1.http2协议
- HTTP 2.0 的主要目标是改进传输性能,实现低延迟和高吞吐量。从另一方面看,HTTP 的高层协议语义并不会因为这次版本升级而受影响。所有HTTP 首部、值,以及它们的使用场景都不会变。
- 现有的任何网站和应用,无需做任何修改都可以在HTTP 2.0 上跑起来。不用为了利用HTTP 2.0 的好处而修改标记。HTTP 服务器必须运行HTTP 2.0 协议,但大部分用户都不会因此而受到影响
- centos6安装参考:
- https://imhanjm.com/2017/04/20/nginx%20http2%E7%BC%96%E8%AF%91%E5%AE%89%E8%A3%85/
- http://blog.csdn.net/littlesmallless/article/details/59173287
2.编译安装nginx
#1.安装依赖
[root@hadoop_node1 ~]# yum install -y gcc gcc-c++ pcre pcre-devel openssl-devel zlib zlib-devel
#2.下载安装
[root@hadoop_node1 ~]# cd /usr/local/src/
[root@hadoop_node1 src]# wget http://nginx.org/download/nginx-1.10.3.tar.gz
[root@hadoop_node1 src]# tar xf nginx-1.10.3.tar.gz
[root@hadoop_node1 src]# cd nginx-1.10.3/
#3.编译参数
[root@hadoop_node1 nginx-1.10.3]# ./configure --user=nginx --group=nginx --prefix=/usr/local/nginx-1.10.3 --with-http_stub_status_module --with-http_ssl_module --with-http_v2_module
[root@hadoop_node1 nginx-1.10.3]# make && make install
- --with-http_v2_module 支持http2协议
[root@hadoop_master nginx]# /usr/local/nginx/sbin/nginx -V
nginx version: nginx/1.10.3
built by gcc 4.8.5 20150623 (Red Hat 4.8.5-16) (GCC)
built with OpenSSL 1.0.2k-fips 26 Jan 2017
TLS SNI support enabled
configure arguments: --user=nginx --group=nginx --prefix=/usr/local/nginx-1.10.3 --with-http_stub_status_module --with-http_ssl_module --with-http_v2_module
3.生成证书
[root@hadoop_node1 nginx-1.10.3]# ln -s /usr/local/nginx-1.10.3/ /usr/local/nginx
[root@hadoop_node1 nginx-1.10.3]# cd /usr/local/nginx/conf/
[root@hadoop_node1 conf]# mkdir key
[root@hadoop_node1 conf]# cd key/
#自定义密码
[root@hadoop_node1 key]# openssl genrsa -des3 -out server.key 1024
Generating RSA private key, 1024 bit long modulus
..........++++++
..........++++++
e is 65537 (0x10001)
Enter pass phrase for server.key:
Verifying - Enter pass phrase for server.key:
#签发证书
[root@hadoop_node1 key]# openssl req -new -key server.key -out server.csr
Enter pass phrase for server.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:BJ
Locality Name (eg, city) [Default City]:BJ
Organization Name (eg, company) [Default Company Ltd]:SDU
Organizational Unit Name (eg, section) []:SA
Common Name (eg, your name or your server's hostname) []:xiaojin
Email Address []:123@qq.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:123456
[root@hadoop_node1 key]# cp server.key server.key.ori
[root@hadoop_node1 key]# openssl rsa -in server.key.ori -out server.key
Enter pass phrase for server.key.ori:
writing RSA key
[root@hadoop_node1 key]# openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
Signature ok
subject=/C=CN/ST=BJ/L=BJ/O=SDU/OU=SA/CN=xiaojin/emailAddress=123@qq.com
Getting Private key
4.修改nginx的配置文件
[root@hadoop_node1 conf]# cat nginx.conf
worker_processes 1;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout 65;
server {
listen 80;
server_name 10.0.0.71;
if ($scheme ~ http) {
return https://$server_name:8443$request_uri;
}
location / {
root html;
index index.html index.htm;
}
location = /50x.html {
root html;
}
}
server {
listen 8443 ssl http2 default_server;
server_name 10.0.0.71;
ssl_certificate key/server.crt;
ssl_certificate_key key/server.key;
location / {
root html;
index index.html index.htm;
}
location = /50x.html {
root html;
}
}
}
[root@hadoop_node1 conf]# iptables -I INPUT -p tcp --dport 80 -j ACCEPT
[root@hadoop_node1 conf]# iptables -I INPUT -p tcp --dport 8443 -j ACCEPT
[root@hadoop_node1 conf]# /usr/local/nginx/sbin/nginx -t
nginx: the configuration file /usr/local/nginx-1.10.3/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx-1.10.3/conf/nginx.conf test is successful
[root@hadoop_node1 conf]# /usr/local/nginx/sbin/nginx
[root@hadoop_node1 conf]# ss -lntup|grep 8
tcp LISTEN 0 128 *:80 *:* users:(("nginx",pid=7582,fd=6),("nginx",pid=7581,fd=6))
tcp LISTEN 0 128 *:22 *:* users:(("sshd",pid=1885,fd=3))
tcp LISTEN 0 128 *:8443 *:* users:(("nginx",pid=7582,fd=7),("nginx",pid=7581,fd=7))
tcp LISTEN 0 128 :::22 :::* users:(("sshd",pid=1885,fd=4))
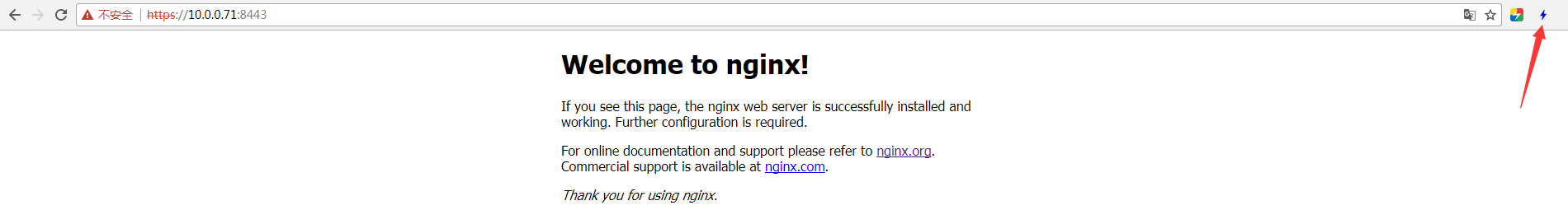
- 使用Chrome访问启用http2的站点,比如Jackie的环境为https://10.0.0.71:8443。
- 新开TAB页,在地址栏中输入
chrome://net-internals/#http2,检查HTTP/2 sessions下的表格。
- 确认表格里是否出现了上一步访问的主机地址,比如10.0.0.71:8443。
- 使用curl命令,参考HTTP/2 with curl,执行如下命令,确认站点返回的协议是否为HTTP
curl --http2 -I 10.0.0.71:8443 - 如执行上述命令时遇到如下错误,说明系统当前安装的curl还不支持HTTP2协议。
curl https://10.0.0.71:8443/ --http2 curl: (1) Unsupported protocol - 可以执行如下命令,检查系统当前安装的curl支持的特性列表,确认是否包含HTTP2。
curl -V curl 7.47.0 (i686-pc-linux-gnu) libcurl/7.47.0 GnuTLS/3.4.10 zlib/1.2.8 libidn/1.32 librtmp/2.3 Protocols: dict file ftp ftps gopher http https imap imaps ldap ldaps pop3 pop3s rtmp rtsp smb smbs smtp smtps telnet tftp Features: AsynchDNS IDN IPv6 Largefile GSS-API Kerberos SPNEGO NTLM NTLM_WB SSL libz TLS-SRP UnixSockets - 从前述输出信息可以了解到,当前安装的curl还不支持HTTP2。
- 这时可参考如何启用curl命令HTTP2支持重新编译curl,加入HTTP2的支持。
- 安装Chrome插件HTTP/2 and SPDY indicator,安装完毕后访问启用HTTP2的站点,如果地址栏出现蓝色的闪电,说明站点已启用HTTP2。
add_header 'Access-Control-Allow-Origin' '*';
add_header 'Access-Control-Allow-Methods' 'POST,GET,OPTIONS';
add_header 'Access-Control-Allow-Headers' 'application/json,X-Requested-With,Content-Type,Accept';
