), "public_key" => file_get_contents($public_key_file) ]; } //显示数据 echo "private_key: " . $key['private_key'] . "<hr/>"; echo "public_key: " . $key['public_key'] . "<hr/>"; //要加密的数据 $data = "123456"; echo '加密的数据:' . $data, "<hr/>"; $rsa->init($public_key_file, $private_key_file); //加密 $encrypt = $rsa->encrypt($data); echo "公钥加密后的数据: " . $encrypt . "<hr/>"; //解密 $decrypt = $rsa->decrypt($encrypt); echo "私钥解密后的数据: " . $decrypt, "<hr/>"; //签名 $sign = $rsa->sign($data); echo "签名的数据(私钥加密): " . $sign . "<hr/>"; //验证 $verify = $rsa->verify($data, $sign); echo "验证的数据: " . $verify . "<hr/>";
运行结果如下图: