第2章 fping应用
主机扫描命令 fping
作用:
批量的给目标主机发送ping请求,测试主机的存活情况
特点:
并行发送、结果易读。
fping安装步骤
一、获取源码包(http://fping.org)
常用参数介绍
-a 只显示出存活的主机(相反参数-u)
1、通过标准输入方式 fping+IP1+IP2
-g 支持主机段的方式 192.168.1.1 192.168.1.255 192.168.1.0/24
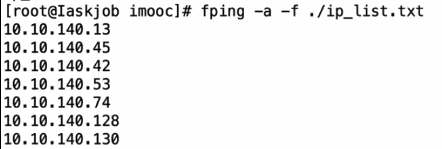
2、通过读取一个文件中P内容
方式:fping -f filename
[root@centos-6 ~]# fping 8.8.8.8 223.5.5.5
223.5.5.5 is alive
8.8.8.8 is alive
[root@centos-6 ~]# fping -a 8.8.8.8 223.5.5.5
223.5.5.5
8.8.8.8[root@centos-6 ~]# fping -a -g 10.0.1.1 10.0.1.66
10.0.1.1
10.0.1.60
ICMP Host Unreachable from 10.0.1.60 for ICMP Echo sent to 10.0.1.2
ICMP Host Unreachable from 10.0.1.60 for ICMP Echo sent to 10.0.1.3
ICMP Host Unreachable from 10.0.1.60 for ICMP Echo sent to 10.0.1.3
ICMP Host Unreachable from 10.0.1.60 for ICMP Echo sent to 10.0.1.4
ICMP Host Unreachable from 10.0.1.60 for ICMP Echo sent to 10.0.1.4
ICMP Host Unreachable from 10.0.1.60 for ICMP Echo sent to 10.0.1.5
ICMP Host Unreachable from 10.0.1.60 for ICMP Echo sent to 10.0.1.5其他主机icmp无法到达
[root@cs7-play ~]# fping -h
Usage: fping [options] [targets...]
-a show targets that are alive
-A show targets by address
-b n amount of ping data to send, in bytes (default 56)
-B f set exponential backoff factor to f
-c n count of pings to send to each target (default 1)
-C n same as -c, report results in verbose format
-D print timestamp before each output line
-e show elapsed time on return packets
-f file read list of targets from a file ( - means stdin) (only if no -g specified)
-g generate target list (only if no -f specified)
(specify the start and end IP in the target list, or supply a IP netmask)
(ex. fping -g 192.168.1.0 192.168.1.255 or fping -g 192.168.1.0/24)
-H n Set the IP TTL value (Time To Live hops)
-i n interval between sending ping packets (in millisec) (default 25)
-I if bind to a particular interface
-l loop sending pings forever
-m ping multiple interfaces on target host
-n show targets by name (-d is equivalent)
-O n set the type of service (tos) flag on the ICMP packets
-p n interval between ping packets to one target (in millisec)
(in looping and counting modes, default 1000)
-q quiet (don't show per-target/per-ping results)
-Q n same as -q, but show summary every n seconds
-r n number of retries (default 3)
-s print final stats
-S addr set source address
-t n individual target initial timeout (in millisec) (default 500)
-T n ignored (for compatibility with fping 2.4)
-u show targets that are unreachable
-v show version
targets list of targets to check (if no -f specified)第3章 hping应用
特点:支持使用的TCP/IP数据包组装、分析工具
官方站点:http://www.hping.org
安装之前的准备:
yum -y install gcc libpcap-devel tcl-devel
libpcap-devel安装不上的话去官网下载安装包手动安装
./configure && make && make install
建立软链接:ln -sf /usr/include/pcap-bpf.h /usr/include/net/bpf.h
yum install -y epel-release
yum install hping3 -y
Hping常用参数
一、对制定目标端口发起tcp探测
-p 端口
-S 设置TCP模式SYN包
二、伪造来源IP,模拟Ddos攻击。
-a 伪造IP地址
忽略icmp包
[root@centos-7 ~]# sysctl -w net.ipv4.icmp_echo_ignore_all=1
net.ipv4.icmp_echo_ignore_all = 1
[root@centos-6 ~]# hping -p 22 -S 10.0.1.10
HPING 10.0.1.10 (eth1 10.0.1.10): S set, 40 headers + 0 data bytes
len=46 ip=10.0.1.10 ttl=64 DF id=0 sport=22 flags=SA seq=0 win=29200 rtt=0.6 ms
len=46 ip=10.0.1.10 ttl=64 DF id=0 sport=22 flags=SA seq=1 win=29200 rtt=0.4 ms
len=46 ip=10.0.1.10 ttl=64 DF id=0 sport=22 flags=SA seq=2 win=29200 rtt=0.6 ms
len=46 ip=10.0.1.10 ttl=64 DF id=0 sport=22 flags=SA seq=3 win=29200 rtt=0.4 ms
len=46 ip=10.0.1.10 ttl=64 DF id=0 sport=22 flags=SA seq=4 win=29200 rtt=0.3 ms
len=46 ip=10.0.1.10 ttl=64 DF id=0 sport=22 flags=SA seq=5 win=29200 rtt=0.3 ms
^C
--- 10.0.1.10 hping statistic ---
6 packets transmitted, 6 packets received, 0% packet loss
round-trip min/avg/max = 0.3/0.4/0.6 ms
[root@centos-6 ~]# ping 10.0.1.10
PING 10.0.1.10 (10.0.1.10) 56(84) bytes of data.
^C
--- 10.0.1.10 ping statistics ---
15 packets transmitted, 0 received, 100% packet loss, time 14172ms
[root@centos-6 ~]# fping -u 10.0.1.10
10.0.1.10
[root@centos-6 ~]# hping -p 22 -S 10.0.1.10
HPING 10.0.1.10 (eth1 10.0.1.10): S set, 40 headers + 0 data bytes
len=46 ip=10.0.1.10 ttl=64 DF id=0 sport=22 flags=SA seq=0 win=29200 rtt=0.6 ms
len=46 ip=10.0.1.10 ttl=64 DF id=0 sport=22 flags=SA seq=1 win=29200 rtt=0.3 ms
len=46 ip=10.0.1.10 ttl=64 DF id=0 sport=22 flags=SA seq=2 win=29200 rtt=0.3 ms
len=46 ip=10.0.1.10 ttl=64 DF id=0 sport=22 flags=SA seq=3 win=29200 rtt=0.5 ms
len=46 ip=10.0.1.10 ttl=64 DF id=0 sport=22 flags=SA seq=4 win=29200 rtt=0.5 ms
len=46 ip=10.0.1.10 ttl=64 DF id=0 sport=22 flags=SA seq=5 win=29200 rtt=0.4 ms
^C
--- 10.0.1.10 hping statistic ---
6 packets transmitted, 6 packets received, 0% packet loss
round-trip min/avg/max = 0.3/0.4/0.6 ms伪造发送包
[root@centos-6 ~]# hping -p 22 -S 10.0.1.10 -a 10.0.1.66
HPING 10.0.1.10 (eth1 10.0.1.10): S set, 40 headers + 0 data bytes[root@centos-7 ~]# tcpdump -np -ieth1 src host 10.0.1.66
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
06:48:39.862942 IP 10.0.1.66.femis > 10.0.1.10.ssh: Flags [S], seq 1667558992, win 512, length 0
06:48:40.863042 IP 10.0.1.66.powerguardian > 10.0.1.10.ssh: Flags [S], seq 701797966, win 512, length 0
06:48:41.863324 IP 10.0.1.66.prodigy-intrnet > 10.0.1.10.ssh: Flags [S], seq 723565960, win 512, length 0
06:48:42.863251 IP 10.0.1.66.pharmasoft > 10.0.1.10.ssh: Flags [S], seq 1068083137, win 512, length 0
06:48:43.863535 IP 10.0.1.66.dpkeyserv > 10.0.1.10.ssh: Flags [S], seq 1386484520, win 512, length 0
06:48:44.863755 IP 10.0.1.66.answersoft-lm > 10.0.1.10.ssh: Flags [S], seq 1894541823, win 512, length 0
06:48:45.864261 IP 10.0.1.66.hp-hcip > 10.0.1.10.ssh: Flags [S], seq 1854398663, win 512, length 0
06:48:46.864519 IP 10.0.1.66.1783 > 10.0.1.10.ssh: Flags [S], seq 754640729, win 512, length 0
06:48:47.864785 IP 10.0.1.66.finle-lm > 10.0.1.10.ssh: Flags [S], seq 432832534, win 512, length 0
06:48:48.864992 IP 10.0.1.66.windlm > 10.0.1.10.ssh: Flags [S], seq 1672102746, win 512, length 0
06:48:49.865081 IP 10.0.1.66.funk-logger > 10.0.1.10.ssh: Flags [S], seq 182615851, win 512, length 0
06:48:50.865966 IP 10.0.1.66.funk-license > 10.0.1.10.ssh: Flags [S], seq 1113500186, win 512, length 0