bandit官网为:https://overthewire.org/wargames/bandit
0-10
0
直接给我们提示了用户名和密码是bandit0
直接使用命令登陆:
ssh -p 2220 bandit0@bandit.labs.overthewire.org
输入密码bandit0登陆成功(密码输入是没有回显的)
ls看到一个readme文件,里面保存着下一级的登陆密码
cat readme
得到下一级的登陆密码:boJ9jbbUNNfktd78OOpsqOltutMc3MY1
1
ssh -p 2220 bandit1@bandit.labs.overthewire.org
ls
看到一个-命名的特殊字符文件
cat -不能直接获得其中内容,会被当做其他命令来解释,回显你输入的内容,可ctrl+d停止
cat ./-即可读取文件中的内容,由此得到下一级的登陆密码:
CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9
2
ssh -p 2220 bandit2@bandit.labs.overthewire.org
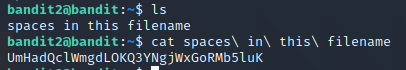
直接cat space,使用tab键补全,得到下级密码:
UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK
如图所示:
3
ssh -p 2220 bandit3@bandit.labs.overthewire.org
可以看到有一个inhere的文件夹
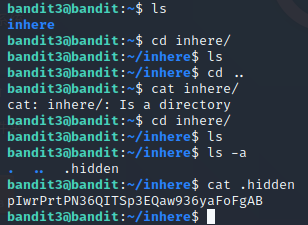
进去后ls查看发现是空的,
于是使用ls -a查看隐藏文件
cat .hidden得到下级密码:
pIwrPrtPN36QITSp3EQaw936yaFoFgAB
4
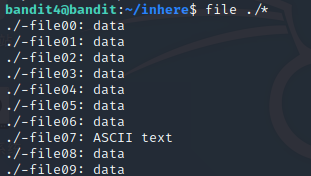
file ./*
使用file命令查看文件类型
cat ./-file07
获得下一级密码:
koReBOKuIDDepwhWk7jZC0RTdopnAYKh
如图:
5
ssh -p 2220 bandit5@bandit.labs.overthewire.org
发现有许多文件夹
find -type f -size 1033c
查找出来:
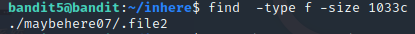
f:一般文档
c:是指字节
找到密码:DXjZPULLxYr17uwoI01bNLQbtFemEgo7
6
ssh -p 2220 bandit6@bandit.labs.overthewire.org
根据提示:
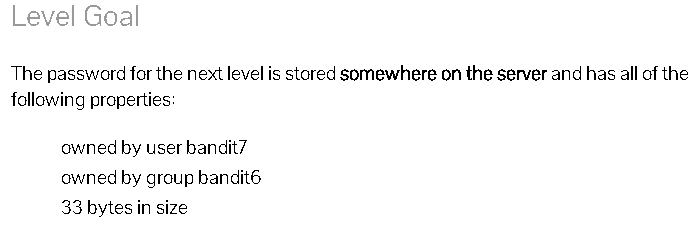
find / -size 33c -user bandit7 -group bandit6 2>/dev/null
2>/dev/null过滤扫描根目录下文件因权限不足而报错的信息
得到下级密码:
HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs
如图:
7
ssh -p 2220 bandit7@bandit.labs.overthewire.org
根据提示,使用grep
cat data.txt|grep millionth
如图:
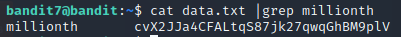
密码为:cvX2JJa4CFALtqS87jk27qwqGhBM9plV
8
ssh -p 2220 bandit8@bandit.labs.overthewire.org
sort data.txt|uniq -u
如图:
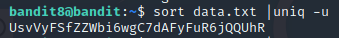
sort排序,
uniq命令:
-i 忽略大小写
-c 计数
-u 只显示唯一的行
下级密码为:UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR
9
ssh -p 2220 bandit9@bandit.labs.overthewire.org
strings data.txt查看里面的字符串
得到下级密码:truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk
10
ssh -p 2220 bandit10@bandit.labs.overthewire.org
base64解密,base64 -d data.txt
下级密码:IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR
11-20
11
ssh -p 2220 bandit11@bandit.labs.overthewire.org
题意为按顺序旋转了13位,及前半段和后半段的字母位置置换了
tr命令 后面接两个字符串,第一个查询,第二个置换
cat data.txt |tr 'a-zA-Z' 'n-za-mN-ZA-M'
同理:cat data.txt |tr 'a-zA-Z' 'a-mn-zA-MN-Z'也是一样的效果
下级密码为:5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu
12
ssh -p 2220 bandit12@bandit.labs.overthewire.org
有点绕,不过我们还是可以一步步根据命令提示来
xxd -r将16进制转化为2进制
下面包含大量tar,bz2,gz的解压操作,具体详细参数的解释此处不做解释
只是看起来繁杂,希望各位读者别被吓着了,多敲敲也就熟悉了
由于在当前目录下权限不足,我们转移到题目提示的工作目录/tmp下面,全部命令如下,如有不理解的请自行百度查看相关参数
bandit12@bandit:~$ mkdir /tmp/ss
bandit12@bandit:~$ cp data.txt /tmp/ss
bandit12@bandit:~$ cd /tmp/ss
bandit12@bandit:/tmp/ss$ file data.txt
data.txt: ASCII text
bandit12@bandit:/tmp/ss$ xxd -r data.txt >data.bin
bandit12@bandit:/tmp/ss$ file data.bin
data.bin: gzip compressed data, was "data2.bin", last modified: Thu May 7 18:14:30 2020, max compression, from Unix
bandit12@bandit:/tmp/ss$ mv data.bin data.gz
bandit12@bandit:/tmp/ss$ gzip -d data.gz
bandit12@bandit:/tmp/ss$ ls
data data.txt
bandit12@bandit:/tmp/ss$ file data
data: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/ss$ bunzip2 -d data
bunzip2: Can't guess original name for data -- using data.out
bandit12@bandit:/tmp/ss$ ls
data.out data.txt
bandit12@bandit:/tmp/ss$ bunzip2 -d data.out
bunzip2: Can't guess original name for data.out -- using data.out.out
bunzip2: data.out is not a bzip2 file.
bandit12@bandit:/tmp/ss$ ls
data.out data.txt
bandit12@bandit:/tmp/ss$ mv data.out data
bandit12@bandit:/tmp/ss$ mv data data.bz2
bandit12@bandit:/tmp/ss$ bunzip2 -d data.bz2
bunzip2: data.bz2 is not a bzip2 file.
bandit12@bandit:/tmp/ss$ ls
data.bz2 data.txt
bandit12@bandit:/tmp/ss$ mv data.bz2 data
bandit12@bandit:/tmp/ss$ mv data data.bz
bandit12@bandit:/tmp/ss$ bunzip2 -d data.bz
bunzip2: data.bz is not a bzip2 file.
bandit12@bandit:/tmp/ss$ mv data.
data.bz data.txt
bandit12@bandit:/tmp/ss$ mv data.bz data
bandit12@bandit:/tmp/ss$ file data
data: gzip compressed data, was "data4.bin", last modified: Thu May 7 18:14:30 2020, max compression, from Unix
bandit12@bandit:/tmp/ss$ ls
data data.txt
bandit12@bandit:/tmp/ss$ ls
data data.txt
bandit12@bandit:/tmp/ss$ rm -rf data
bandit12@bandit:/tmp/ss$ ls
data.txt
bandit12@bandit:/tmp/ss$ xxd -r data.txt >data.bin
bandit12@bandit:/tmp/ss$ ls
data.bin data.txt
bandit12@bandit:/tmp/ss$ rm -rf data.bin
bandit12@bandit:/tmp/ss$ ls
data.txt
bandit12@bandit:/tmp/ss$ file data.txt
data.txt: ASCII text
bandit12@bandit:/tmp/ss$ xxd -r data.txt >data.bin
bandit12@bandit:/tmp/ss$ file data.bin
data.bin: gzip compressed data, was "data2.bin", last modified: Thu May 7 18:14:30 2020, max compression, from Unix
bandit12@bandit:/tmp/ss$ mv data.bin data.gz
bandit12@bandit:/tmp/ss$ gzip -d data.gz
bandit12@bandit:/tmp/ss$ file data
data: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/ss$ mv data data.bz2
bandit12@bandit:/tmp/ss$ bunzip2 -d data.bz2
bandit12@bandit:/tmp/ss$ ls
data data.txt
bandit12@bandit:/tmp/ss$ file data
data: gzip compressed data, was "data4.bin", last modified: Thu May 7 18:14:30 2020, max compression, from Unix
bandit12@bandit:/tmp/ss$ mv data data.gz
bandit12@bandit:/tmp/ss$ gzip -d data.gz
bandit12@bandit:/tmp/ss$ ls
data data.txt
bandit12@bandit:/tmp/ss$ file data
data: POSIX tar archive (GNU)
bandit12@bandit:/tmp/ss$ mv data data.tar
bandit12@bandit:/tmp/ss$ tar xvf data.tar
data5.bin
bandit12@bandit:/tmp/ss$ file data5.bin
data5.bin: POSIX tar archive (GNU)
bandit12@bandit:/tmp/ss$ mv data5.bin data5.tar
bandit12@bandit:/tmp/ss$ tar xvf data5.tar
data6.bin
bandit12@bandit:/tmp/ss$ file data6.bin
data6.bin: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/ss$ mv data6.bin data6.bz2
bandit12@bandit:/tmp/ss$ bunzip2 -d data6.bz2
bandit12@bandit:/tmp/ss$ ls
data5.tar data6 data.tar data.txt
bandit12@bandit:/tmp/ss$ file data6
data6: POSIX tar archive (GNU)
bandit12@bandit:/tmp/ss$ mv data6 data6.tar
bandit12@bandit:/tmp/ss$ tar xvf data6.tar
data8.bin
bandit12@bandit:/tmp/ss$ file data8.bin
data8.bin: gzip compressed data, was "data9.bin", last modified: Thu May 7 18:14:30 2020, max compression, from Unix
bandit12@bandit:/tmp/ss$ mv data8.bin data8.gz
bandit12@bandit:/tmp/ss$ gzip -d data8.gz
bandit12@bandit:/tmp/ss$ ls
data5.tar data6.tar data8 data.tar data.txt
bandit12@bandit:/tmp/ss$ file data8
data8: ASCII text
bandit12@bandit:/tmp/ss$ cat data8
The password is 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL
得到下级密码为:8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL
ssh -p 2220 bandit12@bandit.labs.overthewire.org
13
ssh -p 2220 bandit13@bandit.labs.overthewire.org
这一关告诉我们密码存放/etc/bandit_pass/bandit14里,要使用密钥文件连接ssh,bandit14登陆
ssh -i sshkey.private bandit@127.0.0.1
cat /etc/bandit_pass/bandit14
得到下级密码:
4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e
14
ssh -p 2220 bandit14@bandit.labs.overthewire.org
bandit14@bandit:~$ telnet localhost 30000
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
Wrong! Please enter the correct current password
Connection closed by foreign host.
bandit14@bandit:~$ telnet localhost 30000
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e
Correct!
BfMYroe26WYalil77FoDi9qh59eK5xNr
Connection closed by foreign host.
得到下级密码:BfMYroe26WYalil77FoDi9qh59eK5xNr
15
ssh -p 2220 bandit15@bandit.labs.overthewire.org
使用ssl连接:
openssl s_client -connect localhost:30001
下级密码:cluFn7wTiGryunymYOu4RcffSxQluehd
16
ssh -p 2220 bandit16@bandit.labs.overthewire.org
nmap -sV查找主机版本服务号
nmap -sV localhost -p 31000-32000
扫描出有两个端口31518和31790
按照一般套路,前一个端口都是用来浪费你时间的,我们直接去尝试31790这个端口
openssl s_client -connect localhost -port 31790
得到一串ssh密钥:
MIIEogIBAAKCAQEAvmOkuifmMg6HL2YPIOjon6iWfbp7c3jx34YkYWqUH57SUdyJ
imZzeyGC0gtZPGujUSxiJSWI/oTqexh+cAMTSMlOJf7+BrJObArnxd9Y7YT2bRPQ
Ja6Lzb558YW3FZl87ORiO+rW4LCDCNd2lUvLE/GL2GWyuKN0K5iCd5TbtJzEkQTu
DSt2mcNn4rhAL+JFr56o4T6z8WWAW18BR6yGrMq7Q/kALHYW3OekePQAzL0VUYbW
JGTi65CxbCnzc/w4+mqQyvmzpWtMAzJTzAzQxNbkR2MBGySxDLrjg0LWN6sK7wNX
x0YVztz/zbIkPjfkU1jHS+9EbVNj+D1XFOJuaQIDAQABAoIBABagpxpM1aoLWfvD
KHcj10nqcoBc4oE11aFYQwik7xfW+24pRNuDE6SFthOar69jp5RlLwD1NhPx3iBl
J9nOM8OJ0VToum43UOS8YxF8WwhXriYGnc1sskbwpXOUDc9uX4+UESzH22P29ovd
d8WErY0gPxun8pbJLmxkAtWNhpMvfe0050vk9TL5wqbu9AlbssgTcCXkMQnPw9nC
YNN6DDP2lbcBrvgT9YCNL6C+ZKufD52yOQ9qOkwFTEQpjtF4uNtJom+asvlpmS8A
vLY9r60wYSvmZhNqBUrj7lyCtXMIu1kkd4w7F77k+DjHoAXyxcUp1DGL51sOmama
+TOWWgECgYEA8JtPxP0GRJ+IQkX262jM3dEIkza8ky5moIwUqYdsx0NxHgRRhORT
8c8hAuRBb2G82so8vUHk/fur85OEfc9TncnCY2crpoqsghifKLxrLgtT+qDpfZnx
SatLdt8GfQ85yA7hnWWJ2MxF3NaeSDm75Lsm+tBbAiyc9P2jGRNtMSkCgYEAypHd
HCctNi/FwjulhttFx/rHYKhLidZDFYeiE/v45bN4yFm8x7R/b0iE7KaszX+Exdvt
SghaTdcG0Knyw1bpJVyusavPzpaJMjdJ6tcFhVAbAjm7enCIvGCSx+X3l5SiWg0A
R57hJglezIiVjv3aGwHwvlZvtszK6zV6oXFAu0ECgYAbjo46T4hyP5tJi93V5HDi
Ttiek7xRVxUl+iU7rWkGAXFpMLFteQEsRr7PJ/lemmEY5eTDAFMLy9FL2m9oQWCg
R8VdwSk8r9FGLS+9aKcV5PI/WEKlwgXinB3OhYimtiG2Cg5JCqIZFHxD6MjEGOiu
L8ktHMPvodBwNsSBULpG0QKBgBAplTfC1HOnWiMGOU3KPwYWt0O6CdTkmJOmL8Ni
blh9elyZ9FsGxsgtRBXRsqXuz7wtsQAgLHxbdLq/ZJQ7YfzOKU4ZxEnabvXnvWkU
YOdjHdSOoKvDQNWu6ucyLRAWFuISeXw9a/9p7ftpxm0TSgyvmfLF2MIAEwyzRqaM
77pBAoGAMmjmIJdjp+Ez8duyn3ieo36yrttF5NSsJLAbxFpdlc1gvtGCWW+9Cq0b
dxviW8+TFVEBl1O4f7HVm6EpTscdDxU+bCXWkfjuRb7Dy9GOtt9JPsX8MBTakzh3
vBgsyi/sN3RqRBcGU40fOoZyfAMT8s1m/uYv52O6IgeuZ/ujbjY=
生成密钥文件,使用bandit17进行连接
chmod 600 a.priv
ssh -i a.priv bandit17@localhost
不知道为什么提示还要输入passphrase和password,还有点问题,我看了几篇博客,关于此关也写的不是很详细,希望大家指正
参考别人博客还是给出下级密码:xLYVMN9WE5zQ5vHacb0sZEVqbrp7nBTn
17
ssh -p 2220 bandit17@bandit.labs.overthewire.org
ls查看有password.new和password.old两个文件
cat命令分别查看,发现许多相同的行,
diff password.new password.old找出不同行
密码为:kfBf3eYk5BPBRzwjqutbbfE887SVc5Yd
18
ssh -p 2220 bandit18@bandit.labs.overthewire.org
都遇到byebye了,题意说.bashrc文件被修改了,当我们登陆进去的时候就会登出
但是还是可以执行命令的
如:
ssh -p 2220 bandit18@bandit.labs.overthewire.org cat ./readme
输入密码,获得下级密码:
IueksS7Ubh8G3DCwVzrTd8rAVOwq3M5x
19
ssh -p 2220 bandit19@bandit.labs.overthewire.org
ls -l查看:
-rwsr-x--- 1 bandit20 bandit19 7296 May 7 20:14 bandit20-do
(文件显示为红色,表示为压缩文件或包文件,七列从左往右分别是,权限、文件数、归属用户、归属群组、文件大小、创建日期、文件名称)
简单了解ruid和euid:ruid谁执行就是谁,euid是判断到底用什么权限执行
s位表示,任意用户执行此文件时,都以所有者的身份去执行(若为大S则表示文件未被赋予执行权限)
所有者是bandit20
./bandit20-do cat /etc/bandit_pass/bandit20
下级密码为:GbKksEFF4yrVs6il55v6gwY5aVje5f0j
20
ssh -p 2220 bandit20@bandit.labs.overthewire.org
nc侦听命令
nc -lv < /etc/bandit_pass/bandit20 &
-l 指定nc处于侦听模式
-v 输出详细信息
& 放在命令后面表示,此进程为后台进程,有时进程把shell占了,又没有交互,所以我们希望它在后台执行即可
然后利用soconnect这个文件访问端口获取密码
./suconnect [port]
完整操作如下:
bandit20@bandit:~$ nc -lv < /etc/bandit_pass/bandit20 &
[1] 6617
bandit20@bandit:~$ listening on [any] 36263 ...
bandit20@bandit:~$ ./suconnect 36263
connect to [127.0.0.1] from localhost [127.0.0.1] 42488
Read: GbKksEFF4yrVs6il55v6gwY5aVje5f0j
Password matches, sending next password
gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGr
bandit20@bandit:~$
下级密码为:gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGr
21-30
21
ssh -p 2220 bandit21@bandit.labs.overthewire.org
根据题目提示:cd /etc/cron.d
关于cron(crontab)我们只需要了解它是一个闹钟即可,就像人定闹钟,到点了人就该去洗漱,吃饭之类的,
完整操作如下:
bandit21@bandit:~$ cd /etc/cron.d/
bandit21@bandit:/etc/cron.d$ ls
cronjob_bandit15_root cronjob_bandit22 cronjob_bandit24
cronjob_bandit17_root cronjob_bandit23 cronjob_bandit25_root
bandit21@bandit:/etc/cron.d$ vim cronjob_bandit22
bandit21@bandit:/etc/cron.d$ cat cronjob_bandit22
@reboot bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
* * * * * bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
bandit21@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit22.sh
#!/bin/bash
chmod 644 /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
cat /etc/bandit_pass/bandit22 > /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
bandit21@bandit:/etc/cron.d$ cat /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI
cronjob_bandit22是一个闹钟
前五个号是定时参数,表示任意可能的值,即每分钟都执行一次/usr/bin/cronjob_bandit22.sh脚本,
该脚本则是将密码写入到/tmp目录下
>/dev/null表示将脚本输出的一些报错或者显示信息输出到虚空
(cat /etc/bandit_pass/bandit22提示权限不够 )
得到下级密码:Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI
22
ssh -p 2220 bandit22@bandit.labs.overthewire.org
根据题目提示再次进入 /etc/cron.d/目录
查看cronjob_bandit23
继续跟进查看脚本
发现是将密码放在I am user bandit23的md5之和的值的文件
操作如下:
bandit22@bandit:~$ ls /etc/cron.d/ //根据题目我们查看运行的周期任务
cronjob_bandit15_root cronjob_bandit22 cronjob_bandit24
cronjob_bandit17_root cronjob_bandit23 cronjob_bandit25_root
bandit22@bandit:~$ cat /etc/cron.d/cronjob_bandit22 //查看本关的bandit22内容
@reboot bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
* * * * * bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
bandit22@bandit:~$ cat /usr/bin/cronjob_bandit22.sh //查看对应的脚本文件
#!/bin/bash
chmod 644 /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
cat /etc/bandit_pass/bandit22 > /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv //由此可知,将密码写到了/tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv中
bandit22@bandit:~$ cat /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI
得到密码如下:
Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI
23
不知道为什么使用上关得到的密码登不上,不过没有影响,我们可以用上关的账号进行查看
和上一题差不多,查看任务,读取对应脚本文件
操作如下:
bandit22@bandit:~$ cat /etc/cron.d/cronjob_bandit23
@reboot bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
* * * * * bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
bandit22@bandit:~$ cat /usr/bin/cronjob_bandit23.sh
#!/bin/bash
myname=$(whoami)
mytarget=$(echo I am user $myname | md5sum | cut -d ' ' -f 1)
echo "Copying passwordfile /etc/bandit_pass/$myname to /tmp/$mytarget"
cat /etc/bandit_pass/$myname > /tmp/$mytarget
这里需要我们了解shell脚本的一些东西,$表示变量,将$myname换成bandit23执行一下:
echo I am user bandit23 | md5sum | cut -d ' ' -f 1
得到bandit24的密码:
8ca319486bfbbc3663ea0fbe81326349