一、下载包【地址:https://github.com/kubernetes/kubernetes/releases】(master主机,尽量下载正式版)
①、本地上传压缩包至linux服务器
#windows系统本地上传到linux
scp -r D:迅雷下载kubernetes-server-linux-amd64.tar.gz root@172.17.217.232:/usr/local/bin
#wget下载二进制包【需要科学·上网】
wget https://dl.k8s.io/v1.15.2/kubernetes-server-linux-amd64.tar.gz
#解压
tar -xvf kubernetes-server-linux-amd64.tar.gz
#创建kubernetes相关文件夹
mkdir /opt/kubernetes
#创建二进制、配置文件、ssl文件夹
mkdir /opt/kubernetes/ bin cfg ssl
#将二进制文件复制至/opt/kubernetes/bin
cp kubernetes/server/bin/{kube-controller-manager,kube-apiserver,kubectl,kube-scheduler} /opt/kubernetes/bin/
②、创建api证书配置文件
#创建ca颁发机构配置 vi /opt/kubernetes/ssl/ca-config.json { "signing": { "default": { "expiry": "175200h" #过期时间20年 }, "profiles": { "server": { "expiry": "175200h", "usages": [ "signing", "key encipherment", "server auth" ] }, "client": { "expiry": "175200h", "usages": [ "signing", "key encipherment", "client auth" ] }, "kubernetes": { "expiry": "175200h", "usages": [ "signing", "key encipherment", "server auth", "client auth" ] } } } }
#创建ca颁发机构配置 vi /opt/kubernetes/ssl/ca-config.json #配置信息 { "signing": { "default": { "expiry": "175200h" #过期时间20年 }, "profiles": { "server": { "expiry": "175200h", "usages": [ "signing", "key encipherment", "server auth" ] }, "client": { "expiry": "175200h", "usages": [ "signing", "key encipherment", "client auth" ] }, "kubernetes": { "expiry": "175200h", "usages": [ "signing", "key encipherment", "server auth", "client auth" ] } } } }
#ca颁发机构证书配置 vi /opt/kubernetes/ssl/ca-csr.json #写入配置 { "CN": "kubernetes CA", "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "guangdong", "ST": "shenzhen" } ] }
#hosts中将所有可能作为apiserver的ip添加进去, 也要加入 vi /opt/kubernetes/ssl/server-csr.json #写入配置
{ "CN": "kubernetes", "hosts": [ "172.17.217.232", "127.0.0.1", "172.17.217.226", "172.17.217.228", "kubernetes", "kubernetes.default", "kubernetes.default.svc", "kubernetes.default.svc.cluster", "kubernetes.default.svc.cluster.local" ], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "guangdong", "ST": "shenzhen" } ] }
#创建kube-proxy-csr.josn文件
vi /opt/kubernetes/ssl/kube-proxy-csr.json
#写入配置
{
"CN": "kube-proxy", "hosts": [], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "guangdong", "ST": "shenzhen", "O": "k8s", "OU": "System" } ] }
颁发证书:
#颁发ca证书 cfssl gencert -initca ca-csr.json | cfssljson -bare ca -
#签发kube-proxy证书
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes kube-proxy-csr.json | cfssljson -bare kube-proxy
#签发apiserver证书 cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes server-csr.json | cfssljson -bare server
③、创建配置(kube-apiserver.conf)
vi /opt/kubernetes/cfg/kube-apiserver.conf KUBE_APISERVER_OPTS="--logtostderr=true #是否开启标转错误日志 --v=4 #日志级别 --log-dir=/opt/kubernetes/logs #日志存放地址 --etcd-servers=https://172.17.217.232:2379,https://172.17.217.226:2379,https://172.17.217.228:2379 #etcd节点地址 --bind-address=172.17.217.232 #当前master绑定地址 --secure-port=6443 #当前监听端口 --advertise-address=172.17.217.228 #通告其他节点地址 --allow-privileged=true #是否使用管理员创建容器 --service-cluster-ip-range=10.0.0.0/24 #service服务网段 --enable-admission-plugins=NamespaceLifecycle,LimitRanger,SecurityContextDeny,ServiceAccount,ResourceQuota,NodeRestriction #使用插件 --authorization-mode=RBAC,Node #授权模式、角色、节点 --enable-bootstrap-token-auth=true #基于bootstrap自签颁发证书 --token-auth-file=/opt/kubernetes/cfg/token.csv #自签证书配置 --service-node-port-range=30000-50000 #端口范围 --tls-cert-file=/opt/kubernetes/ssl/server.pem #访问apiserver 证书 --tls-private-key-file=/opt/kubernetes/ssl/server-key.pem --client-ca-file=/opt/kubernetes/ssl/ca.pem --service-account-key-file=/opt/kubernetes/ssl/ca-key.pem --etcd-cafile=/opt/etcd/ssl/ca.pem #访问etcd证书 --etcd-certfile=/opt/etcd/ssl/server.pem --etcd-keyfile=/opt/etcd/ssl/server-key.pem
--audit-log-maxage=30 #日志相关配置
--audit-log-maxbackup=3
--audit-log-maxsize=100
--audit-log-path=/opt/kubernetes/logs/k8s.log"
④、创建配置(kube-controller-manager.conf)
#创建配置文件
vi /opt/kubernetes/cfg/kube-controller-manager.conf
#写入配置 KUBE_CONTROLLER_MANAGER_OPTS="--logtostderr=true #标准错误日志 --v=4 #日志等级 --log-dir=/opt/kubernetes/logs --master=127.0.0.1:8080 #api-server 地址 --leader-elect=true #多个 --address=127.0.0.1 #监听地址 --allocate-node-cidrs=true #是否支持网络插件 --cluster-cidr=10.224.0.0/16 #基于网络插件网段 --service-cluster-ip-range=10.0.0.0/24 #客户端地址范围 --cluster-name=kubernetes --cluster-signing-cert-file=/opt/kubernetes/ssl/ca.pem --cluster-signing-key-file=/opt/kubernetes/ssl/ca-key.pem --root-ca-file=/opt/kubernetes/ssl/ca.pem --service-account-private-key-file=/opt/kubernetes/ssl/ca-key.pem"
⑤、创建配置(kube-scheduler.conf)
#创建配置
vi /opt/kubernetes/cfg/kube-scheduler.conf
#写入配置
KUBE_SCHEDULER_OPTS="--logtostderr=true --v=4 --log-dir=/opt/kubernetes/logs --master=127.0.0.1:8080 #master 地址 --leader-elect #自动选举 --address=127.0.0.1"#当前监听地址
⑥、创建启动服务(kube-apiserver.service)
#创建启动服务文件
vi /usr/lib/systemd/system/kube-apiserver.service
#写入配置
[Unit] Description=Kubernetes API Server Documentation=https://github.com/kubernetes/kubernetes [Service] EnvironmentFile=-/opt/kubernetes/cfg/kube-apiserver.conf #指定配置文件 ExecStart=/opt/kubernetes/bin/kube-apiserver $KUBE_APISERVER_OPTS Restart=on-failure [Install] WantedBy=multi-user.target
⑦、创建启动服务(kube-controller-manager.service)
#创建启动服务文件
vi /usr/lib/systemd/system/kube-controller-manager.service
#写入配置
[Unit] Description=Kubernetes Controller Manager Documentation=https://github.com/kubernetes/kubernetes [Service] EnvironmentFile=-/opt/kubernetes/cfg/kube-controller-manager.conf ExecStart=/opt/kubernetes/bin/kube-controller-manager $KUBE_CONTROLLER_MANAGER_OPTS Restart=on-failure
⑧、创建启动配置(kube-scheduler.service)
[Unit] Description=Kubernetes Scheduler Documentation=https://github.com/kubernetes/kubernetes [Service] EnvironmentFile=-/opt/kubernetes/cfg/kube-scheduler.conf ExecStart=/opt/kubernetes/bin/kube-scheduler $KUBE_SCHEDULER_OPTS Restart=on-failure [Install] WantedBy=multi-user.target
⑨、创建token.csv【自签证书】
#创建token.csv文件
touch /opt/kubernetes/cfg/token.csv
#token【随机生成】 #用户名 #用户Id #用户所在命名空间
b2h326jj2sns6bryahz4i1m6cklesj9o,kubelet-bootstrap,10001,"system:kubelet-bootstrap"
⑩、启动服务查看服务
#启动、开机自启动apiserver
systemctl start kube-apiserver systemctl enable kube-apiserver
#启动、开机自启动controller-manager
systemctl start kube-controller-manager
systemctl enable kube-controller-manager
#启动开机自启scheduler systemctl start kube-scheduler systemctl enable kube-scheduler
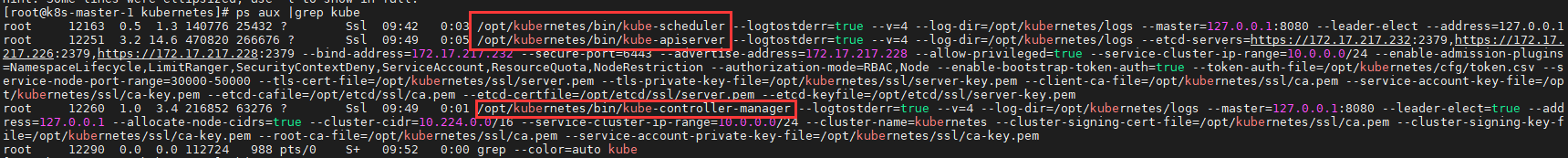
#查看运行服务 ps aux |grep kube
#查看服务运行状态 /opt/kubernetes/bin/kubectl get cs
#将kubectl复制到/bin/下【直接执行 kubectl get cs】
cp /opt/kubernetes/bin/kubectl /bin/
查看运行状态

二、错误查看、排查
①、查看错误日志
cat /var/log/messages|grep kube-apiserver|grep -i error
②、服务启动失败排查错误,执行失败会打印出错误信息【例如api-server】
#执行kube-apiserver 加上配置
/opt/kubernetes/bin/kube-apiserver --logtostderr=true --v=4 --log-dir=/opt/kubernetes/logs
--etcd-servers=https://192.168.2.200:2379,https://192.168.2.110:2379
--bind-address=192.168.2.200
--secure-port=6443
--advertise-address=192.168.2.200
--allow-privileged=true
--service-cluster-ip-range=10.0.0.0/24
--enable-admission-plugins=NamespaceLifecycle,LimitRanger,SecurityContextDeny,ServiceAccount,ResourceQuota,NodeRestriction
--authorization-mode=RBAC,Node
--enable-bootstrap-token-auth=true
--token-auth-file=/opt/kubernetes/cfg/token.csv
--service-node-port-range=30000-50000
--tls-cert-file=/opt/kubernetes/ssl/server.pem
--tls-private-key-file=/opt/kubernetes/ssl/server-key.pem
--client-ca-file=/opt/kubernetes/ssl/ca.pem
--service-account-key-file=/opt/kubernetes/ssl/ca-key.pem
--etcd-cafile=/opt/etcd/ssl/ca.pem
--etcd-certfile=/opt/etcd/ssl/server.pem
--etcd-keyfile=/opt/etcd/ssl/server-key.pem
--audit-log-maxage=30 --audit-log-maxbackup=3
--audit-log-maxsize=100 --audit-log-path=/opt/kubernetes/logs/k8s.log