如何利用Wireshark解密SSL和TLS流量
https://support.citrix.com/article/CTX135121
1.有server端的private key,直接在wireshark上使用
Edit > Preferences->Protocols->RSA keys list
这个protocol必须是小写http,用了大写的会报错。。。
key file必须-----BEGIN RSA PRIVATE KEY-----,如果是-----BEGIN ENCRYPTED PRIVATE KEY-----要转换下,password不填,填了会报错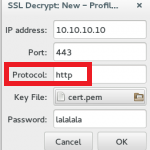
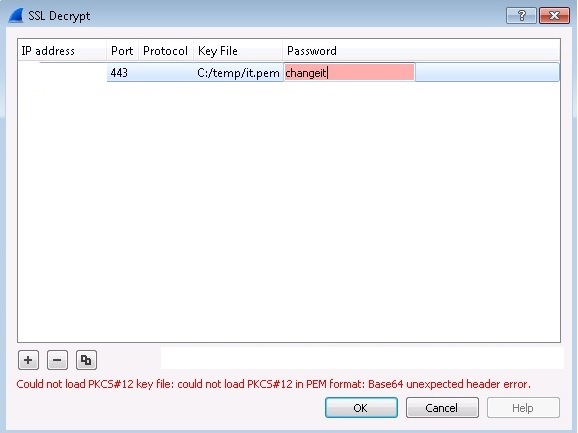
pfx => pem
Private key
openssl pkcs12 -in yourP12File.pfx -nocerts -out privateKey.pem
-----BEGIN ENCRYPTED PRIVATE KEY-----
...
-----END ENCRYPTED PRIVATE KEY-----
Certificates:
openssl pkcs12 -in yourP12File.pfx -clcerts -nokeys -out publicCert.pem
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
Convert from -----BEGIN ENCRYPTED PRIVATE KEY----- to -----BEGIN RSA PRIVATE KEY-----
rsa -in d: empprivateKey.pem -out d: empprivateKey.pem
PEM => DER
openssl x509 -in cert.crt -outform der -out cert.der
DER => PEM
openssl x509 -in cert.crt -inform der -outform pem -out cert.pem
2.没有server端的private key,利用fiddler跳转,wireshark上使用fiddler中转的private key
利用Fiddler和Wireshark解密SSL加密流量
http://www.cnblogs.com/AloneSword/p/4567380.html
http://kelvinh.github.io/blog/2014/01/12/decrypt-ssl-using-fiddler-and-wireshark/
SoapUI with Fiddler
http://stackoverflow.com/questions/3744602/soapui-with-fiddler
因为wireshark不支持对loopback监听,所以在一台机器上安装fiddler和wireshark,另一台机器作为客户端安装soapui
Fiddler: Tools->Options->Connections : Allow Remote computers to connect
Tools->Options->HTTPS->Export Root Certificate to Desktop
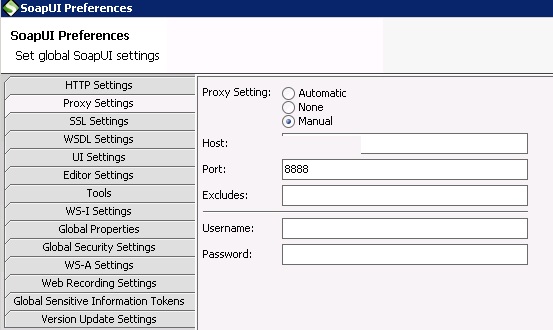
SoapUI: File->Preferences->Proxy Settings IPaddress:8888
cd C:Program Files (x86)SmartBearSoapUI-4.6.2jre
keytool -importcert -file c: empFiddlerRoot.cer -keystore "C:Program Files (x86)SmartBearSoapUI-4.6.2jrelibsecuritycacerts" -alias testkey
After SoapUI server call https requests with Fiddler , we can find the certification in the IE
Tools->Internet Options->Content->Certificates->Export IPaddress certificatin : export the private key
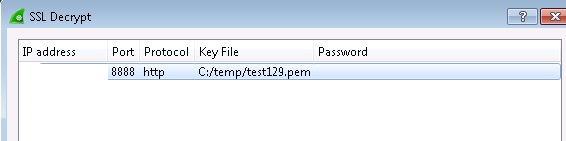
Wireshark: Edit > Preferences->Protocols->RSA keys list
IPaddress 8888 http c:/temp/Ipaddress.pem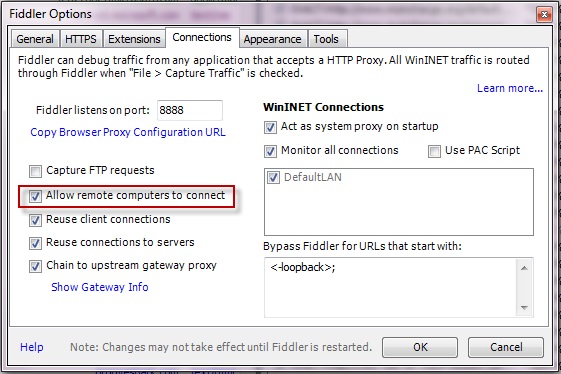
wireshark filter:
ssl.record.version == 0x0301
SSL 3.0 3,0 0x0300 TLS 1.0 3,1 0x0301 TLS 1.1 3,2 0x0302 TLS 1.2 3,3 0x0303
(tcp.port == 1234) or (tcp.port == 5678)