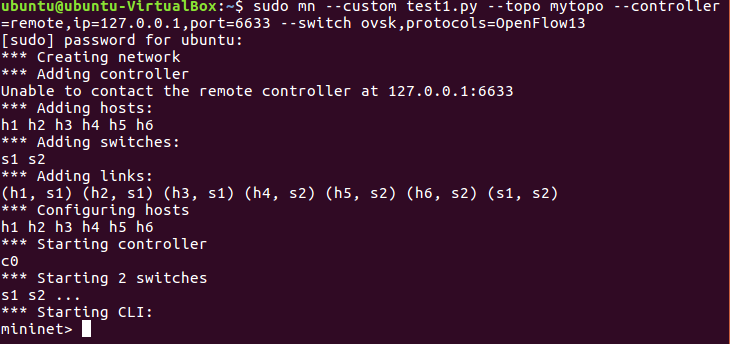
1.实验拓扑
- 实验拓扑

- 使用Python脚本完成拓扑搭建,并连接ryu控制器
代码如下
from mininet.topo import Topo
class Mytopo(Topo):
def __init__(self):
Topo.__init__(self)
s=[]
for i in range(2):
sw = self.addSwitch('s{}'.format(i+1))
s.append(sw)
self.addLink(s[0],s[1])
count=1
for two in s:
for i in range(3):
host = self.addHost('h{}'.format(count))
self.addLink(two,host)
count += 1
topos = {'mytopo': (lambda:Mytopo())}
拓扑搭建成功
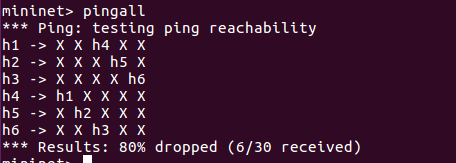
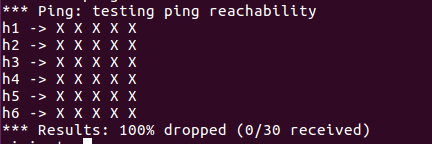
使用pingall命令测试连通性
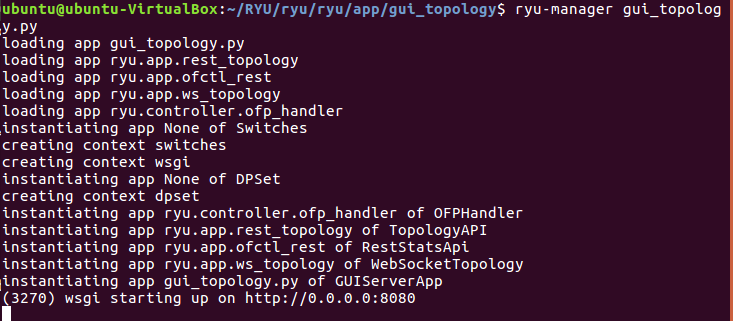
输入命令连接ryu控制器
ryu-manager ofctl_rest.py
输入net,查看各主机与交换机之间的端口情况,方便确定之后脚本中匹配项的值
2.使用Ryu的REST API下发流表实现和第2次实验同样的VLAN
s1脚本
#端口号1发来数据
curl -X POST -d '{
"dpid": 1,
"priority":1,
"match":{
"in_port":1
},
"actions":[
{
"type": "PUSH_VLAN", # s1将从主机发来的数据包打上vlan_tag
"ethertype": 33024 # 帧类型0x8100(=33024): 表示IEEE 802.1Q的VLAN数据帧
},
{
"type": "SET_FIELD",
"field": "vlan_vid", # 设置VLAN ID
"value": 4096 # 设置vlan_id的值
},
{
"type": "OUTPUT",
"port": 4
}
]
}' http://127.0.0.1:8080/stats/flowentry/add
#端口号2发来数据
curl -X POST -d '{
"dpid": 1,
"priority":1,
"match":{
"in_port":2
},
"actions":[
{
"type": "PUSH_VLAN", # s1将从主机发来的数据包打上vlan_tag
"ethertype": 33024 # 帧类型0x8100(=33024): 表示IEEE 802.1Q的VLAN数据帧
},
{
"type": "SET_FIELD",
"field": "vlan_vid", # 设置VLAN ID
"value": 4097 # 设置vlan_id的值
},
{
"type": "OUTPUT",
"port": 4
}
]
}' http://127.0.0.1:8080/stats/flowentry/add
#端口号3发来数据
curl -X POST -d '{
"dpid": 1,
"priority":1,
"match":{
"in_port":3
},
"actions":[
{
"type": "PUSH_VLAN", # s1将从主机发来的数据包打上vlan_tag
"ethertype": 33024 # 帧类型0x8100(=33024): 表示IEEE 802.1Q的VLAN数据帧
},
{
"type": "SET_FIELD",
"field": "vlan_vid", # 设置VLAN ID
"value": 4098 # 设置vlan_id的值
},
{
"type": "OUTPUT",
"port": 4
}
]
}' http://127.0.0.1:8080/stats/flowentry/add
#向端口1转发
curl -X POST -d '{
"dpid": 1,
"priority":1,
"match":{
"dl_vlan": "0"
},
"actions":[
{
"type": "POP_VLAN", # 给进入交换机的包去除 vlan_tag
},
{
"type": "OUTPUT",
"port": 1
}
]
}' http://localhost:8080/stats/flowentry/add
#向端口2转发
curl -X POST -d '{
"dpid": 1,
"priority":1,
"match":{
"dl_vlan": "1"
},
"actions":[
{
"type": "POP_VLAN", # 给进入交换机的包去除 vlan_tag
},
{
"type": "OUTPUT",
"port": 2
}
]
}' http://localhost:8080/stats/flowentry/add
#向端口3转发
curl -X POST -d '{
"dpid": 1,
"priority":1,
"match":{
"dl_vlan": "2"
},
"actions":[
{
"type": "POP_VLAN", # 给进入交换机的包去除 vlan_tag
},
{
"type": "OUTPUT",
"port": 3
}
]
}' http://localhost:8080/stats/flowentry/add
s2脚本
#端口号1发来数据
curl -X POST -d '{
"dpid": 2,
"priority":1,
"match":{
"in_port":1
},
"actions":[
{
"type": "PUSH_VLAN", # s1将从主机发来的数据包打上vlan_tag
"ethertype": 33024 # 帧类型0x8100(=33024): 表示IEEE 802.1Q的VLAN数据帧
},
{
"type": "SET_FIELD",
"field": "vlan_vid", # 设置VLAN ID
"value": 4096 # 设置vlan_id的值
},
{
"type": "OUTPUT",
"port": 4
}
]
}' http://127.0.0.1:8080/stats/flowentry/add
#端口号2发来数据
curl -X POST -d '{
"dpid": 2,
"priority":1,
"match":{
"in_port":2
},
"actions":[
{
"type": "PUSH_VLAN", # s1将从主机发来的数据包打上vlan_tag
"ethertype": 33024 # 帧类型0x8100(=33024): 表示IEEE 802.1Q的VLAN数据帧
},
{
"type": "SET_FIELD",
"field": "vlan_vid", # 设置VLAN ID
"value": 4097 # 设置vlan_id的值
},
{
"type": "OUTPUT",
"port": 4
}
]
}' http://127.0.0.1:8080/stats/flowentry/add
#端口号3发来数据
curl -X POST -d '{
"dpid": 2,
"priority":1,
"match":{
"in_port":3
},
"actions":[
{
"type": "PUSH_VLAN", # s1将从主机发来的数据包打上vlan_tag
"ethertype": 33024 # 帧类型0x8100(=33024): 表示IEEE 802.1Q的VLAN数据帧
},
{
"type": "SET_FIELD",
"field": "vlan_vid", # 设置VLAN ID
"value": 4098 # 设置vlan_id的值
},
{
"type": "OUTPUT",
"port": 4
}
]
}' http://127.0.0.1:8080/stats/flowentry/add
#向端口1转发
curl -X POST -d '{
"dpid": 2,
"priority":1,
"match":{
"dl_vlan": "0"
},
"actions":[
{
"type": "POP_VLAN", # 给进入交换机的包去除 vlan_tag
},
{
"type": "OUTPUT",
"port": 1
}
]
}' http://localhost:8080/stats/flowentry/add
#向端口2转发
curl -X POST -d '{
"dpid": 2,
"priority":1,
"match":{
"dl_vlan": "1"
},
"actions":[
{
"type": "POP_VLAN", # 给进入交换机的包去除 vlan_tag
},
{
"type": "OUTPUT",
"port": 2
}
]
}' http://localhost:8080/stats/flowentry/add
#向端口3转发
curl -X POST -d '{
"dpid": 2,
"priority":1,
"match":{
"dl_vlan": "2"
},
"actions":[
{
"type": "POP_VLAN", # 给进入交换机的包去除 vlan_tag
},
{
"type": "OUTPUT",
"port": 3
}
]
}' http://localhost:8080/stats/flowentry/add
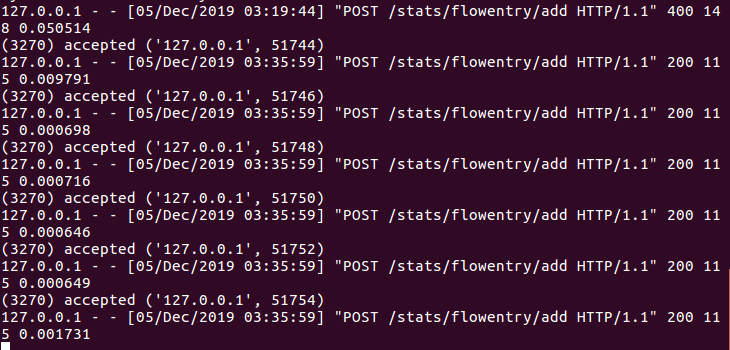
s1下发流表结果
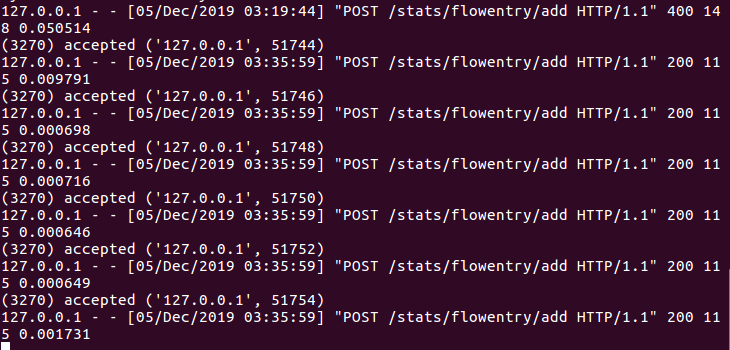
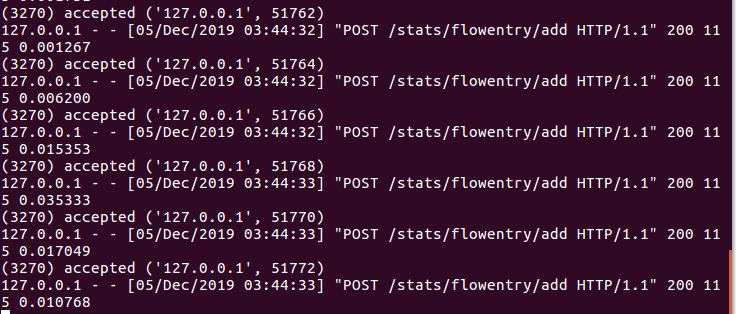
s2下发流表结果
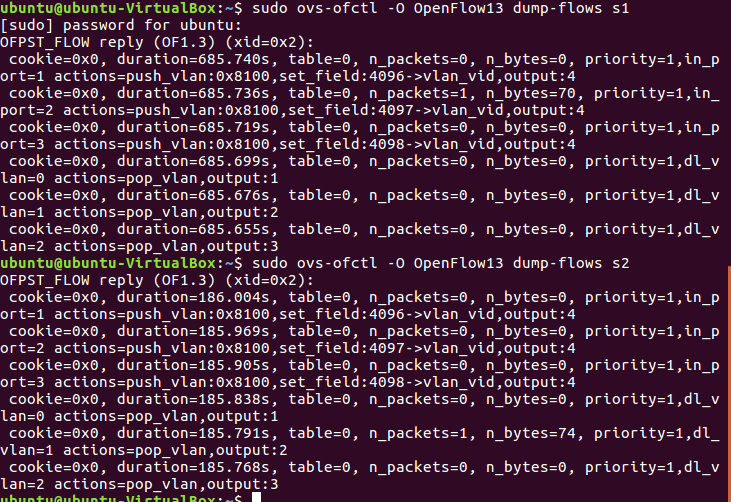
完成所有下发流表后,使用命令查看s1, s2流表
sudo ovs-ofctl -O OpenFlow13 dump-flows s1
sudo ovs-ofctl -O OpenFlow13 dump-flows s2
ping通查看连接性